Top 3 Products & Services
| 1. 2. 3. |
Dated: May. 07, 2010
Related Categories
Network+ CertificationNetworking In General
Network Topologies
Ever wonder... how are all of these file, print, fax, and computer resources connected so as to allow the typical desktop computer to access them? Network topology refers to the way networked computers and network resources are connected. The three most widely used topologies are bus, ring, and star. Note that the following network topology diagrams are logical views of the topologies they represent and don’t necessarily match the physical (electrical) interconnections on the networks.
Bus Network
The bus network topology, connects each computer to a single cable. At each end of the cable is a terminating resistor or a terminator. An electrical signal is passed back and forth along the cable past the computers and between the two terminators. The bus carries a message from one end of the network to the other. As the bus passes each computer, the computer checks the destination address on the message. If the address in the message matches the computer’s address, the computer receives the message. If the address doesn’t match, the bus carries the message to the next computer, and so on.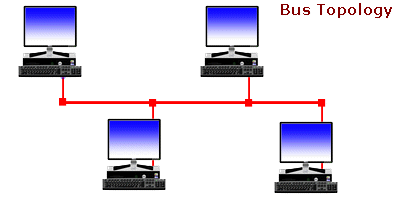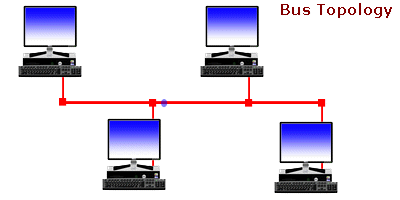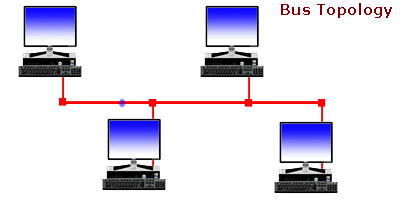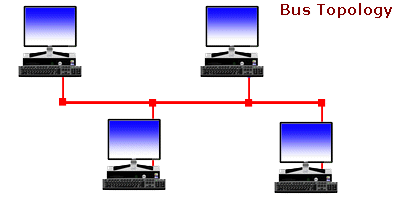
Bus topology is passive, meaning that computers only listen for data being sent on the network and aren’t responsible for moving data from one computer to the next. If one computer fails, it doesn’t affect the entire LAN. On the other hand, if a cable breaks, the entire cable segment (the length between the two terminators) loses its connectivity, so that the entire segment isn’t functional until the cable can be repaired. Each computer attached to a bus network can transmit data whenever it “wants.” This capability means that two computers may try to transmit simultaneously. This occurrence is called a collision. A collision is detected by the network hardware of the sending computers. When a collision is detected, the packets of data that generated the collision are retransmitted.
The limitation of bus networks is the speed of data transmission relative to the number of computers on the network. As more computers are added to the network, more collisions are bound to happen. As more collisions occur, more retransmissions take place and the overall network performance degrades.
Ethernet is one example of a common bus network found on many local area networks. Ethernet is also the most popular LAN architecture in use today.
Ethernet networks can be wired with different types of cable, each with its own benefits and drawbacks. Three popular specifications for Ethernet topologies are 10BASE2, which uses thin coaxial cable (Thinnet) that can carry a signal up to approximately 607 feet; 10BASE5, which uses Thicknet cabling that can carry a signal for about 1,640 feet; and 10BASET, which uses unshielded twisted-pair cable that can carry a message for about 328 feet between a computer and the hub to which the computer is connected.
Note: Ethernet was developed by the Xerox Corporation in 1972 as the follow-up to some research done at the University of Hawaii. Ethernet first became commercially available in 1975 as a 2.94 Mbps network able to connect up to 100 computers spread over a 1-kilometer cable. Xerox Ethernet soon became popular, and work was done with the Intel Corporation and Digital Equipment Corporation to extend Ethernet’s capability to 10 Mbps. Today, 100 Mbps Ethernet is gaining in popularity.
Ring Network
In a ring network, a packet of data (often called a token) is continually moving around the ring from one computer to the next. To send data, a computer on the network must wait for the circulating token to pass by. When the token arrives, it’s examined to see whether it’s empty. If it’s empty, the computer that wishes to transmit adds its data to the token packet and addresses the packet to a destination. As the token passes by the destination computer, the computer looks at the address and because the message is addressed to itself, extracts the data, and replaces the token packet’s data with a delivery acknowledgment message. The token then continues to circle the ring and eventually returns to the sending computer. The sending computer examines the token packet to see if it contains the data it sent or an acknowledgment message. If it doesn’t find an acknowledgment message, the sender knows that the data wasn’t received, possibly because the destination computer wasn’t operating.
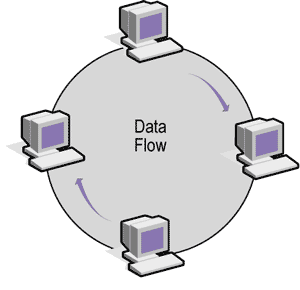 The sender then clears the token packet and passes it along the ring to allow subsequent computers their chance to use the network’s communication resources. The token passing scheme is in contrast to the bus topology whereby any computer can send at any moment and the protocol must detect collisions. Collisions of this nature can’t occur on a ring network.
The sender then clears the token packet and passes it along the ring to allow subsequent computers their chance to use the network’s communication resources. The token passing scheme is in contrast to the bus topology whereby any computer can send at any moment and the protocol must detect collisions. Collisions of this nature can’t occur on a ring network.
Data on the IBM token-ring network is transmitted at either 4 or 16 Mbps, depending on the actual implementation. For computers to communicate with each other, all network cards must be configured similarly to communicate at either 4 or 16 Mbps on the network. Networked computers are connected by shielded and/or unshielded twistedpair cable to a wiring concentrator called a Media Access Unit or MAU (rhymes with cow). Each MAU can support as many as 72 computers that use unshielded wire or up to 260 computers using shielded wire. Each ring can have as many as 33 MAUs allowing for a theoretical maximum of 8,580 computers on the network.
Note: The first design of a network passing a token ring is attributed to E. E. Newhall in 1969. IBM first publicly supported a token-ring topology in March 1982, and announced its first token-ring network product in 1984.
Star Network
To transmit data between any two computers in a star network, requires that data be sent via the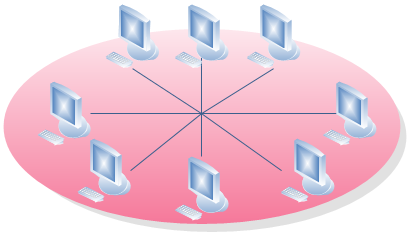 centrally located computer, called a hub. The hub provides a common connection so that all the computers can communicate with one another. To extend the star network, hubs can be connected to one another. The major problem with star networks is that if the centrally located hub isn’t operating, the entire network becomes unusable. A benefit of a star network is that no computer, other than the centrally located hub, can interrupt network traffic.
centrally located computer, called a hub. The hub provides a common connection so that all the computers can communicate with one another. To extend the star network, hubs can be connected to one another. The major problem with star networks is that if the centrally located hub isn’t operating, the entire network becomes unusable. A benefit of a star network is that no computer, other than the centrally located hub, can interrupt network traffic.
Internetworking
The previous section detailed different network topologies. This section will show that these disparate networks can be interconnected and may even be separated by thousands of miles. This scenario is called internetworking. Figure 1.9 shows a well connected network composed of a bus network, a ring network, a satellite connection to a remote server, and a dial-up modem connection. Notice the device called the Gateway. This device is used to connect the bus network to the ring network. Its job isn’t only to bridge the two networks hardware-wise but also to route data between the two when the destination of a data packet isn’t local to either the bus or ring network. In this network, the laptop computer has the same access to resources connected to the bus network’s Workstation computer as does the bus network’s Macintosh computer. Of course the access times may not be the same for the laptop computer and the Macintosh.
Does Network Topology Matter?
Fortunately, the average application programmer has little need to know the topology details of the network his software will run on. Most of these details are hidden fromthe application program by a networking application programming interface (such as WinSock). The application programmer will need to be concerned with these nittygritty details if the application being developed has any special requirements, such as fault tolerance or guaranteed response times. The programmer may also be concerned about the underlying network hardware. Ethernet was listed earlier as an example of a bus network. Some networks may not be as simple as Figure 1.6 appears. As several local area networks are interconnected, and as wide area network links, such as those provided by satellites, are added, network topology becomes an issue with the network application programmer. You can’t assume that data will reach its destination in less than 100 milliseconds, for example. The best advice is to make your network programs as configurable and robust as possible, especially with regard to time-out values.
Look at an example of a network configuration that requires flexible network applications. If the server is acting as a database server, it must serve the client computers on the bus network, the ring network, and the telephone line. The network access times are different for the Macintosh on the bus network than they are for the laptop computer dialed with a 9,600-baud modem, for example.
The application programmer should make the server aware of the disparity in performance when it communicates with the many other computers it serves. Those other computers must likewise be knowledgeable about their connectivity to the server. The client software running on the laptop computer may have a five-second time-out for database access while the bus network’s Macintosh may need a 10-second time-out to make up for the delays introduced by the satellite link. Attention to details such as this early in a network application’s development cycle may save a lot of aggravation later.
Now that you've gotten free know-how on this topic, try to grow your skills even faster with online video training. Then finally, put these skills to the test and make a name for yourself by offering these skills to others by becoming a freelancer. There are literally 2000+ new projects that are posted every single freakin' day, no lie!
 Previous Article |  Next Article |
Check Out: Charles Babbage - Father of Computing

