Top 3 Products & Services
| 1. 2. 3. |
Dated: Nov. 20, 2013
Related Categories
Networking In GeneralThe main idea of VPN networks is tunneling as it creates a logical network. It is a bit complicated so we won't explain it very thoroughly as you may need some greater knowledge to understand what is truly going on.
Types of VPN Tunneling
There are two kinds of tunneling that Virtual Private Networks support and they are called compulsory and voluntary. They are equally being used, as in none is more popular than the other.
When it comes to compulsory tunneling it is the network provider that deals with Virtual Private Network setting up. Here there is only one step, unlike voluntary which is coming up next.
When it comes to voluntary tunneling, there is a different approach. It is not the provider, but you who deals with setting up the connection. Here you will connect to the carrier network and after that the client app will make a tunnel to a Virtual Private Network server.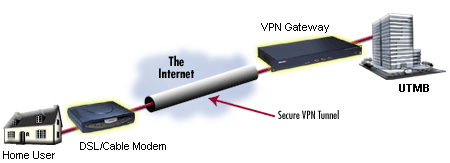
Compulsory tunneling works in a way that it will authenticate the clients and then assign them to a certain server. It does this by using logic, pretty complicated. The device it uses is usually called a FEP or Front End Processor. You may also hear the terms POS or NAS. This way of tunneling will not let you see the details of your connection to the VPN server and it will give control of the tunnels to the ISP.
VPN Tunneling Protocols
There are networking protocols that are created just for the sole purpose of using VPN tunnels. They are called:
Layer Two Tunneling Protocol (L2TP)
This protocol was most commonly used in all devices made by Cisco. This protocol exists in a way of a data link layer, the second layer to be more precise, of the OSI model. It is called Layer two tunneling because of that, obviously.
Point-to-Point Tunneling Protocol (PPTP)
This was the first one to be created and there were some major companies that took part in it's birth. It is most commonly found in Windows. It is not very secure, but it is not abandoned so consider it being worked on.
Internet Protocol Security (IPsec)
This one is interesting as it is not a single protocol, but rather multiple protocols connected together. It is in the third layer of the OSI model.
Note that these protocols are usually not compatible with each other.
You can create your own VPN tunnel on this Website And you want to, you can check out the most common error codes in VPN's in our article here Common VPN error codes.
Now that you've gotten free know-how on this topic, try to grow your skills even faster with online video training. Then finally, put these skills to the test and make a name for yourself by offering these skills to others by becoming a freelancer. There are literally 2000+ new projects that are posted every single freakin' day, no lie!
 Previous Article |  Next Article |
