Other Technologies
Influence of Worldwide Software Piracy -

Information from a research that the research company IDC conducted for the Business Software Alliance (BSA) show that
36% of bought software in 2006. is pirate software.
In a research IDC has analyzed the use of software in a 102 different countries across the world and it is estimated that the software that was installed on all computers in these countries was worth 105 billion dollars, and that the sale of legal software has risen for about 9 percent.

How to Stay Safe From Android Spyware -

The words "free" and "app" can often bring to the fore the greedy kid inside the individuals from the tech savvy brigade - people like yourself for example. Even so, when the aforementioned pair of words combines you just can't help hankering after this technological treat - of course much to the detriment of your smart phone in numerous cases. Mobile phone spy software can ensure that your cell phone goes kaput and hence it is extremely important that you steer clear of the spyware for your Android phone. Here's how you can do it...
Leaping Ahead in WiFi Standard - 802.11ac -

We all know that we need more bandwidth now, than we ever did in the past. There tons more online games, online movies, online collab work, you name it. And the past standards of Wifi namely 802.11a, 802.11b, 802.11g, 802.11n, and so on) were getting better and better; however, the 802.11ac does the trick. Well, atleast for now it is, until something better comes along.
Understanding DNS Servers -

Domain Name System or DNS servers are dedicated computers that have network operating systems installed on them and are responsible for resolving hostnames (computer names) to their IP addresses and vice versa. DNS servers are used worldwide and are helpful while accessing the Internet and visiting websites. Every Internet Service Provider or ISP has its own DNS server which receives name resolution requests from the subscribers of that ISP and resolves the requested host names to their corresponding IP addresses.

Understanding Mesh Topology -

Apart from star topology that is widely used in almost every network environment, the other type of topology that is complex while setting up but provides 100% fault tolerance to the network is Mesh Topology. In this topology, every computer that has to be connected to the network is connected to every computer that is available in the network. For example if there are four computers namely A, B, C and D, then A will be connected to B, C and D. Likewise B will be connected to A, C and D and so on. This means that when mesh topology is used while establishing a network setup, it is very unlikely that the network would ever face congestions or would ever fail.
Wireless Network Security -

Ever wonder if it's a good idea to switch your home LAN to wireless? This is a very easy to understand discussion about the security matters involved.
Most Common Problems With Computer Networks -
 In many homes, the network can't easily reach all areas a person needs.
In many homes, the network can't easily reach all areas a person needs. This fact surprises many people. Stringing network cables to some rooms may prove impractical, of course. But even in wireless networks, "cold spots" where the Wi - Fi radio signals will not reach the corner of the bedroom, study or porches are also common. Be prepared that there is some planing needed in network installation.
More Physical Network Devices -
 FIREWALL
FIREWALL - By its function it is an expanded capabilities gateway. Expansion refers primarily to prevent unauthorized access to the network in general. Aforementioned means that the network device provides control of traffic between the Internet and a local network in a way that all incoming Internet traffic is filtered according to defined filtering rules.
Types of Servers 2 -

One of most important type of server is cluster servers. Software that enables clustering of servers is installed into a computer. Clustering servers also serve as load balancing servers between two computers. This is a common small business server. Clustering servers are used to avoid server failover. Server failover is the capability to shift to another standby server if the main server fails.
Secure Your Internet Live Conferencing -

Okay, this article to some people maybe a bit boring because there is a bit of SILC information overload. But if you are remotely interested in reading about security measures taken to tighten security gaps in chat programs, this is the article for you.
Information Warfare: A New Kind of War -

Ever wonder why CNN keeps talking about technology when it comes to recent news of terrorism? Well thats because our biggest resource is "information" and its "specific distribution". Read all about what our threats, weaknesses, and how we are preparing for countering these threats.

Computer Training Excuses -

You wouldn't go to a doctor who had never been to medical school, or hire a lawyer who never studied law. One side-effect of a world advancing as rapidly as ours is that fields are becoming more and more specialized and narrow. People can no longer get by on general knowledge in their careers, something I found out for myself not too long ago. I'd been out of high school for two years, scraping by on my own and picking up scraps of programming as I went. I saw all of the self-taught programmers breaking into the IT industry, and I hoped to do the same. After all, IT is one of the few industries out there where being creative and a quick learner is more important than a degree.

Understanding LAN Bridges -

LAN Bridges were used to separate and isolate multiple collision domains from each other in large broadcast domains. Bridges had two or more LAN ports to which other central devices, such as network Hubs, were connected via LAN cables. Unlike network Hubs that used to forward data packets to every PC that was connected to the ports, Bridges acted more like LAN Switches to identify destination ports and transferred the data packets only if the packets were destined to reach the segments that were connected to their other ends. Bridges used to calculate and identify the destination segments on the basis of physical (MAC) addresses of the central devices that were connected to their LAN ports.

Network File Sharing Basics -

Microsoft Windows
(and other personal operating systems) contain a built-in file sharing system. For example, the Windows folder can be shared over a
local network (LAN) or
the Internet by using Explorer as well as network drive mappings. You are also able to set restrictions on access security in order to control who can get the shared files.

WiFi Security -

WiFi Security feature protects your network and gets quick access associated with Win2K, XP. It supports WEP or WPA and gives you real-time interloper alerts you from free blockers and you feel glad when there is no spyware and no adware in your network to spoil your files. Any users get access to the Internet by means of laptop, handhold games, smart cell phones and PDA. The most important thing is it tenders a trouble-free and cheap method to safe and sound your network connection at any hotspot all over the world. WiFi Security examines data and perceives entrance point in real time and identifies the user who wants to spoil your files.

Types of Attacks on Web Servers -

I think we hit the mother-load of server security information in this article people. We urge, every server admin as well as those looking to get into server and network security to not miss out on this article. You may already be experiencing attacks and wouldn't even know. And we like to point out that this article has no views against the "White-Hat Hacking Community."

Encrypt Folders in Windows XP/Vista/7 -
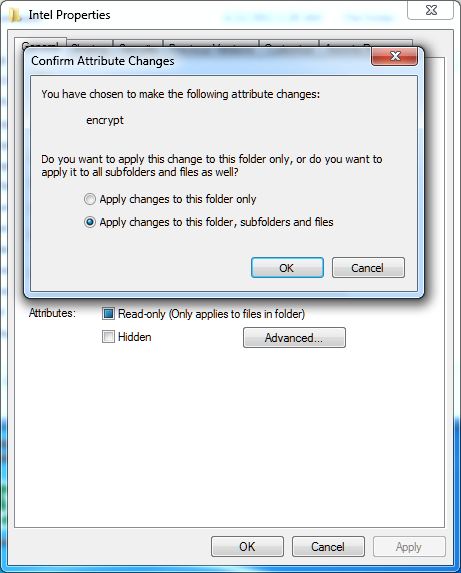
In production environments, where domain-based network infrastructure is established, administrators mostly prefer to use Public Key Infrastructure (PKI) in order to maintain the security of the sensitive information throughout the organization. In such cases Certificate Authority (CA) servers are configured and managed by the security administrators of the organizations. Internal Certificate Authority servers are mostly used when the encryption and decryption process has to take place within the organization only. Organizations that deal with external clients, such as online shopping sites, mostly rely on globally trusted third-party Certificate Authority services.

Understanding DNS Updates & DNS Records -

DNS records are the objects that are created either manually by the DNS administrators or automatically by the DNS servers themselves. A DNS server can have indefinite numbers of records and each DNS record is helpful in resolving the query of its own type. For example a Host (A) record in DNS server helps resolving a hostname to its corresponding IPv4 address whereas Host (AAAA) record resolves hostname to its corresponding IPv6 addresses.

Understanding Star Topology -

Since over a decade, star topologies have been preferred over bus topologies by the administrators. In star topology, a central device (Hub or Switch) is used to connect multiple PCs in a local area network. Central devices that are used in star topologies have multiple LAN ports integrated in them and the PCs are connected to the central devices via patch cables. In most cases patch cables are twisted pair cables that have four twisted pairs (eight wires in all) which are crimped to the RJ-45 connectors. The reason why star topology is mostly preferred nowadays is that it does not provide a single point of failure and is highly scalable. This means ...

Windows 7 - Users, Accounts, and UAC -

By now most Windows users are probably familiar with the notion of user accounts and how all users on a PC can have their own individual settings, documents, and other features. In
Windows Vista, Microsoft simplified the user account types down to just two, and locked them down to make the system more secure.
Windows 7 takes this approach a step further and makes it easier to configure how user accounts behave and are protected. And thanks to features such as User Account Control, Parental Controls, and Windows Live Family Safety, Windows 7 is not only more secure than
previous Windows versions, but also easier to configure from a user account perspective. This tutorial describes these features and explains how they can be put to the best possible use.

Types of Computer Crimes -

What types of computer crimes do you and your company have to look out for? How do you avoid these criminals? Because computers are found in just about every home and office now, criminals are becoming smarter.
What if the Internet Went Down? -

Modern metropolises can't function without computers and the Internet. Water supply and electricity, mobile and telecommunications - all function with the help of the Internet. What would happen if it terminated? If the computer network or a system server failed, that would lead to devastating consequences for people and the economy. According to some estimates Internet crime brings more profit than drug related crime. Threats from the virtual space can go much further than home computers or work place computers.

Phishing An Email Scam -

The type of email scam in which an email is sent claiming to be an established enterprise like eBay, Citibank, PayPal, Amazon.com, etc in an attempt to scam the user into surrendering private information. The word phishing comes from the analogy that Internet scammers are using e-mail lures to fish for passwords and financial data from the sea of Internet users. The term was coined in 1996 by hackers who were stealing AOL Internet accounts by scamming passwords from unsuspecting AOL users.
Add New Host (A) Record in W2K8R2 DNS Server -
%20Record.JPG)
In any network setup DNS server plays an important role as it helps client computers to resolve names to their respective IP addresses. When a DNS server is installed in a network it automatically creates a Forward Lookup Zone and adds some records in it by its own. A DNS server can have several record types depending on the type of network.
Kindness Online -

So I thought this morning I would try to be the optimist, and give reason to hope for the future of the Internet by drawing upon its present.
Now, it may seem like there is less hope today than there was before. People are less kind. There is less trust around. I don't know. As a simple example, we could run a test here. How many people have ever hitchhiked? I know. How many people have hitchhiked within the past 10 years? Right. So what has changed? It's not better public transportation. So that's one reason to think that we might be declensionists, going in the wrong direction.
Phishing -

Phishing is the act of sending out emails, supposedly from a certain trusted party, in order to trick out of the recipient sensitive information such as usernames, passwords, banking details etc. To avoid becoming a victim of phishing, stay alert. Whenever you receive an email telling you that you need to enter sensitive information treat it with suspicion.
Secure Privacy Using Your PC -

You can never be careful enough with the people that surround you and that may see something on your computer that they shouldn't. It probably happened to you that your boss suddenly enters your office and you are doing something you shouldn't. If you can, set your screen so it is available only to your eyes.
Security Tips -

The Internet is a useful place, but unfortunately it can also be quite dangerous. Just how do you know what is safe and what you should stay away from? This article gets right down to the point with some practical tips on avoiding a few tricks, so that you don't end up inconvenienced, annoyed, or devastated.
D-Link Cloud Router DIR-605L -
.png)
This time we had the chance to try out a product from the Chinese firm
D-Link, a renowned manufacturer of computer networking equipment. It is a product that is called
Cloud Router and is classified by the marking
DIR-605L. In the package, next to the router, you get a
voltage adapter (5V DC, 1A),
LAN cable,
CD with instructions and software, as well as printed documentation.
Precaution Is the Best Defense Against Viruses -

Now we have all heard of various ways to help our PC to avoid viruses. Well this is article is no exception. But it does point out a couple of things that you dont usually hear discussed.
Difference Between Adware & Spyware -

This is a good article to show you the differences between spyware and adware. Shows you what you can do to avoid them and protect yourself once infested. Adware is any computer program or software package in which advertisements or other marketing material are included with or automatically loaded by the software and displayed or played back after installation.

IP Spoofing and Sniffing -
 Sniffing and spoofing
Sniffing and spoofing are security threats that target the lower layers of the
networking infrastructure supporting applications that use the Internet. Users do not interact directly with these lower layers and are typically completely unaware that they exist. Without a deliberate consideration of these threats, it is impossible to build effective security into the higher levels. Sniffing is a passive
security attack in which a machine separate from the intended destination reads data on a network. The term
"sniffing" comes from the notion of
"sniffing the ether" in an
Ethernet network and is a bad pun on the two meanings of the word
"ether." Passive
security attack are those that do not alter the normal flow of data on a communication link or inject data into the link.
Spamming -
.jpg)
A brief intoduction into the world of Spamming. Read to find out the only methods known to work in fighting spam emails.
Analysis of Network Computer Monitoring Software -

The most popular application of computer monitoring software is on office networks in a business establishment, where each workstation is actively monitored to see how the employees spend their entire work day.
Business applications of computer monitoring software essentially draw its basic function from the principle that increasing the potential productivity could generate a more positive flow in business. In a sense, the computer monitoring software here is regarded as a "performance balancer", by keeping an eye on employees and making sure that they ...

Understading Networking Hubs -

Network hubs were the central devices that network administrators used to use to establish a network setup using Star Topologies. Network hubs had multiple RJ-45 ports integrated in them and were used to connect one end of the LAN cables that had RJ-45 connectors crimped to them. The other end of the cables were connected to the RJ-45 ports available on the PCs. Network hubs were available with 4, 8, 16 and 24 ports. Administrators also used to cascade two hubs for larger network setups. Cascading means that one RJ-45 port of one hub connected to ...
Privacy Alert! -

Spyware can be installed without the conscious consent of the user, allowing unsolicited spam or remote monitoring of a computer's activity. Neither spyware or adware can be removed using a normal Antivirus program.
Super Cookies and the Global Debate -

The concern and debate about the ethical issues of a third party tracking and
selling PC users online habits is not new in the
Internet age. Yet the debate on personal Internet privacy is dramatically heating up in 2010 and gaining worldwide attention from civic and governmental organizations around the globe. The impetus for renewed focus on standardized levels of
consumer online privacy is largely fueled by new technologies in
cookie tracking tools that is garnering a name for itself in some industry circles as "
super cookies."

Understanding Routers -

Routers are the devices that are used to connect two different networks in order to allow communication between them. Networks with different network IDs are considered to be different. By default, no communication can take place between two different networks, and this configuration prevents computers of one network from getting accessed by the computers on the other network, which may belong to another organization, building premises, home, etc.
Specify Users' Logon Time in Windows -
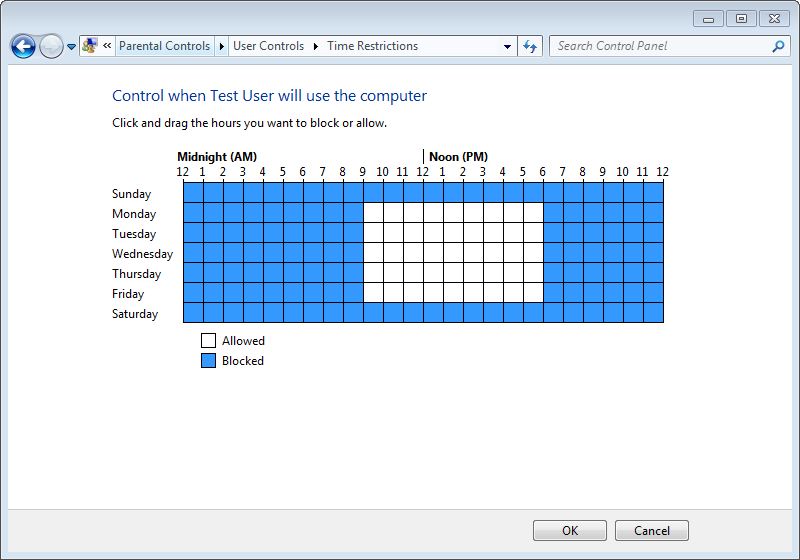
Logon time is the duration between which the operating system allows user accounts to logon to the computer. Logon time can be configured on the operating system only by the administrators of the computer. User accounts that belong to non-admin groups cannot modify or define the logon time and are only allowed to logon to the computer at the times specified for them by the administrators.
How to manage router passwords -
You should always change your routers default password. That is a must. It is because the
generic router passwords can be found all over the Internet. This information can be found by hackers and they could use it to break into your router and cause you a lot of problems.
Administrator Password Hack -
We've got so much email from so many NT Admins that it's almost unbelievable why we haven't come up with a tutorial for them. This tutorial is scrictly for those admins who make it a habit to forget passwords. Enjoy!
America Fought Back - The WORM! -

Foremost, this trick/tip assumes that when the virus tries to send it self out to everyone in the address book, the mail client will falter on the bogus address and the attempt to send will fail.
Torrent - Download Files from the Internet -

What eventually became one of the most significant advantages of the Internet is the possibility of simple access to any information placed on any computer attached to this global network. We can access the information that we need in various ways, from searching on the Web, to downloading complete files, even the ones that are pretty large. This text should help the enlightening of the dilemma about
downloading files from the Internet and to give you short instructions on how to do it.
Business networks -

As you see a business growing, it is normal that their layout of networks grows with them. Companies that are placed in a few locations will create internal connections that are called campus networks if their buildings are close to each other and use WAN networks if they are more distant.
Understanding Collision and Broadcast Domains -

In computer networks, scope (area) up to where data that is transferred over the cables or the wireless media with certain conditions is categorized in two domain main types. In complex network setups, because multiple segments are connected to each other via different types of central devices, it becomes important for the administrators to separate broadcast domains and reduce the numbers of collision domains. A central device in which collisions may occur is Hub because of it logical Bus Topology.
Why Programmers Love the Night -

One famous saying says that programmers are machines that turn caffeine from coffee and Coca Cola into a programming code. And if you
ask a programmer when does he like working the most and when is he most productive - he is probably going to say late at night or early in the morning, that is when he has the greatest energy and concentration to work.
SSL in Brief -

Here is something that no network or web developing professional should ignore. SSL is has already become the widely accepted. Read the full article to understand the intricacies and the nitty gritty of SSL. SSL comes in two strengths, 40-bit and 128-bit, which refer to the length of the "session key" generated by every encrypted transaction
Understanding DNS Zones -

When a DNS server role is installed on a network operating system, by default forward lookup zone is automatically created and the DNS server works as Caching Only server that caches the results of all the queries that it resolves. Forward lookup zone of a DNS server resolves IP addresses to their corresponding host names, is used in most network setups in production environments.
Living La Vida Wireless -

Do you often feel tethered to your home computer or other electronic devices? Tired of the endless cords to untangle under your office desk? Then it's time to go completely wireless! It's easier than ever to live a completely wireless lifestyle, thanks to innovations in the consumer and business electronics industries. Review some of the latest gadgets and services that will have you free-wheeling it in no time.
The best strategy to protect your computer -

A
VPN (virtual private network) gives you the possibility to encrypt every bit of traffic that goes through your network
(it doesn't matter if it is going in our out).
Cookies and Cream -

Cookies are so good. Especially those chocolate chip kinds are my favorite. But not all cookies are so sweet. The cookies we talk about on the web are subject of frustration for many surfers. Find out why many sites use still use them.
Denial Of Service -

DoS stand for denial-of-service attack, a type of attack on a network that is designed to bring the network to its knees by flooding it with useless traffic. While DoS attacks do not usually result in information theft or any security loss for a company, they can cost an organization both time and money while their network services are down.
Areca Backup to Safeguarding Your Files -

No matter for what purpose you use your computer, one thing is certain -
a regular backup of data is necessary. Unfortunately, most users figure the importance of backing up data regularly too late and the problems start taking their toll with money, time and nerves. There are a lot of programs for making backups for all levels of users so it is needed to spend very little time to make the right choice, and we present you one that can satisfy your needs.
Government Web Sites Fail -

However, when 40% of the US Govt.'s own websites fail security tests, there is no sense of respect there but a shear lack thereof. The article mainly talks about DNS Security Extension (DNSSEC) which is an added security measure to DNS. However, DNSSEC itself is not the only method to be implemented by far.
System Intrusion 15 Seconds -

This Article/Tutorial will show you step by step how villian on the web try to hack into everyday PC's. Learn what you can do to protect yourself as well.
IE Solved - Cannot Display the Webpage -

Today, I was browsing through some free font sites when decided to take a break. Upon my return, I saw what at once seemed like a
computer virus protection software alerting me of a possible infection. However, I could tell this was fake because I never installed that
antivirus software. I've always relied on AVG and Avira as my primier free
antivirus firewall software.
Hacktivism: A Ghost Buster of Internet -

Many hackers have decided that if they're going to learn computer security by breaking into servers, those servers might as well belong to people they don't like.
How to Unlock Your Computer if You Lost Your Password -
 Using the reset a password disc
Using the reset a password disc is the right solution if you have prepared before, but what happens if you didn't take the needed steps before you have lost your password? If this is truly the case, you have to use a special program that will enable unlocking your operating system.
The best free option is Ophcrack, a program that guesses the code by using a special program called "
the rainbow table".
Essence of Hacking In Today's World -

Brief discussion on hacking and how it affects our war on terrorism. And how some hacking is in the interest of the US while some hacking hurts us in this current war. Writer also mentions role of Hackers, Crackers, and also Phreakers.
Symantec Platform of Trust -

The online world today can be a scary place. The presence of the Internet in everyday life has brought with it the emergence of malicious activities, which are steadily increasing. Online shoppers, users of the portal for electronic payments and transactions and any other services that include the exchange of confidential or personal data are reasonably concerned.
Understanding Virtualization Concepts -

Virtualization is a process in which a physical computer a.k.a. host computer contains virtual machines that are stored in them in form of files. These virtual machines act exactly the way the physical computers do and can be mapped with the NICs of the host computers. Once mapped, the operating systems installed inside the virtual machines (Guest Operating Systems) can then communicate with the host computers as well as the network setups to which the host computers might be connected.

Understanding Firewalls -

A firewall can be thought of as a gatekeeper who has been handed over a list of people whom he must allow to enter into the premises and/or the list of those people whose request to enter the premises must be denied straightforward. Just like the role of a gatekeeper, a firewall monitors incoming and outgoing network traffic to and from a computer system and allows or denies the communication of the computer with other computers that are connected to it via Local Area Network (LAN). Since in network communication, the packets are transported over the cable or through wireless media, a firewall allows or denies the communication on the basis of source ...
Remove Spyware -

Have you ever gone to a site, and so many pop-ups appear that you feel like your going to explode? Well you need "Remove Spyware Software"
Prolong Your Computers Life -

Do you feel frustrated every time you use your computer because it has really bad performance? Maybe you are thinking about buying a new computer even though it demands a lot of money and it will take away lots of time. Fortunately, there are techniques which you can use to
prolong the life time of your computer and in that way avoid buying a new one.
Understanding DHCP Classes -

In small-scale organizations and home environments, DHCP servers are installed normally and no class oriented configurations are done. The reason behind this is that by default all DHCP client computers belong to default DHCP class and as soon as DHCP scopes are configured and the DHCP servers become ready to assign dynamic addresses to the client computers, the DHCP clients start receiving the IP addresses without any additional administrative overheads. However, in order to allow DHCP servers to assign different ...
Understanding DHCP Servers -

Dynamic Host Configuration Protocol or DHCP servers are the dedicated computers that have network operating systems installed on them and are responsible for providing automatic IP addresses to all the client computers that are configured to obtain the addresses automatically.
Is Internet Shopping Still a Taboo? -

We have all heard about someone
shopping over the Internet more or less successfully and we can just vaguely remember how it all works. This text will break some dilemmas and enlighten Internet shopping.
Best Money Making Computer Fields -
 What Computer Field Makes the Most Money?
What Computer Field Makes the Most Money? This is a common question amongst many and is also very annoying. First of all, don't go in a field just for the money alone, you'll regret it in the long run. Believe me, I know what I'm talking about!
TW Tech Glossary - Misplaced your bible? Well here it is - Tech Glosasary! This truly took a while to complete and should be used by all from beginners to advance techies.
MD5 File Hasher 1.3 -
The hash function is a way of mapping a collection of information that can be various lengths in other values of fixed length. The values that the hash function gives are called hash values, codes, sums, checksums or simply hashes.
MD5 is a cryptographic hash algorithm, which means that it takes information of arbitrary length and creates fixed lengths for it, a cryptographic hash value, in a way that any change of data (accidental or on purpose) leads to the change of that value.

Rootkit - Ways to Remove Rootkit from a Windows System -

A rootkit is a program that allows attackers to obtain manager entry to a system. On Unix/Linux system, this is known as "root" accessibility. Rootkits contain resources and value that help assailants(attackers) cover up their existence as well as give the enemy full control of the hosting server or customer device consistently without being observed. Sometimes they even cause common viruses type problems. I had a case where a web browser hijack was being brought on by a particular rootkit set up on the program. In this article, I will show you one way to eliminate a Rootkit from a Windows program.

WikiLeaks, The Technical Aspect -

Wikileaks has been in the news for quite some time now as it has rocked many nations, embroiling itself in controversy over the fact that it has been releasing classified documents which have been termed as potentially harmful for national security as well as international diplomacy. Amidst all the confusion related to it's ethical and moral standards, people around the world have also speculated how the site functions technically, as a site which has been so controversial, might be technologically sound as well because various steps have already been taken in order to shut the Website down but none of them have availed any results.
Computer Networks Common Misconceptions -

There are not enough people who offer advice to help others learn about computer networks. For some reason, however, certain facts about networking tend to be misunderstood. This article describes the commonly held misconceptions that people have.
Understanding LAN Switches -

LAN switches, which are also sometimes called intelligent hubs, are the networking devices that have completely dominated and replaced Hubs. The reason behind this is that unlike Hubs, that only used to regenerate the received packets and forward them to all the ports that they had, LAN switches create one-to-one virtual circuits directly to the ports to which the destination computers are connected. This reduces the time consumed while transferring the data packets from the source computers to the destination ones.
How To Recover Your Deleted Files? -

It has probably happened to you that you
accidentally delete some file, and then in a hurry tried to get it back but you again, by accident, clicked on empty recycle bin and lost that file forever. Imagine that there is a solution for this. Of course there is one, and with the help of the
program Recuva.

Understanding Wireless Network Topologies -

In any network setup, network topology plays an important role without which network cannot be established whatsoever. In other words, whenever two or more machines are connected to each other, a topology is automatically formed. Unlike wired networks that have multiple topologies, wireless networks have only two topologies namely Infrastructure and Ad Hoc. Since wireless networks work on unguided media, it makes sense to have limited number of topologies while configuring the wireless network setups. Moreover, since wireless networks are a bit complicated configure as compared to the wired networks, it is essential for the administrators to have ...
Hacking: Where It Came From And How? -

Dont worry, its not a history lesson. Well maybe it is, but its worth knowing where it originated from. Hacking is rapidly becoming a problem not only to big time corporations but also to simple individuals like ourselves.
Understanding Ring Topology -

In ring topology, data used to transfer in the form of ring where every computer that was connected to the network had two LAN cards and each LAN card was connected to the LAN card of its neighbor computer. Many times ring topology was preferred over bus topology because there were no collisions and the chances of network getting congested were next to 0%.
Physical Network Devices -
.jpg)
In collective network topology it may happen that two users that are connected to opposite ends with a closer can not communicate because the digital signal is distorted over time and is not as recognizable. Therefore, a device is inserted that has two-way communication and performs restoration of digital signals.
Reward for Kaspersky Internet Security 2013 -

Kaspersky Internet Security 2013 was one of only four antivirus products that have amazed analysts from an independent organization for testing IT safety solutions, MRG Effitas, in that they did, during the test that was recently done, blocked all attempts to steal financial information.
Crack or Hack? -

Would you hack a walnut or crack it? Well, isn't it the same thing? No? Then why do people consider hackers and crackers to be the same? Read the details here.
How to Configure Win7 to Enable BitLocker without TPM -
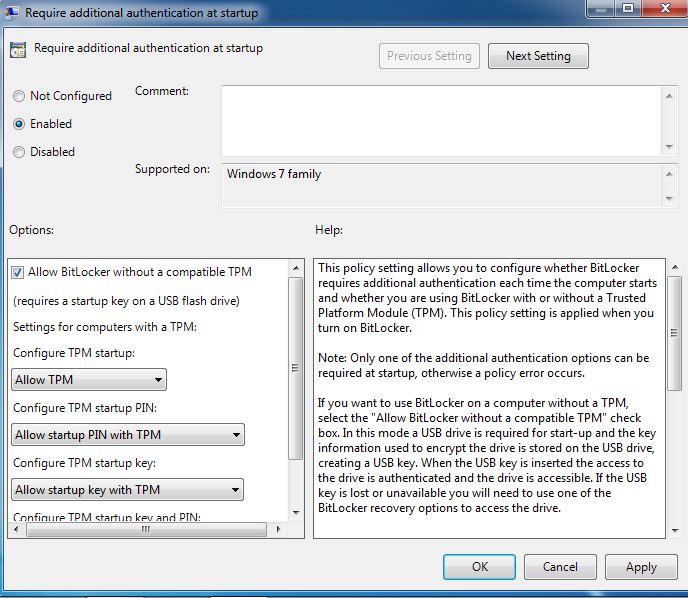
Trusted Platform Module (TPM) is a hardware chip that is integrated in almost all latest computer systems and it stores a key from the key pair that is used to encrypt/decrypt the hard disk drive if the BitLocker drive encryption feature is enabled. In order to enable BitLocker drive encryption on a Windows 7 computer, the computer must have TPM chip present in it and the feature must be enabled in the BIOS settings of the motherboard, failing to which BitLocker drive encryption cannot be enabled on the computer under normal circumstances.

Choosing a Secure Password -

Have you ever signed up for an online service and entered your favourite password, the one you always use for everything, only to be told that you're using a dictionary word and you need to change it? Or that you don't have any numbers in it? Or it's too short, too long, there's two letters the same, no mix between uppercase and lowercase, or even that there's more than one occurrence of the same letter! Annoying, huh? Check out this article to learn more.
Trojan -

In our studies we have found that Trojans are primarily responsible for almost all Windows Based machines being compromised. Find out more in this weeks article.
Ethics of Hacking -

This article was submitted by one of the visitors. It seems to have been written a long time ago however, the information in it is invaluable. Find out what a hacker is from a hackers point of view. It just may surprise you to hear what the writer has to say.
The Script Kiddie -

This is a very short but very thought provoking fictitious story about a script kiddie who become a real hacker. And so the budding hacker asked some computer people he knew how to learn more about computers. They advised him to try building his own computer by putting parts together.
E-Security -

We cannot have our networks secured from anyone unless we know a bit about security itself. Well here is your chance to get to know what is involved in E-Security. And remember, "There Always Watching"! The owners of storage and processing systems must take very specific steps to protect their assets and monitor their networks to counter the security threats.
Understanding Bus Topology -

n a nutshell, network topologies are the physical alignments of computers and the way they are connected to each other. For example, if all the computers are connected to each other via a central device (Hub or Switch), the type of topology is Star. Likewise, if all the computers are connected to each other via a main cable, this means it is Bus Topology.
What is Online Security and General PC Security?
In the IT industry the word "security" relates to a variety of issues. It could be things associated to Viruses, Hacking, Software Piracy (Cracking), Telephone Misuse (Phreaking), etc...
In this category of TW, we'll try to cover as much as possible so nobody feels left out. Also, as you can imagine, the category of Security can be taken as anything. There are just way too much information to sort out here. Some people maybe looking for ways to defend thier computers from Viruses and some from Hackers. And yet there maybe some idiots that are looking into ways to play pranks on innocent people. For the later bunch, your in the wrong place boys and girls. But for the first bunch, you couldn't have come to a better spot.
TW has been intending to liquify as much security information as possible to its readers for over a year now. And we finally think its time we applied it. Here, you'll find information on Privacy, Virus Control, Hacker Defence, Software Piracy Protection and More...But the only problem we are facing is "how to keep it simple enough so that people can directly get to thier intended information quickly?". Well, we are still working on that problem but for now, read as much as you can here. It Will Come In Handy Someday!
Tips
Implement all of these tips
Every computer with Internet access is part of the solution contributing to a secure Cyberspace. Any of these computers can be used by hackers for malicious purposes and to attack others, even if the computer is not on the Internet full time. Following these guidelines will greatly reduce the chance that your computer can be compromised by hackers.
Learn about available security solutions
A multi-layered security solution is required and it is important to know how different solutions work and how they compliment each other. A complete computer security solution set uses the "best of breed" in each of the following categories:
- Anti-Hacker Software - For defending against non-viral malicious code - the new security threat.
- Anti-Virus Software - For defending against fragmented self-replicating code.
- Firewall Protection - For controlling what is allowed to and from your computer to the Internet.
- Content (Web) Filtering Software - For making computers safer for kids on the Internet.
Protect your computers
Get the best anti-hacking, anti virus and firewall software available. This is the first and most critical step to getting protection from the hacker threats on the Internet today. The focus of this site is to provide the best products, updates and information to make this ongoing task as easy as possible.
Keep the software up to date. This especially includes non-security programs
Operating systems (like Windows 95, 98, 2K XP) and Email programs (like Outlook, Outlook express) and Internet Browsers (like Explorer, Netscape) have known security holes and need updating. Hackers know all too well about these holes and regularly exploit them. Regular software updates are necessary and required to keep these threats at bay.
Use a Firewall
This is the first line of defense on the Internet.
A Firewall protects computers from non-desirable Internet traffic.
For home computers choose a personal firewall (software) for the most user friendly protection. These products will send an alert when a particular program is trying to access the Internet and/or an unknown source is trying to access the computer from the Internet.
If you need to protect many computers, a hardware firewall solution is strongly recommended, along with someone that is qualified to configure and maintain it.
Don't open E-mail from strangers. Especially attachments. Turn off preview.
This is a favorite medium for malicious hackers because threats can travel so fast. If you suspect a message, is malicious, highlight it and delete it by pressing (shift + delete) (PC) for complete deletion. Web based Email environments are especially at risk. Be even more careful if you use these services. Some programs are able to use the preview pane to execute. We recommend that this feature be turned off.
Use hard to guess User Names and Passwords.
Don't use your real name as your user name. Using something other than your real name makes it harder for hackers to guess your account information and then access your resources.
Passwords should use a combination of UPPER & lower case letters and numbers for example; 3J16o1H7n. Don?t use the same password everywhere, so if a hacker should guess one, they can?t use it at every one of your sites. Change your passwords every 90 days at a minimum (or at each season change for example).
Disconnect from the Internet when not in use.
When you are done working on the Internet, disconnect. You can always continue to work ?off line?. This is especially important to personal DSL, cable modem and users that have an ?always on? connection to the Internet. It is nice to have these ?bigger pipes? that allow you to work better and faster, but it also allows malicious work the same luxury.
When you are not using your computer, turn it off! It saves power and locks out hackers.
Learn about file sharing.
Unless you absolutely need file sharing, make sure it is turned off so your operating system does not allow others access your files. Do not give others access to your computer. Check your operating system help menu for information on how to turn file sharing off.
Download security ?patches? regularly for all your software.
Quite often bugs and vulnerabilities are discovered in original manufacturer?s software and they fix these bugs with patches, or updates to the software. If you don't have the time to do the updates yourself, install a utility program to do it. There are software programs available that can provide the updates for you.
Use the highest security settings on your Internet browser that is tolerable
Adjust the browser security level to the highest level and work with it for a week. If you find it is too cumbersome and you can't easily access certain sites (especially this one!), back it off a step and repeat the process. Be patient, the higher the setting the less exposure there is to accepting unknown files and programs.
Share this information with your family and friends
The pests and viruses on the Internet can be thought of like polio. If we all get the medicine (security programs) and keep them current (like vaccine), life for the hackers will become more and more difficult. Encourage your family, friends, neighbors and co-workers to get a comprehensive set of tools and keep them current. Otherwise we can count on getting the same viruses and pests over and over.
|
|
|
|
 Did You Know?
- Every year, the number of hackers is growing in multiples of 3. And every year they are getting better at thier trade.
- Almost 80% of all computers without anti-virus software are infected with a mid-range virus on a monthly basis. That number is lowered to 15% for computers with an antivirus software.
- Best way to protect yourself online is to limit your one-one chats with people you dont know.
- ICQ in our test came out a pure looser in terms of keeping the user secured from IP peakers.

|
|
|
|
|
|




























































































 Information from a research that the research company IDC conducted for the Business Software Alliance (BSA) show that 36% of bought software in 2006. is pirate software. In a research IDC has analyzed the use of software in a 102 different countries across the world and it is estimated that the software that was installed on all computers in these countries was worth 105 billion dollars, and that the sale of legal software has risen for about 9 percent.
Information from a research that the research company IDC conducted for the Business Software Alliance (BSA) show that 36% of bought software in 2006. is pirate software. In a research IDC has analyzed the use of software in a 102 different countries across the world and it is estimated that the software that was installed on all computers in these countries was worth 105 billion dollars, and that the sale of legal software has risen for about 9 percent. The words "free" and "app" can often bring to the fore the greedy kid inside the individuals from the tech savvy brigade - people like yourself for example. Even so, when the aforementioned pair of words combines you just can't help hankering after this technological treat - of course much to the detriment of your smart phone in numerous cases. Mobile phone spy software can ensure that your cell phone goes kaput and hence it is extremely important that you steer clear of the spyware for your Android phone. Here's how you can do it...
The words "free" and "app" can often bring to the fore the greedy kid inside the individuals from the tech savvy brigade - people like yourself for example. Even so, when the aforementioned pair of words combines you just can't help hankering after this technological treat - of course much to the detriment of your smart phone in numerous cases. Mobile phone spy software can ensure that your cell phone goes kaput and hence it is extremely important that you steer clear of the spyware for your Android phone. Here's how you can do it... We all know that we need more bandwidth now, than we ever did in the past. There tons more online games, online movies, online collab work, you name it. And the past standards of Wifi namely 802.11a, 802.11b, 802.11g, 802.11n, and so on) were getting better and better; however, the 802.11ac does the trick. Well, atleast for now it is, until something better comes along.
We all know that we need more bandwidth now, than we ever did in the past. There tons more online games, online movies, online collab work, you name it. And the past standards of Wifi namely 802.11a, 802.11b, 802.11g, 802.11n, and so on) were getting better and better; however, the 802.11ac does the trick. Well, atleast for now it is, until something better comes along. Domain Name System or DNS servers are dedicated computers that have network operating systems installed on them and are responsible for resolving hostnames (computer names) to their IP addresses and vice versa. DNS servers are used worldwide and are helpful while accessing the Internet and visiting websites. Every Internet Service Provider or ISP has its own DNS server which receives name resolution requests from the subscribers of that ISP and resolves the requested host names to their corresponding IP addresses.
Domain Name System or DNS servers are dedicated computers that have network operating systems installed on them and are responsible for resolving hostnames (computer names) to their IP addresses and vice versa. DNS servers are used worldwide and are helpful while accessing the Internet and visiting websites. Every Internet Service Provider or ISP has its own DNS server which receives name resolution requests from the subscribers of that ISP and resolves the requested host names to their corresponding IP addresses. Apart from star topology that is widely used in almost every network environment, the other type of topology that is complex while setting up but provides 100% fault tolerance to the network is Mesh Topology. In this topology, every computer that has to be connected to the network is connected to every computer that is available in the network. For example if there are four computers namely A, B, C and D, then A will be connected to B, C and D. Likewise B will be connected to A, C and D and so on. This means that when mesh topology is used while establishing a network setup, it is very unlikely that the network would ever face congestions or would ever fail.
Apart from star topology that is widely used in almost every network environment, the other type of topology that is complex while setting up but provides 100% fault tolerance to the network is Mesh Topology. In this topology, every computer that has to be connected to the network is connected to every computer that is available in the network. For example if there are four computers namely A, B, C and D, then A will be connected to B, C and D. Likewise B will be connected to A, C and D and so on. This means that when mesh topology is used while establishing a network setup, it is very unlikely that the network would ever face congestions or would ever fail. Ever wonder if it's a good idea to switch your home LAN to wireless? This is a very easy to understand discussion about the security matters involved.
Ever wonder if it's a good idea to switch your home LAN to wireless? This is a very easy to understand discussion about the security matters involved. In many homes, the network can't easily reach all areas a person needs. This fact surprises many people. Stringing network cables to some rooms may prove impractical, of course. But even in wireless networks, "cold spots" where the Wi - Fi radio signals will not reach the corner of the bedroom, study or porches are also common. Be prepared that there is some planing needed in network installation.
In many homes, the network can't easily reach all areas a person needs. This fact surprises many people. Stringing network cables to some rooms may prove impractical, of course. But even in wireless networks, "cold spots" where the Wi - Fi radio signals will not reach the corner of the bedroom, study or porches are also common. Be prepared that there is some planing needed in network installation. FIREWALL - By its function it is an expanded capabilities gateway. Expansion refers primarily to prevent unauthorized access to the network in general. Aforementioned means that the network device provides control of traffic between the Internet and a local network in a way that all incoming Internet traffic is filtered according to defined filtering rules.
FIREWALL - By its function it is an expanded capabilities gateway. Expansion refers primarily to prevent unauthorized access to the network in general. Aforementioned means that the network device provides control of traffic between the Internet and a local network in a way that all incoming Internet traffic is filtered according to defined filtering rules. One of most important type of server is cluster servers. Software that enables clustering of servers is installed into a computer. Clustering servers also serve as load balancing servers between two computers. This is a common small business server. Clustering servers are used to avoid server failover. Server failover is the capability to shift to another standby server if the main server fails.
One of most important type of server is cluster servers. Software that enables clustering of servers is installed into a computer. Clustering servers also serve as load balancing servers between two computers. This is a common small business server. Clustering servers are used to avoid server failover. Server failover is the capability to shift to another standby server if the main server fails. Ever wonder why CNN keeps talking about technology when it comes to recent news of terrorism? Well thats because our biggest resource is "information" and its "specific distribution". Read all about what our threats, weaknesses, and how we are preparing for countering these threats.
Ever wonder why CNN keeps talking about technology when it comes to recent news of terrorism? Well thats because our biggest resource is "information" and its "specific distribution". Read all about what our threats, weaknesses, and how we are preparing for countering these threats. You wouldn't go to a doctor who had never been to medical school, or hire a lawyer who never studied law. One side-effect of a world advancing as rapidly as ours is that fields are becoming more and more specialized and narrow. People can no longer get by on general knowledge in their careers, something I found out for myself not too long ago. I'd been out of high school for two years, scraping by on my own and picking up scraps of programming as I went. I saw all of the self-taught programmers breaking into the IT industry, and I hoped to do the same. After all, IT is one of the few industries out there where being creative and a quick learner is more important than a degree.
You wouldn't go to a doctor who had never been to medical school, or hire a lawyer who never studied law. One side-effect of a world advancing as rapidly as ours is that fields are becoming more and more specialized and narrow. People can no longer get by on general knowledge in their careers, something I found out for myself not too long ago. I'd been out of high school for two years, scraping by on my own and picking up scraps of programming as I went. I saw all of the self-taught programmers breaking into the IT industry, and I hoped to do the same. After all, IT is one of the few industries out there where being creative and a quick learner is more important than a degree. LAN Bridges were used to separate and isolate multiple collision domains from each other in large broadcast domains. Bridges had two or more LAN ports to which other central devices, such as network Hubs, were connected via LAN cables. Unlike network Hubs that used to forward data packets to every PC that was connected to the ports, Bridges acted more like LAN Switches to identify destination ports and transferred the data packets only if the packets were destined to reach the segments that were connected to their other ends. Bridges used to calculate and identify the destination segments on the basis of physical (MAC) addresses of the central devices that were connected to their LAN ports.
LAN Bridges were used to separate and isolate multiple collision domains from each other in large broadcast domains. Bridges had two or more LAN ports to which other central devices, such as network Hubs, were connected via LAN cables. Unlike network Hubs that used to forward data packets to every PC that was connected to the ports, Bridges acted more like LAN Switches to identify destination ports and transferred the data packets only if the packets were destined to reach the segments that were connected to their other ends. Bridges used to calculate and identify the destination segments on the basis of physical (MAC) addresses of the central devices that were connected to their LAN ports. Microsoft Windows (and other personal operating systems) contain a built-in file sharing system. For example, the Windows folder can be shared over a local network (LAN) or the Internet by using Explorer as well as network drive mappings. You are also able to set restrictions on access security in order to control who can get the shared files.
Microsoft Windows (and other personal operating systems) contain a built-in file sharing system. For example, the Windows folder can be shared over a local network (LAN) or the Internet by using Explorer as well as network drive mappings. You are also able to set restrictions on access security in order to control who can get the shared files. WiFi Security feature protects your network and gets quick access associated with Win2K, XP. It supports WEP or WPA and gives you real-time interloper alerts you from free blockers and you feel glad when there is no spyware and no adware in your network to spoil your files. Any users get access to the Internet by means of laptop, handhold games, smart cell phones and PDA. The most important thing is it tenders a trouble-free and cheap method to safe and sound your network connection at any hotspot all over the world. WiFi Security examines data and perceives entrance point in real time and identifies the user who wants to spoil your files.
WiFi Security feature protects your network and gets quick access associated with Win2K, XP. It supports WEP or WPA and gives you real-time interloper alerts you from free blockers and you feel glad when there is no spyware and no adware in your network to spoil your files. Any users get access to the Internet by means of laptop, handhold games, smart cell phones and PDA. The most important thing is it tenders a trouble-free and cheap method to safe and sound your network connection at any hotspot all over the world. WiFi Security examines data and perceives entrance point in real time and identifies the user who wants to spoil your files. I think we hit the mother-load of server security information in this article people. We urge, every server admin as well as those looking to get into server and network security to not miss out on this article. You may already be experiencing attacks and wouldn't even know. And we like to point out that this article has no views against the "White-Hat Hacking Community."
I think we hit the mother-load of server security information in this article people. We urge, every server admin as well as those looking to get into server and network security to not miss out on this article. You may already be experiencing attacks and wouldn't even know. And we like to point out that this article has no views against the "White-Hat Hacking Community."  Since over a decade, star topologies have been preferred over bus topologies by the administrators. In star topology, a central device (Hub or Switch) is used to connect multiple PCs in a local area network. Central devices that are used in star topologies have multiple LAN ports integrated in them and the PCs are connected to the central devices via patch cables. In most cases patch cables are twisted pair cables that have four twisted pairs (eight wires in all) which are crimped to the RJ-45 connectors. The reason why star topology is mostly preferred nowadays is that it does not provide a single point of failure and is highly scalable. This means ...
Since over a decade, star topologies have been preferred over bus topologies by the administrators. In star topology, a central device (Hub or Switch) is used to connect multiple PCs in a local area network. Central devices that are used in star topologies have multiple LAN ports integrated in them and the PCs are connected to the central devices via patch cables. In most cases patch cables are twisted pair cables that have four twisted pairs (eight wires in all) which are crimped to the RJ-45 connectors. The reason why star topology is mostly preferred nowadays is that it does not provide a single point of failure and is highly scalable. This means ... By now most Windows users are probably familiar with the notion of user accounts and how all users on a PC can have their own individual settings, documents, and other features. In
By now most Windows users are probably familiar with the notion of user accounts and how all users on a PC can have their own individual settings, documents, and other features. In  What types of computer crimes do you and your company have to look out for? How do you avoid these criminals? Because computers are found in just about every home and office now, criminals are becoming smarter.
What types of computer crimes do you and your company have to look out for? How do you avoid these criminals? Because computers are found in just about every home and office now, criminals are becoming smarter.  Modern metropolises can't function without computers and the Internet. Water supply and electricity, mobile and telecommunications - all function with the help of the Internet. What would happen if it terminated? If the computer network or a system server failed, that would lead to devastating consequences for people and the economy. According to some estimates Internet crime brings more profit than drug related crime. Threats from the virtual space can go much further than home computers or work place computers.
Modern metropolises can't function without computers and the Internet. Water supply and electricity, mobile and telecommunications - all function with the help of the Internet. What would happen if it terminated? If the computer network or a system server failed, that would lead to devastating consequences for people and the economy. According to some estimates Internet crime brings more profit than drug related crime. Threats from the virtual space can go much further than home computers or work place computers. The type of email scam in which an email is sent claiming to be an established enterprise like eBay, Citibank, PayPal, Amazon.com, etc in an attempt to scam the user into surrendering private information. The word phishing comes from the analogy that Internet scammers are using e-mail lures to fish for passwords and financial data from the sea of Internet users. The term was coined in 1996 by hackers who were stealing AOL Internet accounts by scamming passwords from unsuspecting AOL users.
The type of email scam in which an email is sent claiming to be an established enterprise like eBay, Citibank, PayPal, Amazon.com, etc in an attempt to scam the user into surrendering private information. The word phishing comes from the analogy that Internet scammers are using e-mail lures to fish for passwords and financial data from the sea of Internet users. The term was coined in 1996 by hackers who were stealing AOL Internet accounts by scamming passwords from unsuspecting AOL users.  So I thought this morning I would try to be the optimist, and give reason to hope for the future of the Internet by drawing upon its present.
So I thought this morning I would try to be the optimist, and give reason to hope for the future of the Internet by drawing upon its present. Phishing is the act of sending out emails, supposedly from a certain trusted party, in order to trick out of the recipient sensitive information such as usernames, passwords, banking details etc. To avoid becoming a victim of phishing, stay alert. Whenever you receive an email telling you that you need to enter sensitive information treat it with suspicion.
Phishing is the act of sending out emails, supposedly from a certain trusted party, in order to trick out of the recipient sensitive information such as usernames, passwords, banking details etc. To avoid becoming a victim of phishing, stay alert. Whenever you receive an email telling you that you need to enter sensitive information treat it with suspicion. You can never be careful enough with the people that surround you and that may see something on your computer that they shouldn't. It probably happened to you that your boss suddenly enters your office and you are doing something you shouldn't. If you can, set your screen so it is available only to your eyes.
You can never be careful enough with the people that surround you and that may see something on your computer that they shouldn't. It probably happened to you that your boss suddenly enters your office and you are doing something you shouldn't. If you can, set your screen so it is available only to your eyes. The Internet is a useful place, but unfortunately it can also be quite dangerous. Just how do you know what is safe and what you should stay away from? This article gets right down to the point with some practical tips on avoiding a few tricks, so that you don't end up inconvenienced, annoyed, or devastated.
The Internet is a useful place, but unfortunately it can also be quite dangerous. Just how do you know what is safe and what you should stay away from? This article gets right down to the point with some practical tips on avoiding a few tricks, so that you don't end up inconvenienced, annoyed, or devastated..png) This time we had the chance to try out a product from the Chinese firm D-Link, a renowned manufacturer of computer networking equipment. It is a product that is called Cloud Router and is classified by the marking DIR-605L. In the package, next to the router, you get a voltage adapter (5V DC, 1A), LAN cable, CD with instructions and software, as well as printed documentation.
This time we had the chance to try out a product from the Chinese firm D-Link, a renowned manufacturer of computer networking equipment. It is a product that is called Cloud Router and is classified by the marking DIR-605L. In the package, next to the router, you get a voltage adapter (5V DC, 1A), LAN cable, CD with instructions and software, as well as printed documentation. Now we have all heard of various ways to help our PC to avoid viruses. Well this is article is no exception. But it does point out a couple of things that you dont usually hear discussed.
Now we have all heard of various ways to help our PC to avoid viruses. Well this is article is no exception. But it does point out a couple of things that you dont usually hear discussed. This is a good article to show you the differences between spyware and adware. Shows you what you can do to avoid them and protect yourself once infested. Adware is any computer program or software package in which advertisements or other marketing material are included with or automatically loaded by the software and displayed or played back after installation.
This is a good article to show you the differences between spyware and adware. Shows you what you can do to avoid them and protect yourself once infested. Adware is any computer program or software package in which advertisements or other marketing material are included with or automatically loaded by the software and displayed or played back after installation. Sniffing and spoofing are security threats that target the lower layers of the
Sniffing and spoofing are security threats that target the lower layers of the .jpg) A brief intoduction into the world of Spamming. Read to find out the only methods known to work in fighting spam emails.
A brief intoduction into the world of Spamming. Read to find out the only methods known to work in fighting spam emails. The most popular application of computer monitoring software is on office networks in a business establishment, where each workstation is actively monitored to see how the employees spend their entire work day.
The most popular application of computer monitoring software is on office networks in a business establishment, where each workstation is actively monitored to see how the employees spend their entire work day.
 Network hubs were the central devices that network administrators used to use to establish a network setup using Star Topologies. Network hubs had multiple RJ-45 ports integrated in them and were used to connect one end of the LAN cables that had RJ-45 connectors crimped to them. The other end of the cables were connected to the RJ-45 ports available on the PCs. Network hubs were available with 4, 8, 16 and 24 ports. Administrators also used to cascade two hubs for larger network setups. Cascading means that one RJ-45 port of one hub connected to ...
Network hubs were the central devices that network administrators used to use to establish a network setup using Star Topologies. Network hubs had multiple RJ-45 ports integrated in them and were used to connect one end of the LAN cables that had RJ-45 connectors crimped to them. The other end of the cables were connected to the RJ-45 ports available on the PCs. Network hubs were available with 4, 8, 16 and 24 ports. Administrators also used to cascade two hubs for larger network setups. Cascading means that one RJ-45 port of one hub connected to ... Spyware can be installed without the conscious consent of the user, allowing unsolicited spam or remote monitoring of a computer's activity. Neither spyware or adware can be removed using a normal Antivirus program.
Spyware can be installed without the conscious consent of the user, allowing unsolicited spam or remote monitoring of a computer's activity. Neither spyware or adware can be removed using a normal Antivirus program. The concern and debate about the ethical issues of a third party tracking and selling PC users online habits is not new in the Internet age. Yet the debate on personal Internet privacy is dramatically heating up in 2010 and gaining worldwide attention from civic and governmental organizations around the globe. The impetus for renewed focus on standardized levels of consumer online privacy is largely fueled by new technologies in cookie tracking tools that is garnering a name for itself in some industry circles as "super cookies."
The concern and debate about the ethical issues of a third party tracking and selling PC users online habits is not new in the Internet age. Yet the debate on personal Internet privacy is dramatically heating up in 2010 and gaining worldwide attention from civic and governmental organizations around the globe. The impetus for renewed focus on standardized levels of consumer online privacy is largely fueled by new technologies in cookie tracking tools that is garnering a name for itself in some industry circles as "super cookies." Routers are the devices that are used to connect two different networks in order to allow communication between them. Networks with different network IDs are considered to be different. By default, no communication can take place between two different networks, and this configuration prevents computers of one network from getting accessed by the computers on the other network, which may belong to another organization, building premises, home, etc.
Routers are the devices that are used to connect two different networks in order to allow communication between them. Networks with different network IDs are considered to be different. By default, no communication can take place between two different networks, and this configuration prevents computers of one network from getting accessed by the computers on the other network, which may belong to another organization, building premises, home, etc. You should always change your routers default password. That is a must. It is because the generic router passwords can be found all over the Internet. This information can be found by hackers and they could use it to break into your router and cause you a lot of problems.
You should always change your routers default password. That is a must. It is because the generic router passwords can be found all over the Internet. This information can be found by hackers and they could use it to break into your router and cause you a lot of problems. We've got so much email from so many NT Admins that it's almost unbelievable why we haven't come up with a tutorial for them. This tutorial is scrictly for those admins who make it a habit to forget passwords. Enjoy!
We've got so much email from so many NT Admins that it's almost unbelievable why we haven't come up with a tutorial for them. This tutorial is scrictly for those admins who make it a habit to forget passwords. Enjoy! Foremost, this trick/tip assumes that when the virus tries to send it self out to everyone in the address book, the mail client will falter on the bogus address and the attempt to send will fail.
Foremost, this trick/tip assumes that when the virus tries to send it self out to everyone in the address book, the mail client will falter on the bogus address and the attempt to send will fail. What eventually became one of the most significant advantages of the Internet is the possibility of simple access to any information placed on any computer attached to this global network. We can access the information that we need in various ways, from searching on the Web, to downloading complete files, even the ones that are pretty large. This text should help the enlightening of the dilemma about downloading files from the Internet and to give you short instructions on how to do it.
What eventually became one of the most significant advantages of the Internet is the possibility of simple access to any information placed on any computer attached to this global network. We can access the information that we need in various ways, from searching on the Web, to downloading complete files, even the ones that are pretty large. This text should help the enlightening of the dilemma about downloading files from the Internet and to give you short instructions on how to do it. As you see a business growing, it is normal that their layout of networks grows with them. Companies that are placed in a few locations will create internal connections that are called campus networks if their buildings are close to each other and use WAN networks if they are more distant.
As you see a business growing, it is normal that their layout of networks grows with them. Companies that are placed in a few locations will create internal connections that are called campus networks if their buildings are close to each other and use WAN networks if they are more distant. In computer networks, scope (area) up to where data that is transferred over the cables or the wireless media with certain conditions is categorized in two domain main types. In complex network setups, because multiple segments are connected to each other via different types of central devices, it becomes important for the administrators to separate broadcast domains and reduce the numbers of collision domains. A central device in which collisions may occur is Hub because of it logical Bus Topology.
In computer networks, scope (area) up to where data that is transferred over the cables or the wireless media with certain conditions is categorized in two domain main types. In complex network setups, because multiple segments are connected to each other via different types of central devices, it becomes important for the administrators to separate broadcast domains and reduce the numbers of collision domains. A central device in which collisions may occur is Hub because of it logical Bus Topology. One famous saying says that programmers are machines that turn caffeine from coffee and Coca Cola into a programming code. And if you ask a programmer when does he like working the most and when is he most productive - he is probably going to say late at night or early in the morning, that is when he has the greatest energy and concentration to work.
One famous saying says that programmers are machines that turn caffeine from coffee and Coca Cola into a programming code. And if you ask a programmer when does he like working the most and when is he most productive - he is probably going to say late at night or early in the morning, that is when he has the greatest energy and concentration to work. Here is something that no network or web developing professional should ignore. SSL is has already become the widely accepted. Read the full article to understand the intricacies and the nitty gritty of SSL. SSL comes in two strengths, 40-bit and 128-bit, which refer to the length of the "session key" generated by every encrypted transaction
Here is something that no network or web developing professional should ignore. SSL is has already become the widely accepted. Read the full article to understand the intricacies and the nitty gritty of SSL. SSL comes in two strengths, 40-bit and 128-bit, which refer to the length of the "session key" generated by every encrypted transaction Do you often feel tethered to your home computer or other electronic devices? Tired of the endless cords to untangle under your office desk? Then it's time to go completely wireless! It's easier than ever to live a completely wireless lifestyle, thanks to innovations in the consumer and business electronics industries. Review some of the latest gadgets and services that will have you free-wheeling it in no time.
Do you often feel tethered to your home computer or other electronic devices? Tired of the endless cords to untangle under your office desk? Then it's time to go completely wireless! It's easier than ever to live a completely wireless lifestyle, thanks to innovations in the consumer and business electronics industries. Review some of the latest gadgets and services that will have you free-wheeling it in no time. A VPN (virtual private network) gives you the possibility to encrypt every bit of traffic that goes through your network (it doesn't matter if it is going in our out).
A VPN (virtual private network) gives you the possibility to encrypt every bit of traffic that goes through your network (it doesn't matter if it is going in our out). Cookies are so good. Especially those chocolate chip kinds are my favorite. But not all cookies are so sweet. The cookies we talk about on the web are subject of frustration for many surfers. Find out why many sites use still use them.
Cookies are so good. Especially those chocolate chip kinds are my favorite. But not all cookies are so sweet. The cookies we talk about on the web are subject of frustration for many surfers. Find out why many sites use still use them. DoS stand for denial-of-service attack, a type of attack on a network that is designed to bring the network to its knees by flooding it with useless traffic. While DoS attacks do not usually result in information theft or any security loss for a company, they can cost an organization both time and money while their network services are down.
DoS stand for denial-of-service attack, a type of attack on a network that is designed to bring the network to its knees by flooding it with useless traffic. While DoS attacks do not usually result in information theft or any security loss for a company, they can cost an organization both time and money while their network services are down. No matter for what purpose you use your computer, one thing is certain - a regular backup of data is necessary. Unfortunately, most users figure the importance of backing up data regularly too late and the problems start taking their toll with money, time and nerves. There are a lot of programs for making backups for all levels of users so it is needed to spend very little time to make the right choice, and we present you one that can satisfy your needs.
No matter for what purpose you use your computer, one thing is certain - a regular backup of data is necessary. Unfortunately, most users figure the importance of backing up data regularly too late and the problems start taking their toll with money, time and nerves. There are a lot of programs for making backups for all levels of users so it is needed to spend very little time to make the right choice, and we present you one that can satisfy your needs. However, when 40% of the US Govt.'s own websites fail security tests, there is no sense of respect there but a shear lack thereof. The article mainly talks about DNS Security Extension (DNSSEC) which is an added security measure to DNS. However, DNSSEC itself is not the only method to be implemented by far.
However, when 40% of the US Govt.'s own websites fail security tests, there is no sense of respect there but a shear lack thereof. The article mainly talks about DNS Security Extension (DNSSEC) which is an added security measure to DNS. However, DNSSEC itself is not the only method to be implemented by far. This Article/Tutorial will show you step by step how villian on the web try to hack into everyday PC's. Learn what you can do to protect yourself as well.
This Article/Tutorial will show you step by step how villian on the web try to hack into everyday PC's. Learn what you can do to protect yourself as well. Today, I was browsing through some free font sites when decided to take a break. Upon my return, I saw what at once seemed like a computer virus protection software alerting me of a possible infection. However, I could tell this was fake because I never installed that antivirus software. I've always relied on AVG and Avira as my primier free antivirus firewall software.
Today, I was browsing through some free font sites when decided to take a break. Upon my return, I saw what at once seemed like a computer virus protection software alerting me of a possible infection. However, I could tell this was fake because I never installed that antivirus software. I've always relied on AVG and Avira as my primier free antivirus firewall software. Many hackers have decided that if they're going to learn computer security by breaking into servers, those servers might as well belong to people they don't like.
Many hackers have decided that if they're going to learn computer security by breaking into servers, those servers might as well belong to people they don't like. Using the reset a password disc is the right solution if you have prepared before, but what happens if you didn't take the needed steps before you have lost your password? If this is truly the case, you have to use a special program that will enable unlocking your operating system. The best free option is Ophcrack, a program that guesses the code by using a special program called "the rainbow table".
Using the reset a password disc is the right solution if you have prepared before, but what happens if you didn't take the needed steps before you have lost your password? If this is truly the case, you have to use a special program that will enable unlocking your operating system. The best free option is Ophcrack, a program that guesses the code by using a special program called "the rainbow table". Brief discussion on hacking and how it affects our war on terrorism. And how some hacking is in the interest of the US while some hacking hurts us in this current war. Writer also mentions role of Hackers, Crackers, and also Phreakers.
Brief discussion on hacking and how it affects our war on terrorism. And how some hacking is in the interest of the US while some hacking hurts us in this current war. Writer also mentions role of Hackers, Crackers, and also Phreakers..png) In this guide we will show you how to get rid of unwanted "trash" that keeps piling up when you are using Microsoft Windows.
In this guide we will show you how to get rid of unwanted "trash" that keeps piling up when you are using Microsoft Windows.  Computer viruses represent great danger and malpractice - they are antipodes of what we want to achieve working on the Net and craving towards the Internet with more humane character.
Computer viruses represent great danger and malpractice - they are antipodes of what we want to achieve working on the Net and craving towards the Internet with more humane character. The online world today can be a scary place. The presence of the Internet in everyday life has brought with it the emergence of malicious activities, which are steadily increasing. Online shoppers, users of the portal for electronic payments and transactions and any other services that include the exchange of confidential or personal data are reasonably concerned.
The online world today can be a scary place. The presence of the Internet in everyday life has brought with it the emergence of malicious activities, which are steadily increasing. Online shoppers, users of the portal for electronic payments and transactions and any other services that include the exchange of confidential or personal data are reasonably concerned. Virtualization is a process in which a physical computer a.k.a. host computer contains virtual machines that are stored in them in form of files. These virtual machines act exactly the way the physical computers do and can be mapped with the NICs of the host computers. Once mapped, the operating systems installed inside the virtual machines (Guest Operating Systems) can then communicate with the host computers as well as the network setups to which the host computers might be connected.
Virtualization is a process in which a physical computer a.k.a. host computer contains virtual machines that are stored in them in form of files. These virtual machines act exactly the way the physical computers do and can be mapped with the NICs of the host computers. Once mapped, the operating systems installed inside the virtual machines (Guest Operating Systems) can then communicate with the host computers as well as the network setups to which the host computers might be connected. Have you ever gone to a site, and so many pop-ups appear that you feel like your going to explode? Well you need "Remove Spyware Software"
Have you ever gone to a site, and so many pop-ups appear that you feel like your going to explode? Well you need "Remove Spyware Software" Do you feel frustrated every time you use your computer because it has really bad performance? Maybe you are thinking about buying a new computer even though it demands a lot of money and it will take away lots of time. Fortunately, there are techniques which you can use to prolong the life time of your computer and in that way avoid buying a new one.
Do you feel frustrated every time you use your computer because it has really bad performance? Maybe you are thinking about buying a new computer even though it demands a lot of money and it will take away lots of time. Fortunately, there are techniques which you can use to prolong the life time of your computer and in that way avoid buying a new one. In small-scale organizations and home environments, DHCP servers are installed normally and no class oriented configurations are done. The reason behind this is that by default all DHCP client computers belong to default DHCP class and as soon as DHCP scopes are configured and the DHCP servers become ready to assign dynamic addresses to the client computers, the DHCP clients start receiving the IP addresses without any additional administrative overheads. However, in order to allow DHCP servers to assign different ...
In small-scale organizations and home environments, DHCP servers are installed normally and no class oriented configurations are done. The reason behind this is that by default all DHCP client computers belong to default DHCP class and as soon as DHCP scopes are configured and the DHCP servers become ready to assign dynamic addresses to the client computers, the DHCP clients start receiving the IP addresses without any additional administrative overheads. However, in order to allow DHCP servers to assign different ... Here's a computer trick today that's very important and ingenious in it's simplicity in fighting against internet worms.
Here's a computer trick today that's very important and ingenious in it's simplicity in fighting against internet worms. We have all heard about someone shopping over the Internet more or less successfully and we can just vaguely remember how it all works. This text will break some dilemmas and enlighten Internet shopping.
We have all heard about someone shopping over the Internet more or less successfully and we can just vaguely remember how it all works. This text will break some dilemmas and enlighten Internet shopping. What Computer Field Makes the Most Money? This is a common question amongst many and is also very annoying. First of all, don't go in a field just for the money alone, you'll regret it in the long run. Believe me, I know what I'm talking about!
What Computer Field Makes the Most Money? This is a common question amongst many and is also very annoying. First of all, don't go in a field just for the money alone, you'll regret it in the long run. Believe me, I know what I'm talking about!  The hash function is a way of mapping a collection of information that can be various lengths in other values of fixed length. The values that the hash function gives are called hash values, codes, sums, checksums or simply hashes. MD5 is a cryptographic hash algorithm, which means that it takes information of arbitrary length and creates fixed lengths for it, a cryptographic hash value, in a way that any change of data (accidental or on purpose) leads to the change of that value.
The hash function is a way of mapping a collection of information that can be various lengths in other values of fixed length. The values that the hash function gives are called hash values, codes, sums, checksums or simply hashes. MD5 is a cryptographic hash algorithm, which means that it takes information of arbitrary length and creates fixed lengths for it, a cryptographic hash value, in a way that any change of data (accidental or on purpose) leads to the change of that value. A rootkit is a program that allows attackers to obtain manager entry to a system. On Unix/Linux system, this is known as "root" accessibility. Rootkits contain resources and value that help assailants(attackers) cover up their existence as well as give the enemy full control of the hosting server or customer device consistently without being observed. Sometimes they even cause common viruses type problems. I had a case where a web browser hijack was being brought on by a particular rootkit set up on the program. In this article, I will show you one way to eliminate a Rootkit from a Windows program.
A rootkit is a program that allows attackers to obtain manager entry to a system. On Unix/Linux system, this is known as "root" accessibility. Rootkits contain resources and value that help assailants(attackers) cover up their existence as well as give the enemy full control of the hosting server or customer device consistently without being observed. Sometimes they even cause common viruses type problems. I had a case where a web browser hijack was being brought on by a particular rootkit set up on the program. In this article, I will show you one way to eliminate a Rootkit from a Windows program. Wikileaks has been in the news for quite some time now as it has rocked many nations, embroiling itself in controversy over the fact that it has been releasing classified documents which have been termed as potentially harmful for national security as well as international diplomacy. Amidst all the confusion related to it's ethical and moral standards, people around the world have also speculated how the site functions technically, as a site which has been so controversial, might be technologically sound as well because various steps have already been taken in order to shut the Website down but none of them have availed any results.
Wikileaks has been in the news for quite some time now as it has rocked many nations, embroiling itself in controversy over the fact that it has been releasing classified documents which have been termed as potentially harmful for national security as well as international diplomacy. Amidst all the confusion related to it's ethical and moral standards, people around the world have also speculated how the site functions technically, as a site which has been so controversial, might be technologically sound as well because various steps have already been taken in order to shut the Website down but none of them have availed any results. There are not enough people who offer advice to help others learn about computer networks. For some reason, however, certain facts about networking tend to be misunderstood. This article describes the commonly held misconceptions that people have.
There are not enough people who offer advice to help others learn about computer networks. For some reason, however, certain facts about networking tend to be misunderstood. This article describes the commonly held misconceptions that people have. LAN switches, which are also sometimes called intelligent hubs, are the networking devices that have completely dominated and replaced Hubs. The reason behind this is that unlike Hubs, that only used to regenerate the received packets and forward them to all the ports that they had, LAN switches create one-to-one virtual circuits directly to the ports to which the destination computers are connected. This reduces the time consumed while transferring the data packets from the source computers to the destination ones.
LAN switches, which are also sometimes called intelligent hubs, are the networking devices that have completely dominated and replaced Hubs. The reason behind this is that unlike Hubs, that only used to regenerate the received packets and forward them to all the ports that they had, LAN switches create one-to-one virtual circuits directly to the ports to which the destination computers are connected. This reduces the time consumed while transferring the data packets from the source computers to the destination ones. It has probably happened to you that you accidentally delete some file, and then in a hurry tried to get it back but you again, by accident, clicked on empty recycle bin and lost that file forever. Imagine that there is a solution for this. Of course there is one, and with the help of the program Recuva.
It has probably happened to you that you accidentally delete some file, and then in a hurry tried to get it back but you again, by accident, clicked on empty recycle bin and lost that file forever. Imagine that there is a solution for this. Of course there is one, and with the help of the program Recuva. In any network setup, network topology plays an important role without which network cannot be established whatsoever. In other words, whenever two or more machines are connected to each other, a topology is automatically formed. Unlike wired networks that have multiple topologies, wireless networks have only two topologies namely Infrastructure and Ad Hoc. Since wireless networks work on unguided media, it makes sense to have limited number of topologies while configuring the wireless network setups. Moreover, since wireless networks are a bit complicated configure as compared to the wired networks, it is essential for the administrators to have ...
In any network setup, network topology plays an important role without which network cannot be established whatsoever. In other words, whenever two or more machines are connected to each other, a topology is automatically formed. Unlike wired networks that have multiple topologies, wireless networks have only two topologies namely Infrastructure and Ad Hoc. Since wireless networks work on unguided media, it makes sense to have limited number of topologies while configuring the wireless network setups. Moreover, since wireless networks are a bit complicated configure as compared to the wired networks, it is essential for the administrators to have ... Dont worry, its not a history lesson. Well maybe it is, but its worth knowing where it originated from. Hacking is rapidly becoming a problem not only to big time corporations but also to simple individuals like ourselves.
Dont worry, its not a history lesson. Well maybe it is, but its worth knowing where it originated from. Hacking is rapidly becoming a problem not only to big time corporations but also to simple individuals like ourselves. In ring topology, data used to transfer in the form of ring where every computer that was connected to the network had two LAN cards and each LAN card was connected to the LAN card of its neighbor computer. Many times ring topology was preferred over bus topology because there were no collisions and the chances of network getting congested were next to 0%.
In ring topology, data used to transfer in the form of ring where every computer that was connected to the network had two LAN cards and each LAN card was connected to the LAN card of its neighbor computer. Many times ring topology was preferred over bus topology because there were no collisions and the chances of network getting congested were next to 0%..jpg) In collective network topology it may happen that two users that are connected to opposite ends with a closer can not communicate because the digital signal is distorted over time and is not as recognizable. Therefore, a device is inserted that has two-way communication and performs restoration of digital signals.
In collective network topology it may happen that two users that are connected to opposite ends with a closer can not communicate because the digital signal is distorted over time and is not as recognizable. Therefore, a device is inserted that has two-way communication and performs restoration of digital signals. Kaspersky Internet Security 2013 was one of only four antivirus products that have amazed analysts from an independent organization for testing IT safety solutions, MRG Effitas, in that they did, during the test that was recently done, blocked all attempts to steal financial information.
Kaspersky Internet Security 2013 was one of only four antivirus products that have amazed analysts from an independent organization for testing IT safety solutions, MRG Effitas, in that they did, during the test that was recently done, blocked all attempts to steal financial information. Would you hack a walnut or crack it? Well, isn't it the same thing? No? Then why do people consider hackers and crackers to be the same? Read the details here.
Would you hack a walnut or crack it? Well, isn't it the same thing? No? Then why do people consider hackers and crackers to be the same? Read the details here. Have you ever signed up for an online service and entered your favourite password, the one you always use for everything, only to be told that you're using a dictionary word and you need to change it? Or that you don't have any numbers in it? Or it's too short, too long, there's two letters the same, no mix between uppercase and lowercase, or even that there's more than one occurrence of the same letter! Annoying, huh? Check out this article to learn more.
Have you ever signed up for an online service and entered your favourite password, the one you always use for everything, only to be told that you're using a dictionary word and you need to change it? Or that you don't have any numbers in it? Or it's too short, too long, there's two letters the same, no mix between uppercase and lowercase, or even that there's more than one occurrence of the same letter! Annoying, huh? Check out this article to learn more. In our studies we have found that Trojans are primarily responsible for almost all Windows Based machines being compromised. Find out more in this weeks article.
In our studies we have found that Trojans are primarily responsible for almost all Windows Based machines being compromised. Find out more in this weeks article. This article was submitted by one of the visitors. It seems to have been written a long time ago however, the information in it is invaluable. Find out what a hacker is from a hackers point of view. It just may surprise you to hear what the writer has to say.
This article was submitted by one of the visitors. It seems to have been written a long time ago however, the information in it is invaluable. Find out what a hacker is from a hackers point of view. It just may surprise you to hear what the writer has to say. This is a very short but very thought provoking fictitious story about a script kiddie who become a real hacker. And so the budding hacker asked some computer people he knew how to learn more about computers. They advised him to try building his own computer by putting parts together.
This is a very short but very thought provoking fictitious story about a script kiddie who become a real hacker. And so the budding hacker asked some computer people he knew how to learn more about computers. They advised him to try building his own computer by putting parts together. We cannot have our networks secured from anyone unless we know a bit about security itself. Well here is your chance to get to know what is involved in E-Security. And remember, "There Always Watching"! The owners of storage and processing systems must take very specific steps to protect their assets and monitor their networks to counter the security threats.
We cannot have our networks secured from anyone unless we know a bit about security itself. Well here is your chance to get to know what is involved in E-Security. And remember, "There Always Watching"! The owners of storage and processing systems must take very specific steps to protect their assets and monitor their networks to counter the security threats.  n a nutshell, network topologies are the physical alignments of computers and the way they are connected to each other. For example, if all the computers are connected to each other via a central device (Hub or Switch), the type of topology is Star. Likewise, if all the computers are connected to each other via a main cable, this means it is Bus Topology.
n a nutshell, network topologies are the physical alignments of computers and the way they are connected to each other. For example, if all the computers are connected to each other via a central device (Hub or Switch), the type of topology is Star. Likewise, if all the computers are connected to each other via a main cable, this means it is Bus Topology.
