IT Certifications
IT Jobs - What's Out There? -

In this article, we would like to point out the obvious
IT Jobs that at times get overlooked. Find out what's out there and which
information technology is the right choice for you. From people that create
laptop computers to folks that do
web design to
developers that come up with
computer software concepts from scratch. Also a bit at the end about
computer schools and
computer training.

How Virtual LANs (VLANS) Work -
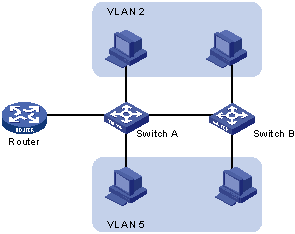
A VLAN is a grouping of computers that is logically segmented by functions, project teams, or applications without regard to the physical location of users. Similar to routers, VLANs offer an effective mechanism for setting up firewalls in a switch fabric, protecting the network against broadcast problems that are potentially dangerous, and maintaining all the performance benefits of switching. You can create these firewalls by assigning switch ports or users to specific VLAN groups in single switches and across multiple connected switches, which will increase security easily and inexpensively by segmenting the network.

Leaping Ahead in WiFi Standard - 802.11ac -

We all know that we need more bandwidth now, than we ever did in the past. There tons more online games, online movies, online collab work, you name it. And the past standards of Wifi namely 802.11a, 802.11b, 802.11g, 802.11n, and so on) were getting better and better; however, the 802.11ac does the trick. Well, atleast for now it is, until something better comes along.
Understanding DNS Servers -

Domain Name System or DNS servers are dedicated computers that have network operating systems installed on them and are responsible for resolving hostnames (computer names) to their IP addresses and vice versa. DNS servers are used worldwide and are helpful while accessing the Internet and visiting websites. Every Internet Service Provider or ISP has its own DNS server which receives name resolution requests from the subscribers of that ISP and resolves the requested host names to their corresponding IP addresses.

Understanding Mesh Topology -

Apart from star topology that is widely used in almost every network environment, the other type of topology that is complex while setting up but provides 100% fault tolerance to the network is Mesh Topology. In this topology, every computer that has to be connected to the network is connected to every computer that is available in the network. For example if there are four computers namely A, B, C and D, then A will be connected to B, C and D. Likewise B will be connected to A, C and D and so on. This means that when mesh topology is used while establishing a network setup, it is very unlikely that the network would ever face congestions or would ever fail.

Types of Servers 2 -

One of most important type of server is cluster servers. Software that enables clustering of servers is installed into a computer. Clustering servers also serve as load balancing servers between two computers. This is a common small business server. Clustering servers are used to avoid server failover. Server failover is the capability to shift to another standby server if the main server fails.
Computer Certification Training in Houston -
![Zend Certification]()
I live in Magnolia, TX area which is just North West of Houston. I'm sure, all that I would need is to maybe get a couple of community college classes to brush up on the fundamentals of programming, then maybe a few hours training on PHP to get up to speed. Finally, I'll need a few hours training for the Zend Certification itself, right? I mean this is the United States of America. We invented most of this stuff.
7 Layers of the OSI Model -
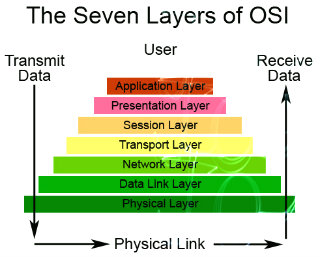
Ever heard of OSI? Know what it is fully? No? Well what are you waiting for? Get cracking this week on the 7 Layers of the OSI Model. So that the next time the topic comes up, you'll have a clue. OSI short for Open System Interconnection, an ISO standard for worldwide communications that defines a networking framework for implementing protocols in seven layers. ISO shorts for International Organization for Standardization.
Backing Up Your Data On An External Hard Disk -
 External hard disks
External hard disks are becoming an essential part of computer equipment whether it is business or user based computer systems. Except for the fact that they enable storing more data, they don't slow down your processor. External hard disks are connected with the computer using a USB cable. USB ports are now being placed in almost every computer. If you are buying a new computer make sure that....

Computer Training Excuses -

You wouldn't go to a doctor who had never been to medical school, or hire a lawyer who never studied law. One side-effect of a world advancing as rapidly as ours is that fields are becoming more and more specialized and narrow. People can no longer get by on general knowledge in their careers, something I found out for myself not too long ago. I'd been out of high school for two years, scraping by on my own and picking up scraps of programming as I went. I saw all of the self-taught programmers breaking into the IT industry, and I hoped to do the same. After all, IT is one of the few industries out there where being creative and a quick learner is more important than a degree.

Understanding LAN Bridges -

LAN Bridges were used to separate and isolate multiple collision domains from each other in large broadcast domains. Bridges had two or more LAN ports to which other central devices, such as network Hubs, were connected via LAN cables. Unlike network Hubs that used to forward data packets to every PC that was connected to the ports, Bridges acted more like LAN Switches to identify destination ports and transferred the data packets only if the packets were destined to reach the segments that were connected to their other ends. Bridges used to calculate and identify the destination segments on the basis of physical (MAC) addresses of the central devices that were connected to their LAN ports.

Understanding DNS Updates & DNS Records -

DNS records are the objects that are created either manually by the DNS administrators or automatically by the DNS servers themselves. A DNS server can have indefinite numbers of records and each DNS record is helpful in resolving the query of its own type. For example a Host (A) record in DNS server helps resolving a hostname to its corresponding IPv4 address whereas Host (AAAA) record resolves hostname to its corresponding IPv6 addresses.

Understanding Star Topology -

Since over a decade, star topologies have been preferred over bus topologies by the administrators. In star topology, a central device (Hub or Switch) is used to connect multiple PCs in a local area network. Central devices that are used in star topologies have multiple LAN ports integrated in them and the PCs are connected to the central devices via patch cables. In most cases patch cables are twisted pair cables that have four twisted pairs (eight wires in all) which are crimped to the RJ-45 connectors. The reason why star topology is mostly preferred nowadays is that it does not provide a single point of failure and is highly scalable. This means ...

What if the Internet Went Down? -

Modern metropolises can't function without computers and the Internet. Water supply and electricity, mobile and telecommunications - all function with the help of the Internet. What would happen if it terminated? If the computer network or a system server failed, that would lead to devastating consequences for people and the economy. According to some estimates Internet crime brings more profit than drug related crime. Threats from the virtual space can go much further than home computers or work place computers.

Network Topologies - .
Ever wonder... how are all of these file, print, fax, and computer resources connected so as to allow the typical desktop computer to access them?
Network topology refers to the way
networked computers and network resources are connected. The three most widely used topologies are
bus,
ring, and
star. Note that the following
network topology diagrams are logical views of the
topologies they represent and don’t necessarily match the physical (electrical) interconnections on the networks.
D-Link Cloud Router DIR-605L -
.png)
This time we had the chance to try out a product from the Chinese firm
D-Link, a renowned manufacturer of computer networking equipment. It is a product that is called
Cloud Router and is classified by the marking
DIR-605L. In the package, next to the router, you get a
voltage adapter (5V DC, 1A),
LAN cable,
CD with instructions and software, as well as printed documentation.

IP Spoofing and Sniffing -
 Sniffing and spoofing
Sniffing and spoofing are security threats that target the lower layers of the
networking infrastructure supporting applications that use the Internet. Users do not interact directly with these lower layers and are typically completely unaware that they exist. Without a deliberate consideration of these threats, it is impossible to build effective security into the higher levels. Sniffing is a passive
security attack in which a machine separate from the intended destination reads data on a network. The term
"sniffing" comes from the notion of
"sniffing the ether" in an
Ethernet network and is a bad pun on the two meanings of the word
"ether." Passive
security attack are those that do not alter the normal flow of data on a communication link or inject data into the link.
Internet Backbone Speeds -
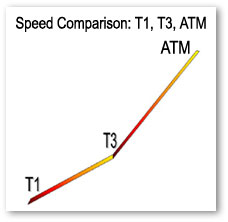
This is something that can come in handy for those of you who are simply curious about internet backbone speeds.
Understading Networking Hubs -

Network hubs were the central devices that network administrators used to use to establish a network setup using Star Topologies. Network hubs had multiple RJ-45 ports integrated in them and were used to connect one end of the LAN cables that had RJ-45 connectors crimped to them. The other end of the cables were connected to the RJ-45 ports available on the PCs. Network hubs were available with 4, 8, 16 and 24 ports. Administrators also used to cascade two hubs for larger network setups. Cascading means that one RJ-45 port of one hub connected to ...

Understanding Routers -

Routers are the devices that are used to connect two different networks in order to allow communication between them. Networks with different network IDs are considered to be different. By default, no communication can take place between two different networks, and this configuration prevents computers of one network from getting accessed by the computers on the other network, which may belong to another organization, building premises, home, etc.
History of TCP/IP -
 Internetworking
Internetworking with
TCP/IP has been around for many years-almost as many years as
Unix has been available.
TCP/IP, or
Transmission Control Protocol/Internet Protocol, grew out of the work that was done with the Defense Advanced Research Projects Agency, or
DARPA. In 1969, DARPA sponsored a project that became known as the
ARPANET. This network mainly provided high-bandwidth connectivity between the major
computing sites in government, educational, and research laboratories.

Understanding Collision and Broadcast Domains -

In computer networks, scope (area) up to where data that is transferred over the cables or the wireless media with certain conditions is categorized in two domain main types. In complex network setups, because multiple segments are connected to each other via different types of central devices, it becomes important for the administrators to separate broadcast domains and reduce the numbers of collision domains. A central device in which collisions may occur is Hub because of it logical Bus Topology.
Understanding DNS Zones -

When a DNS server role is installed on a network operating system, by default forward lookup zone is automatically created and the DNS server works as Caching Only server that caches the results of all the queries that it resolves. Forward lookup zone of a DNS server resolves IP addresses to their corresponding host names, is used in most network setups in production environments.

IT College Program vs. IT Boot Camp -

Perhaps it is time for a career change, or you are fresh out of high school and the idea of four more years of schooling does not appeal to you. After much research you have decided to embark upon a career in the Information Technology field. Not a bad choice, especially since Technology changes every day.
You are faced with the choice of education. As previously stated, going to
computer school for four years to get a
computer science degree is not an option but there is another option,
IT Boot Camp. And
IT Boot Camps solely focus on a very limited number of IT Certifications. So there can be
MCSE Boot Camps that may focus on just that.

How to Connect Two Laptops Using Bluetooth -

Do you need to copy a heavy file from another laptop without using pen drive or connecting cables? Of course, this can be done by using electronic transfer methods like ftp or online data storage systems. However, these methods are not only time consuming, they often lead to increased data transfer costs. Moreover, what if there is no internet connectivity available in the immediate vicinity? Under such circumstances, you can connect two laptops through Bluetooth and exchange files seamlessly.

227 Categorized CompTIA A Plus Q and A -
CompTIA
A+ Certification is widely recognized as the first
certification you should receive in an
information technology (IT) career. Whether you are planning to specialize in
PC hardware, Windows operating system management, or
network management, the
CompTIA A+ Certification exams measure the baseline skills you need to master in order to begin your journey toward greater responsibilities and achievements in
information technology.
CompTIA A+ Certification is designed to be a "vendor-neutral" exam that measures your knowledge of industry-standard technology.

Understanding Virtualization Concepts -

Virtualization is a process in which a physical computer a.k.a. host computer contains virtual machines that are stored in them in form of files. These virtual machines act exactly the way the physical computers do and can be mapped with the NICs of the host computers. Once mapped, the operating systems installed inside the virtual machines (Guest Operating Systems) can then communicate with the host computers as well as the network setups to which the host computers might be connected.
Network Plus Certification Exam -

This tutorial can be thought of as God sent. It will not only get you through Network+ Exam but is very hand resource for all those of you who are already in the networking field. Don't leave home without it!
Understanding Firewalls -

A firewall can be thought of as a gatekeeper who has been handed over a list of people whom he must allow to enter into the premises and/or the list of those people whose request to enter the premises must be denied straightforward. Just like the role of a gatekeeper, a firewall monitors incoming and outgoing network traffic to and from a computer system and allows or denies the communication of the computer with other computers that are connected to it via Local Area Network (LAN). Since in network communication, the packets are transported over the cable or through wireless media, a firewall allows or denies the communication on the basis of source ...

Understanding DHCP Classes -

In small-scale organizations and home environments, DHCP servers are installed normally and no class oriented configurations are done. The reason behind this is that by default all DHCP client computers belong to default DHCP class and as soon as DHCP scopes are configured and the DHCP servers become ready to assign dynamic addresses to the client computers, the DHCP clients start receiving the IP addresses without any additional administrative overheads. However, in order to allow DHCP servers to assign different ...
Understanding DHCP Servers -

Dynamic Host Configuration Protocol or DHCP servers are the dedicated computers that have network operating systems installed on them and are responsible for providing automatic IP addresses to all the client computers that are configured to obtain the addresses automatically.
TW Tech Glossary - Misplaced your bible? Well here it is - Tech Glosasary! This truly took a while to complete and should be used by all from beginners to advance techies.
IT Certifications a Solid Return On Investment -

Step into the realm of IT Certifications. Where millions have entered and zillions have flunked. Ah, that didnt sound right, mathematically speaking that is. Anyway, if your one of the few breeds that like to get your hands on a certification and get ahead in your work place, it is strongly recommended that you read this article. Its not made with grueling details and gets right down to the point. So check it out, you probably owe it to yourself by now!
Beginner Computer Training FAQ -

Use the webs best resource to find computer and technical training schools near you. Choose from hundreds of schools offering Classroom, Corporate, Onsite, and Online programs.
Understanding LAN Switches -

LAN switches, which are also sometimes called intelligent hubs, are the networking devices that have completely dominated and replaced Hubs. The reason behind this is that unlike Hubs, that only used to regenerate the received packets and forward them to all the ports that they had, LAN switches create one-to-one virtual circuits directly to the ports to which the destination computers are connected. This reduces the time consumed while transferring the data packets from the source computers to the destination ones.

Understanding Wireless Network Topologies -

In any network setup, network topology plays an important role without which network cannot be established whatsoever. In other words, whenever two or more machines are connected to each other, a topology is automatically formed. Unlike wired networks that have multiple topologies, wireless networks have only two topologies namely Infrastructure and Ad Hoc. Since wireless networks work on unguided media, it makes sense to have limited number of topologies while configuring the wireless network setups. Moreover, since wireless networks are a bit complicated configure as compared to the wired networks, it is essential for the administrators to have ...

Understanding Ring Topology -

In ring topology, data used to transfer in the form of ring where every computer that was connected to the network had two LAN cards and each LAN card was connected to the LAN card of its neighbor computer. Many times ring topology was preferred over bus topology because there were no collisions and the chances of network getting congested were next to 0%.
Physical Network Devices -
.jpg)
In collective network topology it may happen that two users that are connected to opposite ends with a closer can not communicate because the digital signal is distorted over time and is not as recognizable. Therefore, a device is inserted that has two-way communication and performs restoration of digital signals.
Selecting the Best Computer Science Field -

If you are looking for career counseling, and are in a dilemma as which branch of computer science you should go for, this small section would hopefully help you in selecting the best option according to your nature and interest. In computer industry, there are several branches from which you can choose any one. The reason behind this is that in this industry, you can get success and/or fame only when you are skilled, and full of knowledge.

Getting Into IT - No Experience No Qualification -
 But how?
But how? If you have computer skill but no experience (
or qualifications), the employment agencies will tell you the same old line,
"You need experience before anyone will look at you."
It's just plain old Catch-22. You need the work to get the experience but you can't get that first job to give you a track record and therefore verifiable experience. With this logic, it amazes me that anyone actually gets into IT!
Qualifications help but even that is no guarantee nowadays of getting an IT Job. And what do you do when you don't have qualifications but you want to start now? I mean right now, not 3 months later after you've paid a fortune for certification and given up your job to have enough study time.
All is not lost. You have two alternatives.

What REAL Computer People Need To Know -

A great deal of fundamental understanding about computers has been mostly lost from our world today. Computers are so complicated and work so reliably nowadays that many of the finer aspects of computing are now little more than dim memories in the minds of some older hackers, or little-read publications gathering dust in libraries somewhere. People often try to get away with knowing as little as they can, and while they might be able to get away with that, it's distressing how many people who believe themselves to be knowledgeable about computers are actually unaware of some highly fundamental concepts.

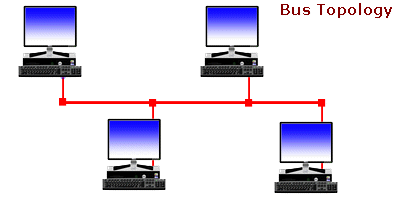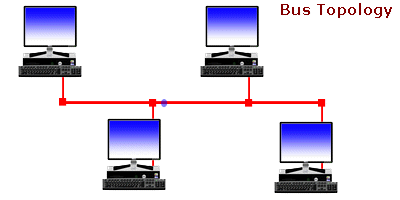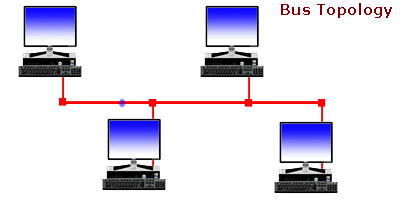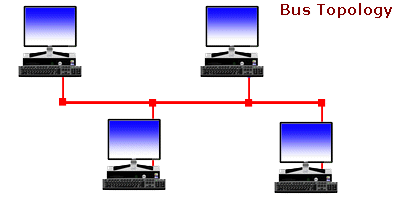
Understanding Bus Topology -

n a nutshell, network topologies are the physical alignments of computers and the way they are connected to each other. For example, if all the computers are connected to each other via a central device (Hub or Switch), the type of topology is Star. Likewise, if all the computers are connected to each other via a main cable, this means it is Bus Topology.
What is Computer Networking?
 A network is a collection of connected intelligent computing devices. The connection is not necessarily a fancy one. A connection between two computers by direct cabling is qualified to be a network. By this definition, a workstation which is loaded with a computer, a scanner, and a printer, is not treated as a network.
A network is a collection of connected intelligent computing devices. The connection is not necessarily a fancy one. A connection between two computers by direct cabling is qualified to be a network. By this definition, a workstation which is loaded with a computer, a scanner, and a printer, is not treated as a network.
A network can consist of two computers connected together on a desk or it can consist of many Local Area Networks (LANs) connected together to form a Wide Area Network (WAN) across a continent. The key is that two or more computers are connected together by a medium and are sharing resources. These resources can be files, printers, hard?drives, or CPU number-crunching power.
A Local Area Network (LAN) is a smaller network within one location or between several buildings A Metropolitan Network (MAN, politically incorrect, no WOMAN!) is a midsize network spanning the city. A Wide Area Network (WAN) is a giant network spanning across several cities or even several continents.
Tips
What is the maximum number of computers on a LAN in the Star Topology?
100
1024
144
Unlimited
The correct answer is 1024.
A star topology supports up to 1024 computers on the LAN.
NTFS stands for:
Networking Technology File System
New Technology File System
Network Transfer File System
None of the Above
Answer: NTFS stands for New Technology File System
NTFS is the file system Windows NT uses. It is a transaction based file system that is native to Windows NT.
NetBEUI is Routable:
True
False
The answer is False.
NetBEUI is not routable
Which type of fault tolerance duplicates data from one partition to another?
Striping
Duplicating
Mirroring
Active backup
The correct answer is mirroring.
Mirroring is a method of fault tolerance, which duplicates data on one partition to another.
What does OSI stand for?
Operating System Intelligence
Open Systems Integration
Operating Systems Interaction
Open Systems Interconnections
OSI stands for Open Systems Interconnections
The OSI Reference Model is the basic concept for networking
WWW is a popular protocol on which layer in the OSI Reference Model?
Presentation
Application
Internet
Session
WWW is a protocol on the Application layer.
The Application Layer is the layer at which software programs communicate with each other and establish communication.
Which layer in the OSI Reference Model is responsible for addressing and routing data through an internetwork?
Presentation
Network
Data Link
Physical
The correct answer is the Network layer.
The Network layer is responsible for addressing and routing data.
What are the corresponding devices in the Data Link layer of the OSI Reference Model?
Routers and Repeaters
Gateways
Hubs and Repeaters
Bridges and Switches
The correct answer is Bridges and Switches.
The Data Link layer has the corresponding devices of Bridges and Switches.
What is the maximum data transfer speed for CAT 5 cable?
10 Mbps
100 Mbps
500 Mbps
No limitations for CAT 5 cable
The correct answer is 100 Mbps.
CAT 5 Cable is data grade cable; four twisted pairs and can sustain transfer rates up to 100 Mbps.
What is the maximum distance for fiber optic cable?
100 meters
5 km
25 km
No limitations for fiber optic cable
The correct answer is 25 km.
The maximum distance for fiber optic cable is 25 km.
|
|
|
|
 Did You Know?
- Peer to Peer networking was around even 30 years ago.
- Internet itself has evolved from the basic home networking.

|
|
|
|
|
|











































![]() A network is a collection of connected intelligent computing devices. The connection is not necessarily a fancy one. A connection between two computers by direct cabling is qualified to be a network. By this definition, a workstation which is loaded with a computer, a scanner, and a printer, is not treated as a network.
A network is a collection of connected intelligent computing devices. The connection is not necessarily a fancy one. A connection between two computers by direct cabling is qualified to be a network. By this definition, a workstation which is loaded with a computer, a scanner, and a printer, is not treated as a network.
 In this article, we would like to point out the obvious IT Jobs that at times get overlooked. Find out what's out there and which information technology is the right choice for you. From people that create laptop computers to folks that do web design to developers that come up with computer software concepts from scratch. Also a bit at the end about
In this article, we would like to point out the obvious IT Jobs that at times get overlooked. Find out what's out there and which information technology is the right choice for you. From people that create laptop computers to folks that do web design to developers that come up with computer software concepts from scratch. Also a bit at the end about  A VLAN is a grouping of computers that is logically segmented by functions, project teams, or applications without regard to the physical location of users. Similar to routers, VLANs offer an effective mechanism for setting up firewalls in a switch fabric, protecting the network against broadcast problems that are potentially dangerous, and maintaining all the performance benefits of switching. You can create these firewalls by assigning switch ports or users to specific VLAN groups in single switches and across multiple connected switches, which will increase security easily and inexpensively by segmenting the network.
A VLAN is a grouping of computers that is logically segmented by functions, project teams, or applications without regard to the physical location of users. Similar to routers, VLANs offer an effective mechanism for setting up firewalls in a switch fabric, protecting the network against broadcast problems that are potentially dangerous, and maintaining all the performance benefits of switching. You can create these firewalls by assigning switch ports or users to specific VLAN groups in single switches and across multiple connected switches, which will increase security easily and inexpensively by segmenting the network.  We all know that we need more bandwidth now, than we ever did in the past. There tons more online games, online movies, online collab work, you name it. And the past standards of Wifi namely 802.11a, 802.11b, 802.11g, 802.11n, and so on) were getting better and better; however, the 802.11ac does the trick. Well, atleast for now it is, until something better comes along.
We all know that we need more bandwidth now, than we ever did in the past. There tons more online games, online movies, online collab work, you name it. And the past standards of Wifi namely 802.11a, 802.11b, 802.11g, 802.11n, and so on) were getting better and better; however, the 802.11ac does the trick. Well, atleast for now it is, until something better comes along. Domain Name System or DNS servers are dedicated computers that have network operating systems installed on them and are responsible for resolving hostnames (computer names) to their IP addresses and vice versa. DNS servers are used worldwide and are helpful while accessing the Internet and visiting websites. Every Internet Service Provider or ISP has its own DNS server which receives name resolution requests from the subscribers of that ISP and resolves the requested host names to their corresponding IP addresses.
Domain Name System or DNS servers are dedicated computers that have network operating systems installed on them and are responsible for resolving hostnames (computer names) to their IP addresses and vice versa. DNS servers are used worldwide and are helpful while accessing the Internet and visiting websites. Every Internet Service Provider or ISP has its own DNS server which receives name resolution requests from the subscribers of that ISP and resolves the requested host names to their corresponding IP addresses. Apart from star topology that is widely used in almost every network environment, the other type of topology that is complex while setting up but provides 100% fault tolerance to the network is Mesh Topology. In this topology, every computer that has to be connected to the network is connected to every computer that is available in the network. For example if there are four computers namely A, B, C and D, then A will be connected to B, C and D. Likewise B will be connected to A, C and D and so on. This means that when mesh topology is used while establishing a network setup, it is very unlikely that the network would ever face congestions or would ever fail.
Apart from star topology that is widely used in almost every network environment, the other type of topology that is complex while setting up but provides 100% fault tolerance to the network is Mesh Topology. In this topology, every computer that has to be connected to the network is connected to every computer that is available in the network. For example if there are four computers namely A, B, C and D, then A will be connected to B, C and D. Likewise B will be connected to A, C and D and so on. This means that when mesh topology is used while establishing a network setup, it is very unlikely that the network would ever face congestions or would ever fail. One of most important type of server is cluster servers. Software that enables clustering of servers is installed into a computer. Clustering servers also serve as load balancing servers between two computers. This is a common small business server. Clustering servers are used to avoid server failover. Server failover is the capability to shift to another standby server if the main server fails.
One of most important type of server is cluster servers. Software that enables clustering of servers is installed into a computer. Clustering servers also serve as load balancing servers between two computers. This is a common small business server. Clustering servers are used to avoid server failover. Server failover is the capability to shift to another standby server if the main server fails. Ever heard of OSI? Know what it is fully? No? Well what are you waiting for? Get cracking this week on the 7 Layers of the OSI Model. So that the next time the topic comes up, you'll have a clue. OSI short for Open System Interconnection, an ISO standard for worldwide communications that defines a networking framework for implementing protocols in seven layers. ISO shorts for International Organization for Standardization.
Ever heard of OSI? Know what it is fully? No? Well what are you waiting for? Get cracking this week on the 7 Layers of the OSI Model. So that the next time the topic comes up, you'll have a clue. OSI short for Open System Interconnection, an ISO standard for worldwide communications that defines a networking framework for implementing protocols in seven layers. ISO shorts for International Organization for Standardization. External hard disks are becoming an essential part of computer equipment whether it is business or user based computer systems. Except for the fact that they enable storing more data, they don't slow down your processor. External hard disks are connected with the computer using a USB cable. USB ports are now being placed in almost every computer. If you are buying a new computer make sure that....
External hard disks are becoming an essential part of computer equipment whether it is business or user based computer systems. Except for the fact that they enable storing more data, they don't slow down your processor. External hard disks are connected with the computer using a USB cable. USB ports are now being placed in almost every computer. If you are buying a new computer make sure that.... You wouldn't go to a doctor who had never been to medical school, or hire a lawyer who never studied law. One side-effect of a world advancing as rapidly as ours is that fields are becoming more and more specialized and narrow. People can no longer get by on general knowledge in their careers, something I found out for myself not too long ago. I'd been out of high school for two years, scraping by on my own and picking up scraps of programming as I went. I saw all of the self-taught programmers breaking into the IT industry, and I hoped to do the same. After all, IT is one of the few industries out there where being creative and a quick learner is more important than a degree.
You wouldn't go to a doctor who had never been to medical school, or hire a lawyer who never studied law. One side-effect of a world advancing as rapidly as ours is that fields are becoming more and more specialized and narrow. People can no longer get by on general knowledge in their careers, something I found out for myself not too long ago. I'd been out of high school for two years, scraping by on my own and picking up scraps of programming as I went. I saw all of the self-taught programmers breaking into the IT industry, and I hoped to do the same. After all, IT is one of the few industries out there where being creative and a quick learner is more important than a degree. LAN Bridges were used to separate and isolate multiple collision domains from each other in large broadcast domains. Bridges had two or more LAN ports to which other central devices, such as network Hubs, were connected via LAN cables. Unlike network Hubs that used to forward data packets to every PC that was connected to the ports, Bridges acted more like LAN Switches to identify destination ports and transferred the data packets only if the packets were destined to reach the segments that were connected to their other ends. Bridges used to calculate and identify the destination segments on the basis of physical (MAC) addresses of the central devices that were connected to their LAN ports.
LAN Bridges were used to separate and isolate multiple collision domains from each other in large broadcast domains. Bridges had two or more LAN ports to which other central devices, such as network Hubs, were connected via LAN cables. Unlike network Hubs that used to forward data packets to every PC that was connected to the ports, Bridges acted more like LAN Switches to identify destination ports and transferred the data packets only if the packets were destined to reach the segments that were connected to their other ends. Bridges used to calculate and identify the destination segments on the basis of physical (MAC) addresses of the central devices that were connected to their LAN ports. Since over a decade, star topologies have been preferred over bus topologies by the administrators. In star topology, a central device (Hub or Switch) is used to connect multiple PCs in a local area network. Central devices that are used in star topologies have multiple LAN ports integrated in them and the PCs are connected to the central devices via patch cables. In most cases patch cables are twisted pair cables that have four twisted pairs (eight wires in all) which are crimped to the RJ-45 connectors. The reason why star topology is mostly preferred nowadays is that it does not provide a single point of failure and is highly scalable. This means ...
Since over a decade, star topologies have been preferred over bus topologies by the administrators. In star topology, a central device (Hub or Switch) is used to connect multiple PCs in a local area network. Central devices that are used in star topologies have multiple LAN ports integrated in them and the PCs are connected to the central devices via patch cables. In most cases patch cables are twisted pair cables that have four twisted pairs (eight wires in all) which are crimped to the RJ-45 connectors. The reason why star topology is mostly preferred nowadays is that it does not provide a single point of failure and is highly scalable. This means ... Modern metropolises can't function without computers and the Internet. Water supply and electricity, mobile and telecommunications - all function with the help of the Internet. What would happen if it terminated? If the computer network or a system server failed, that would lead to devastating consequences for people and the economy. According to some estimates Internet crime brings more profit than drug related crime. Threats from the virtual space can go much further than home computers or work place computers.
Modern metropolises can't function without computers and the Internet. Water supply and electricity, mobile and telecommunications - all function with the help of the Internet. What would happen if it terminated? If the computer network or a system server failed, that would lead to devastating consequences for people and the economy. According to some estimates Internet crime brings more profit than drug related crime. Threats from the virtual space can go much further than home computers or work place computers. This very much to the point guide highlights some important networking terms and topics and simplifies them to us, the mere mortals.
This very much to the point guide highlights some important networking terms and topics and simplifies them to us, the mere mortals. Ever wonder... how are all of these file, print, fax, and computer resources connected so as to allow the typical desktop computer to access them? Network topology refers to the way
Ever wonder... how are all of these file, print, fax, and computer resources connected so as to allow the typical desktop computer to access them? Network topology refers to the way .png) This time we had the chance to try out a product from the Chinese firm D-Link, a renowned manufacturer of computer networking equipment. It is a product that is called Cloud Router and is classified by the marking DIR-605L. In the package, next to the router, you get a voltage adapter (5V DC, 1A), LAN cable, CD with instructions and software, as well as printed documentation.
This time we had the chance to try out a product from the Chinese firm D-Link, a renowned manufacturer of computer networking equipment. It is a product that is called Cloud Router and is classified by the marking DIR-605L. In the package, next to the router, you get a voltage adapter (5V DC, 1A), LAN cable, CD with instructions and software, as well as printed documentation. Sniffing and spoofing are security threats that target the lower layers of the
Sniffing and spoofing are security threats that target the lower layers of the  This is something that can come in handy for those of you who are simply curious about internet backbone speeds.
This is something that can come in handy for those of you who are simply curious about internet backbone speeds. Network hubs were the central devices that network administrators used to use to establish a network setup using Star Topologies. Network hubs had multiple RJ-45 ports integrated in them and were used to connect one end of the LAN cables that had RJ-45 connectors crimped to them. The other end of the cables were connected to the RJ-45 ports available on the PCs. Network hubs were available with 4, 8, 16 and 24 ports. Administrators also used to cascade two hubs for larger network setups. Cascading means that one RJ-45 port of one hub connected to ...
Network hubs were the central devices that network administrators used to use to establish a network setup using Star Topologies. Network hubs had multiple RJ-45 ports integrated in them and were used to connect one end of the LAN cables that had RJ-45 connectors crimped to them. The other end of the cables were connected to the RJ-45 ports available on the PCs. Network hubs were available with 4, 8, 16 and 24 ports. Administrators also used to cascade two hubs for larger network setups. Cascading means that one RJ-45 port of one hub connected to ... Routers are the devices that are used to connect two different networks in order to allow communication between them. Networks with different network IDs are considered to be different. By default, no communication can take place between two different networks, and this configuration prevents computers of one network from getting accessed by the computers on the other network, which may belong to another organization, building premises, home, etc.
Routers are the devices that are used to connect two different networks in order to allow communication between them. Networks with different network IDs are considered to be different. By default, no communication can take place between two different networks, and this configuration prevents computers of one network from getting accessed by the computers on the other network, which may belong to another organization, building premises, home, etc.
 In computer networks, scope (area) up to where data that is transferred over the cables or the wireless media with certain conditions is categorized in two domain main types. In complex network setups, because multiple segments are connected to each other via different types of central devices, it becomes important for the administrators to separate broadcast domains and reduce the numbers of collision domains. A central device in which collisions may occur is Hub because of it logical Bus Topology.
In computer networks, scope (area) up to where data that is transferred over the cables or the wireless media with certain conditions is categorized in two domain main types. In complex network setups, because multiple segments are connected to each other via different types of central devices, it becomes important for the administrators to separate broadcast domains and reduce the numbers of collision domains. A central device in which collisions may occur is Hub because of it logical Bus Topology. Perhaps it is time for a career change, or you are fresh out of high school and the idea of four more years of schooling does not appeal to you. After much research you have decided to embark upon a career in the Information Technology field. Not a bad choice, especially since Technology changes every day.
You are faced with the choice of education. As previously stated, going to computer school for four years to get a computer science degree is not an option but there is another option, IT Boot Camp. And IT Boot Camps solely focus on a very limited number of IT Certifications. So there can be MCSE Boot Camps that may focus on just that.
Perhaps it is time for a career change, or you are fresh out of high school and the idea of four more years of schooling does not appeal to you. After much research you have decided to embark upon a career in the Information Technology field. Not a bad choice, especially since Technology changes every day.
You are faced with the choice of education. As previously stated, going to computer school for four years to get a computer science degree is not an option but there is another option, IT Boot Camp. And IT Boot Camps solely focus on a very limited number of IT Certifications. So there can be MCSE Boot Camps that may focus on just that. Do you need to copy a heavy file from another laptop without using pen drive or connecting cables? Of course, this can be done by using electronic transfer methods like ftp or online data storage systems. However, these methods are not only time consuming, they often lead to increased data transfer costs. Moreover, what if there is no internet connectivity available in the immediate vicinity? Under such circumstances, you can connect two laptops through Bluetooth and exchange files seamlessly.
Do you need to copy a heavy file from another laptop without using pen drive or connecting cables? Of course, this can be done by using electronic transfer methods like ftp or online data storage systems. However, these methods are not only time consuming, they often lead to increased data transfer costs. Moreover, what if there is no internet connectivity available in the immediate vicinity? Under such circumstances, you can connect two laptops through Bluetooth and exchange files seamlessly. CompTIA A+ Certification is widely recognized as the first certification you should receive in an information technology (IT) career. Whether you are planning to specialize in PC hardware, Windows operating system management, or network management, the
CompTIA A+ Certification is widely recognized as the first certification you should receive in an information technology (IT) career. Whether you are planning to specialize in PC hardware, Windows operating system management, or network management, the  Virtualization is a process in which a physical computer a.k.a. host computer contains virtual machines that are stored in them in form of files. These virtual machines act exactly the way the physical computers do and can be mapped with the NICs of the host computers. Once mapped, the operating systems installed inside the virtual machines (Guest Operating Systems) can then communicate with the host computers as well as the network setups to which the host computers might be connected.
Virtualization is a process in which a physical computer a.k.a. host computer contains virtual machines that are stored in them in form of files. These virtual machines act exactly the way the physical computers do and can be mapped with the NICs of the host computers. Once mapped, the operating systems installed inside the virtual machines (Guest Operating Systems) can then communicate with the host computers as well as the network setups to which the host computers might be connected. This tutorial can be thought of as God sent. It will not only get you through Network+ Exam but is very hand resource for all those of you who are already in the networking field. Don't leave home without it!
This tutorial can be thought of as God sent. It will not only get you through Network+ Exam but is very hand resource for all those of you who are already in the networking field. Don't leave home without it! In small-scale organizations and home environments, DHCP servers are installed normally and no class oriented configurations are done. The reason behind this is that by default all DHCP client computers belong to default DHCP class and as soon as DHCP scopes are configured and the DHCP servers become ready to assign dynamic addresses to the client computers, the DHCP clients start receiving the IP addresses without any additional administrative overheads. However, in order to allow DHCP servers to assign different ...
In small-scale organizations and home environments, DHCP servers are installed normally and no class oriented configurations are done. The reason behind this is that by default all DHCP client computers belong to default DHCP class and as soon as DHCP scopes are configured and the DHCP servers become ready to assign dynamic addresses to the client computers, the DHCP clients start receiving the IP addresses without any additional administrative overheads. However, in order to allow DHCP servers to assign different ... Step into the realm of IT Certifications. Where millions have entered and zillions have flunked. Ah, that didnt sound right, mathematically speaking that is. Anyway, if your one of the few breeds that like to get your hands on a certification and get ahead in your work place, it is strongly recommended that you read this article. Its not made with grueling details and gets right down to the point. So check it out, you probably owe it to yourself by now!
Step into the realm of IT Certifications. Where millions have entered and zillions have flunked. Ah, that didnt sound right, mathematically speaking that is. Anyway, if your one of the few breeds that like to get your hands on a certification and get ahead in your work place, it is strongly recommended that you read this article. Its not made with grueling details and gets right down to the point. So check it out, you probably owe it to yourself by now! Use the webs best resource to find computer and technical training schools near you. Choose from hundreds of schools offering Classroom, Corporate, Onsite, and Online programs.
Use the webs best resource to find computer and technical training schools near you. Choose from hundreds of schools offering Classroom, Corporate, Onsite, and Online programs. LAN switches, which are also sometimes called intelligent hubs, are the networking devices that have completely dominated and replaced Hubs. The reason behind this is that unlike Hubs, that only used to regenerate the received packets and forward them to all the ports that they had, LAN switches create one-to-one virtual circuits directly to the ports to which the destination computers are connected. This reduces the time consumed while transferring the data packets from the source computers to the destination ones.
LAN switches, which are also sometimes called intelligent hubs, are the networking devices that have completely dominated and replaced Hubs. The reason behind this is that unlike Hubs, that only used to regenerate the received packets and forward them to all the ports that they had, LAN switches create one-to-one virtual circuits directly to the ports to which the destination computers are connected. This reduces the time consumed while transferring the data packets from the source computers to the destination ones. In any network setup, network topology plays an important role without which network cannot be established whatsoever. In other words, whenever two or more machines are connected to each other, a topology is automatically formed. Unlike wired networks that have multiple topologies, wireless networks have only two topologies namely Infrastructure and Ad Hoc. Since wireless networks work on unguided media, it makes sense to have limited number of topologies while configuring the wireless network setups. Moreover, since wireless networks are a bit complicated configure as compared to the wired networks, it is essential for the administrators to have ...
In any network setup, network topology plays an important role without which network cannot be established whatsoever. In other words, whenever two or more machines are connected to each other, a topology is automatically formed. Unlike wired networks that have multiple topologies, wireless networks have only two topologies namely Infrastructure and Ad Hoc. Since wireless networks work on unguided media, it makes sense to have limited number of topologies while configuring the wireless network setups. Moreover, since wireless networks are a bit complicated configure as compared to the wired networks, it is essential for the administrators to have ... In ring topology, data used to transfer in the form of ring where every computer that was connected to the network had two LAN cards and each LAN card was connected to the LAN card of its neighbor computer. Many times ring topology was preferred over bus topology because there were no collisions and the chances of network getting congested were next to 0%.
In ring topology, data used to transfer in the form of ring where every computer that was connected to the network had two LAN cards and each LAN card was connected to the LAN card of its neighbor computer. Many times ring topology was preferred over bus topology because there were no collisions and the chances of network getting congested were next to 0%..jpg) In collective network topology it may happen that two users that are connected to opposite ends with a closer can not communicate because the digital signal is distorted over time and is not as recognizable. Therefore, a device is inserted that has two-way communication and performs restoration of digital signals.
In collective network topology it may happen that two users that are connected to opposite ends with a closer can not communicate because the digital signal is distorted over time and is not as recognizable. Therefore, a device is inserted that has two-way communication and performs restoration of digital signals. If you are looking for career counseling, and are in a dilemma as which branch of computer science you should go for, this small section would hopefully help you in selecting the best option according to your nature and interest. In computer industry, there are several branches from which you can choose any one. The reason behind this is that in this industry, you can get success and/or fame only when you are skilled, and full of knowledge.
If you are looking for career counseling, and are in a dilemma as which branch of computer science you should go for, this small section would hopefully help you in selecting the best option according to your nature and interest. In computer industry, there are several branches from which you can choose any one. The reason behind this is that in this industry, you can get success and/or fame only when you are skilled, and full of knowledge. But how? If you have computer skill but no experience (or qualifications), the employment agencies will tell you the same old line, "You need experience before anyone will look at you."
But how? If you have computer skill but no experience (or qualifications), the employment agencies will tell you the same old line, "You need experience before anyone will look at you."
 A great deal of fundamental understanding about computers has been mostly lost from our world today. Computers are so complicated and work so reliably nowadays that many of the finer aspects of computing are now little more than dim memories in the minds of some older hackers, or little-read publications gathering dust in libraries somewhere. People often try to get away with knowing as little as they can, and while they might be able to get away with that, it's distressing how many people who believe themselves to be knowledgeable about computers are actually unaware of some highly fundamental concepts.
A great deal of fundamental understanding about computers has been mostly lost from our world today. Computers are so complicated and work so reliably nowadays that many of the finer aspects of computing are now little more than dim memories in the minds of some older hackers, or little-read publications gathering dust in libraries somewhere. People often try to get away with knowing as little as they can, and while they might be able to get away with that, it's distressing how many people who believe themselves to be knowledgeable about computers are actually unaware of some highly fundamental concepts. n a nutshell, network topologies are the physical alignments of computers and the way they are connected to each other. For example, if all the computers are connected to each other via a central device (Hub or Switch), the type of topology is Star. Likewise, if all the computers are connected to each other via a main cable, this means it is Bus Topology.
n a nutshell, network topologies are the physical alignments of computers and the way they are connected to each other. For example, if all the computers are connected to each other via a central device (Hub or Switch), the type of topology is Star. Likewise, if all the computers are connected to each other via a main cable, this means it is Bus Topology.
