Articles & Tutorials
 External hard disks are becoming an essential part of computer equipment whether it is business or user based computer systems. Except for the fact that they enable storing more data, they don't slow down your processor. External hard disks are connected with the computer using a USB cable. USB ports are now being placed in almost every computer. If you are buying a new computer make sure that....
External hard disks are becoming an essential part of computer equipment whether it is business or user based computer systems. Except for the fact that they enable storing more data, they don't slow down your processor. External hard disks are connected with the computer using a USB cable. USB ports are now being placed in almost every computer. If you are buying a new computer make sure that....
 If you are using Android, BlackBerry or Apple as a phone, you can print whatever you like on your printer no matter where you are. You need to have an installed Cloud print application on your mobile phone.
If you are using Android, BlackBerry or Apple as a phone, you can print whatever you like on your printer no matter where you are. You need to have an installed Cloud print application on your mobile phone.
 InDesign is actually the successor to the Adobe PageMaker that the company Adobe bought from Aldus in 1994. A few years later, in 1998., PageMaker lost almost the complete market by QuarkXPress that was the most popular program for Desktop Publishing. To make things more interesting, the company Quark offered to buy Adobe, but Adobe refused that offer and continued with the development of the PageMaker.
InDesign is actually the successor to the Adobe PageMaker that the company Adobe bought from Aldus in 1994. A few years later, in 1998., PageMaker lost almost the complete market by QuarkXPress that was the most popular program for Desktop Publishing. To make things more interesting, the company Quark offered to buy Adobe, but Adobe refused that offer and continued with the development of the PageMaker.
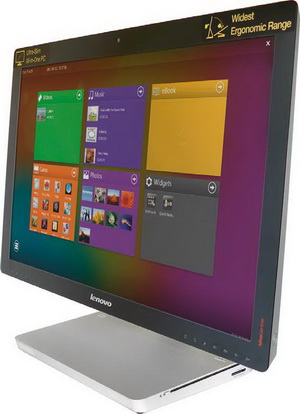 All-in-one computers with touch screen seem to be becoming the future of this type of home computer, and with the appearance of the new Windows, their usability has reached the level of a competitive firm that, next to OS, puts its name on hardware. On this test we had an impressive computer with the most advanced options for multitouch using. The Lenovo IdeaCentre A720 was designed and conceived to make a great first impression.
All-in-one computers with touch screen seem to be becoming the future of this type of home computer, and with the appearance of the new Windows, their usability has reached the level of a competitive firm that, next to OS, puts its name on hardware. On this test we had an impressive computer with the most advanced options for multitouch using. The Lenovo IdeaCentre A720 was designed and conceived to make a great first impression.
 Compressing PDF files will shrink its size without any information loss. In the following article you will find information that will guide you through the process of compressing PDF files. Don't upload documents with private information. It is not rare that sites that offer compression services keep a copy of your file for themselves.
Compressing PDF files will shrink its size without any information loss. In the following article you will find information that will guide you through the process of compressing PDF files. Don't upload documents with private information. It is not rare that sites that offer compression services keep a copy of your file for themselves.
 Do you feel frustrated every time you use your computer because it has really bad performance? Maybe you are thinking about buying a new computer even though it demands a lot of money and it will take away lots of time. Fortunately, there are techniques which you can use to prolong the life time of your computer and in that way avoid buying a new one.
Do you feel frustrated every time you use your computer because it has really bad performance? Maybe you are thinking about buying a new computer even though it demands a lot of money and it will take away lots of time. Fortunately, there are techniques which you can use to prolong the life time of your computer and in that way avoid buying a new one.
 Since Android was mostly based on the open source Linux project, many of the Linux tweaks and settings apply to the OS. You can make your Android device run faster, conserve more battery, play sound louder, and even change the theme, look and feel of the device. If you managed to get your device rooted, then you are ready to take full advantage of your Android hardware.
Since Android was mostly based on the open source Linux project, many of the Linux tweaks and settings apply to the OS. You can make your Android device run faster, conserve more battery, play sound louder, and even change the theme, look and feel of the device. If you managed to get your device rooted, then you are ready to take full advantage of your Android hardware.
 Although we talk about computing in a cloud, there is still a lot of work done on papers. The Sharp MX M354N will satisfy the needs of every office. No matter how much you resist it, digitalization is inevitable. Because of the ever growing business and chronic lack of time in employees, it is expected to get speed, quality print, low price and availability from multifunctional printers (MFP).
Although we talk about computing in a cloud, there is still a lot of work done on papers. The Sharp MX M354N will satisfy the needs of every office. No matter how much you resist it, digitalization is inevitable. Because of the ever growing business and chronic lack of time in employees, it is expected to get speed, quality print, low price and availability from multifunctional printers (MFP).
 When asked the question what graphic card to choose for a Linux machine users, experienced, but not sufficiently familiar with subject matter, will usually answer: "AMD for laptop, nVidia for desktop". Having in mind the lack of the support of the "vanilla" Linux kernel for the modern nVidia Optimus technology that enables the consistency of one integrated and another "discreet" graphic card in laptops, by which the more powerful one should "light up" only when the graphic and processor needs that, previous opinion have sense. But...
When asked the question what graphic card to choose for a Linux machine users, experienced, but not sufficiently familiar with subject matter, will usually answer: "AMD for laptop, nVidia for desktop". Having in mind the lack of the support of the "vanilla" Linux kernel for the modern nVidia Optimus technology that enables the consistency of one integrated and another "discreet" graphic card in laptops, by which the more powerful one should "light up" only when the graphic and processor needs that, previous opinion have sense. But...
 LG has recently made the new IPS7 monitor series available for testing, more precisely the 27 inch model that is called IPS277L. We are going to give more info, measures and our opinion here. Before all, this FullHD premium model brags about it's Cinema Screen design, but we will review it later in the text. The monitor comes pre-calibrated but has also got a colorimeter and if you want even more accurate calibration, it comes with an LG True Color Finder software. There is also a very useful thing called a MHL (Mobile High-definition Link) compatibility for connecting with smartphones or tablets.
LG has recently made the new IPS7 monitor series available for testing, more precisely the 27 inch model that is called IPS277L. We are going to give more info, measures and our opinion here. Before all, this FullHD premium model brags about it's Cinema Screen design, but we will review it later in the text. The monitor comes pre-calibrated but has also got a colorimeter and if you want even more accurate calibration, it comes with an LG True Color Finder software. There is also a very useful thing called a MHL (Mobile High-definition Link) compatibility for connecting with smartphones or tablets.

 Flash is a vector-based animation and interactivity program that allows you to create everything from simple animations to complex interactive applications. With its built-in programming language ActionScript Flash is fully scriptable and can communicate with several backend database languages. Since the first Flash product appeared (from Macromedia), the e-Learning community has worked with Flash developers and engineers to make Flash content more and more accessible in e-Learning environments.
Flash is a vector-based animation and interactivity program that allows you to create everything from simple animations to complex interactive applications. With its built-in programming language ActionScript Flash is fully scriptable and can communicate with several backend database languages. Since the first Flash product appeared (from Macromedia), the e-Learning community has worked with Flash developers and engineers to make Flash content more and more accessible in e-Learning environments.
 While you can find a lot of battery saving apps on Web, It is enough to just play a little with the settings of a smartphone to prolong the duration of the battery.
While you can find a lot of battery saving apps on Web, It is enough to just play a little with the settings of a smartphone to prolong the duration of the battery.It is enough to just play a little with the settings of a smartphone to prolong the duration of the battery on a daily basis for an hour. Most smartphone users struggle with their technological pets battery life.
No matter for what you use your smartphone, fun or work, the average battery life of 5 to 6 hours is simply not enough.
Because of that, a lot of people have to recharge their battery or use alternative solutions like a spare battery or a pocket charger.�While you can find a lot of battery saving apps on Google Play that promise to enhance your battery life, some simple adjustments can ensure up to an hour more of smartphone use.

 Here are our top five predictions for the next 12 months when it comes to Apple.
Here are our top five predictions for the next 12 months when it comes to Apple.In the first place, there is the Apple TV, because there are great chances that Apple will present an Apple TV in the following year. The equally important thing is the fact that Sirihas to get out of the Beta version. This software is turning one year now, and Apple has given it some new possibilities with iOS 6.

 CompTIA A+ Certification is widely recognized as the first certification you should receive in an information technology (IT) career. Whether you are planning to specialize in PC hardware, Windows operating system management, or network management, the CompTIA A+ Certification exams measure the baseline skills you need to master in order to begin your journey toward greater responsibilities and achievements in information technology.
CompTIA A+ Certification is widely recognized as the first certification you should receive in an information technology (IT) career. Whether you are planning to specialize in PC hardware, Windows operating system management, or network management, the CompTIA A+ Certification exams measure the baseline skills you need to master in order to begin your journey toward greater responsibilities and achievements in information technology.CompTIA A+ Certification is designed to be a "vendor-neutral" exam that measures your knowledge of industry-standard technology.

 The 26 best Google Adsense Tips and Tricks for earning more from Google adsense program. Strictly follow the rules/regulations mentioned in Adsense policies. Trying to cheat the adsense policies results in lifetime ban from adsense.
The 26 best Google Adsense Tips and Tricks for earning more from Google adsense program. Strictly follow the rules/regulations mentioned in Adsense policies. Trying to cheat the adsense policies results in lifetime ban from adsense.
 The tech-savvy should be well aware of the benefits of building their own personal computers. The relatively easy process of assembling various components can not only save you a boatload of money, but also supply you with the perfect rig for your individual needs. Whether you are updating a current machine or building a new one from scratch, the most important part you buy will probably be the motherboard. Involved in almost every major computing process, a motherboard can make or break your personal computer. However, technology is changing so rapidly that it's sometimes hard to know what's cutting edge and what's outdated. But, no matter what you're looking for, we've got you covered. Below are the three best motherboards of 2011, as determined by price, performance and durability. Since motherboards tend to be divided between Intel and AMD processors, a comparable board for the other processor is included in each category.
The tech-savvy should be well aware of the benefits of building their own personal computers. The relatively easy process of assembling various components can not only save you a boatload of money, but also supply you with the perfect rig for your individual needs. Whether you are updating a current machine or building a new one from scratch, the most important part you buy will probably be the motherboard. Involved in almost every major computing process, a motherboard can make or break your personal computer. However, technology is changing so rapidly that it's sometimes hard to know what's cutting edge and what's outdated. But, no matter what you're looking for, we've got you covered. Below are the three best motherboards of 2011, as determined by price, performance and durability. Since motherboards tend to be divided between Intel and AMD processors, a comparable board for the other processor is included in each category.
 3D Modeling and Animation: The Creative Profession of Computer Animation & Visual Effects, the Film Industry, the Companies, the Hardware, the Software. Ever dreamt of working for the film industry? You dont have to be an actor or a director to do so. Computer Animators share equally the glamour of a blockbusting creation.
3D Modeling and Animation: The Creative Profession of Computer Animation & Visual Effects, the Film Industry, the Companies, the Hardware, the Software. Ever dreamt of working for the film industry? You dont have to be an actor or a director to do so. Computer Animators share equally the glamour of a blockbusting creation. 
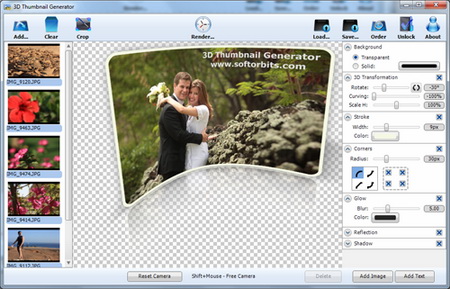 Thumbnail is a reduced display based on which you can have insight in the content that is represented through it. In the last century, more precisely the 80', the thumbnail became a term that refers to a preview of a graphic format on computers. The 3D Thumbnail Generator will make sure that your thumbnails are not just a copies of the original in very small form.
Thumbnail is a reduced display based on which you can have insight in the content that is represented through it. In the last century, more precisely the 80', the thumbnail became a term that refers to a preview of a graphic format on computers. The 3D Thumbnail Generator will make sure that your thumbnails are not just a copies of the original in very small form.
 This is the mother of all A+ FAQ's. With over 400 of the most frequently asked questions found on the net regarding the A+ Certification. Read, Think, Process, and Memorize.
This is the mother of all A+ FAQ's. With over 400 of the most frequently asked questions found on the net regarding the A+ Certification. Read, Think, Process, and Memorize.
 Human beings receive, process and retain any information in their memory through multiple senses in the real world. Similar phenomenon occurs in the virtual world of Internet as well. Since you cannot make use of senses like smell, taste and touch to influence people via internet, you must make the most of the "sight" and "hearing", so that people experience and perceive your products and services, the way you want them to. You guessed it right. Video marketing is the new buzzword.
Human beings receive, process and retain any information in their memory through multiple senses in the real world. Similar phenomenon occurs in the virtual world of Internet as well. Since you cannot make use of senses like smell, taste and touch to influence people via internet, you must make the most of the "sight" and "hearing", so that people experience and perceive your products and services, the way you want them to. You guessed it right. Video marketing is the new buzzword.
 If you're starting college and trying to choose your major, you may be wondering if computer science would be a good fit for you. You might be interested in computers and technology and good at math, for instance. Unfortunately, computer science is one of the most challenging and time-consuming majors, and you'll need more than just an interest in computers and math skills to achieve your academic goals. Succeeding as a computer science major requires that you have a number of soft skills.
If you're starting college and trying to choose your major, you may be wondering if computer science would be a good fit for you. You might be interested in computers and technology and good at math, for instance. Unfortunately, computer science is one of the most challenging and time-consuming majors, and you'll need more than just an interest in computers and math skills to achieve your academic goals. Succeeding as a computer science major requires that you have a number of soft skills.

 Content marketing or Inbound marketing is a term that applies to marketing strategies linked to the placement and distribution of content on the Internet. The goal of content marketing is the aim to make the company and its business more available to users of different services on the Internet, and in that way strengthen the awareness of the brand, present services and products and to secure the presence in the largest possible target group.
Content marketing or Inbound marketing is a term that applies to marketing strategies linked to the placement and distribution of content on the Internet. The goal of content marketing is the aim to make the company and its business more available to users of different services on the Internet, and in that way strengthen the awareness of the brand, present services and products and to secure the presence in the largest possible target group.
 A 60 GHz protocol is a network protocol that runs in a range that is close to 60 GHz, obviously. But, this is quite flexible as the range can go up to 64 and down to 57. If you compare other protocols like Wi-Fi or any other wireless protocol you will see that they are significantly lower (Wi-Fi is somewhere around 2-5 GHz). This major difference is what contributes to the problems and advantages in 60 GHz protocols.
A 60 GHz protocol is a network protocol that runs in a range that is close to 60 GHz, obviously. But, this is quite flexible as the range can go up to 64 and down to 57. If you compare other protocols like Wi-Fi or any other wireless protocol you will see that they are significantly lower (Wi-Fi is somewhere around 2-5 GHz). This major difference is what contributes to the problems and advantages in 60 GHz protocols.
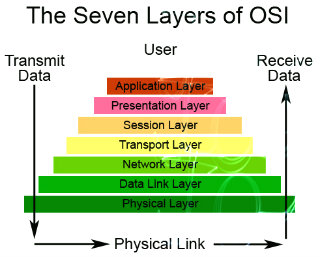 Ever heard of OSI? Know what it is fully? No? Well what are you waiting for? Get cracking this week on the 7 Layers of the OSI Model. So that the next time the topic comes up, you'll have a clue. OSI short for Open System Interconnection, an ISO standard for worldwide communications that defines a networking framework for implementing protocols in seven layers. ISO shorts for International Organization for Standardization.
Ever heard of OSI? Know what it is fully? No? Well what are you waiting for? Get cracking this week on the 7 Layers of the OSI Model. So that the next time the topic comes up, you'll have a clue. OSI short for Open System Interconnection, an ISO standard for worldwide communications that defines a networking framework for implementing protocols in seven layers. ISO shorts for International Organization for Standardization.
 This study guide provides an overview what you need to pass the exam 70-210 Installing, Configuring and Administering MS Windows 2000 Professional and summarize the skills required to install, configure and troubleshoot Windows 2000 Professional as a desktop operating system in a generic network-operating environment.
This study guide provides an overview what you need to pass the exam 70-210 Installing, Configuring and Administering MS Windows 2000 Professional and summarize the skills required to install, configure and troubleshoot Windows 2000 Professional as a desktop operating system in a generic network-operating environment.
 This study guide provides an overview what you need to pass the exam 70-215 Installing, Configuring and Administering MS Windows 2000 Server and summarize the skills required to install and configure Windows 2000 Server to participate as a member server of a domain in an Active directory environment.
This study guide provides an overview what you need to pass the exam 70-215 Installing, Configuring and Administering MS Windows 2000 Server and summarize the skills required to install and configure Windows 2000 Server to participate as a member server of a domain in an Active directory environment.

 This study guide provides an overview what you need to pass the exam 70-217 Implementing and Administering a MS Windows 2000 Directory Services Infrastructure and summarize the skills required to install, configure, and troubleshoot Active Directory and DNS for Active Directory, change and configuration management including RIS and Group Policy and Active Directory Security solutions.
This study guide provides an overview what you need to pass the exam 70-217 Implementing and Administering a MS Windows 2000 Directory Services Infrastructure and summarize the skills required to install, configure, and troubleshoot Active Directory and DNS for Active Directory, change and configuration management including RIS and Group Policy and Active Directory Security solutions.
 This study guide provides an overview what you need to pass the exam 70-221 designing a Microsoft Windows 2000 Network Infrastructure, which sheds light on the business aspects and technical requirements for creating a functional Windows 2000 network Infrastructure, including the description of administrative tasks in the Windows operating system.
This study guide provides an overview what you need to pass the exam 70-221 designing a Microsoft Windows 2000 Network Infrastructure, which sheds light on the business aspects and technical requirements for creating a functional Windows 2000 network Infrastructure, including the description of administrative tasks in the Windows operating system.
 When a business begins to grow, the next logical step is to set up a professional website. Whether you are looking for an international market or are trying to connect with your clients or customers; a professional website can ensure that your business is seen by the right people. Here are nine tips to consider when choosing a company to host your business' website.
When a business begins to grow, the next logical step is to set up a professional website. Whether you are looking for an international market or are trying to connect with your clients or customers; a professional website can ensure that your business is seen by the right people. Here are nine tips to consider when choosing a company to host your business' website.
 This is a well written little guide by our friends at Pro Profs. It has almost everything you need to know to get prepared for the A+ Exam.
This is a well written little guide by our friends at Pro Profs. It has almost everything you need to know to get prepared for the A+ Exam.
 Don't you hate it when you open Windows Explorer in Windows 2000 or XP, and you have to sift through all sorts of drives and folders to get to the location you want? Wouldn't it be easier if Windows Explorer would automatically open to that location? It would be easier, and it can be done. As I'll show you, Windows Explorer's default location can be changed to whatever location you want.
Don't you hate it when you open Windows Explorer in Windows 2000 or XP, and you have to sift through all sorts of drives and folders to get to the location you want? Wouldn't it be easier if Windows Explorer would automatically open to that location? It would be easier, and it can be done. As I'll show you, Windows Explorer's default location can be changed to whatever location you want.
 Ever wanted a full featured Active X document thats not as thick as a bible but gets you all the nifty little information you need? Well read this tutorial, you wont go back.
Ever wanted a full featured Active X document thats not as thick as a bible but gets you all the nifty little information you need? Well read this tutorial, you wont go back.
 Shortcuts are combinations of keys that give you fast access to command's, font's, symbol's, style's and macro's. A lot of shortcuts are built into Word. If you are using Microsoft Office Word for something a bit more complex than writing letters you are probably spending a lot of time opening menus, choosing commands and options in the dialog frames. Wouldn't it be more efficient work if you could use simple button combinations?
Shortcuts are combinations of keys that give you fast access to command's, font's, symbol's, style's and macro's. A lot of shortcuts are built into Word. If you are using Microsoft Office Word for something a bit more complex than writing letters you are probably spending a lot of time opening menus, choosing commands and options in the dialog frames. Wouldn't it be more efficient work if you could use simple button combinations?

 We've got so much email from so many NT Admins that it's almost unbelievable why we haven't come up with a tutorial for them. This tutorial is scrictly for those admins who make it a habit to forget passwords. Enjoy!
We've got so much email from so many NT Admins that it's almost unbelievable why we haven't come up with a tutorial for them. This tutorial is scrictly for those admins who make it a habit to forget passwords. Enjoy!
 Each search engine has something called an algorithm which is the formula that each search engine uses to evaluate web pages and determine their relevance and value when crawling them for possible inclusion in their search engine. A crawler is the robot that browses all of these pages for the search engine. Let's take look at how Algorithm, Page Rank, Backlinks, Hyperlinks, and various other variables can benefit your website.
Each search engine has something called an algorithm which is the formula that each search engine uses to evaluate web pages and determine their relevance and value when crawling them for possible inclusion in their search engine. A crawler is the robot that browses all of these pages for the search engine. Let's take look at how Algorithm, Page Rank, Backlinks, Hyperlinks, and various other variables can benefit your website.
.jpg) This part of Advanced SEO Techniques will go over some of the most important elements that a page that hopes to get high esearch engine rankings needs. Make sure that you go through this section very carefully as each of these can have a dramatic impact on the rankings that your website will ultimately achieve. Don't focus solely on the for�home page, keywords and titles.
This part of Advanced SEO Techniques will go over some of the most important elements that a page that hopes to get high esearch engine rankings needs. Make sure that you go through this section very carefully as each of these can have a dramatic impact on the rankings that your website will ultimately achieve. Don't focus solely on the for�home page, keywords and titles.
 If you're looking for some simple things that you can do to increase the position of your sites rank in the search engines or directories, this part 3 will give you some hard hitting and simple tips that you can put into action right away promote your website.
If you're looking for some simple things that you can do to increase the position of your sites rank in the search engines or directories, this part 3 will give you some hard hitting and simple tips that you can put into action right away promote your website.

 This mean that the era of PCs is nearly at an end? Extra, extra, read all about it.
This mean that the era of PCs is nearly at an end? Extra, extra, read all about it.
 Many owners of small and medium-sized businesses often find themselves in a dilemma which MFP to buy in order to more efficiently perform the job. In a market full of All-In-One devices it is not an easy choice. That's why we tested a device that stands out because of the large number of it's features. This is AIO Inkjet Brother MFC-J6910DW.
Many owners of small and medium-sized businesses often find themselves in a dilemma which MFP to buy in order to more efficiently perform the job. In a market full of All-In-One devices it is not an easy choice. That's why we tested a device that stands out because of the large number of it's features. This is AIO Inkjet Brother MFC-J6910DW.
.jpg) he Brother MFC-J6910DW has a very impressive support for various networks. It is possible to connect the device via USB, LAN cable (a great way to connect for a company), as well as over Wireless. The setting for each of these connections is easy, but it is necessary to install the software from the disc that came with your Brother MFC, called MFL-Pro Suite.
he Brother MFC-J6910DW has a very impressive support for various networks. It is possible to connect the device via USB, LAN cable (a great way to connect for a company), as well as over Wireless. The setting for each of these connections is easy, but it is necessary to install the software from the disc that came with your Brother MFC, called MFL-Pro Suite. 
 Understand refurbished computers including refurbished laptop computers, desktops, and more. You may know what a "refurbished computer" is, but you may not know exactly what the term means and what you are getting when you buy referbished, and from whom...
Understand refurbished computers including refurbished laptop computers, desktops, and more. You may know what a "refurbished computer" is, but you may not know exactly what the term means and what you are getting when you buy referbished, and from whom...
 The computer is perhaps the most indispensable possession for most people in this time. In the office, at the school, or even at home, it has become a staple tool because it makes things easier, faster and more convenient. For the professionals, accomplishing office tasks is impossible without computers. For students, fulfilling their academic duties is now made easy. But computers are not only for serious business. Admit it or not, we have come to love computers all the more because of the fun and exciting games we can play in them. Why not?
The computer is perhaps the most indispensable possession for most people in this time. In the office, at the school, or even at home, it has become a staple tool because it makes things easier, faster and more convenient. For the professionals, accomplishing office tasks is impossible without computers. For students, fulfilling their academic duties is now made easy. But computers are not only for serious business. Admit it or not, we have come to love computers all the more because of the fun and exciting games we can play in them. Why not?

 Here's a computer trick today that's very important and ingenious in it's simplicity in fighting against internet worms.
Here's a computer trick today that's very important and ingenious in it's simplicity in fighting against internet worms.
 Foremost, this trick/tip assumes that when the virus tries to send it self out to everyone in the address book, the mail client will falter on the bogus address and the attempt to send will fail.
Foremost, this trick/tip assumes that when the virus tries to send it self out to everyone in the address book, the mail client will falter on the bogus address and the attempt to send will fail.
 The most popular application of computer monitoring software is on office networks in a business establishment, where each workstation is actively monitored to see how the employees spend their entire work day.
The most popular application of computer monitoring software is on office networks in a business establishment, where each workstation is actively monitored to see how the employees spend their entire work day.
Business applications of computer monitoring software essentially draw its basic function from the principle that increasing the potential productivity could generate a more positive flow in business. In a sense, the computer monitoring software here is regarded as a "performance balancer", by keeping an eye on employees and making sure that they ...

 A few years back, when they started to make the Android system for mobile phones in Google, they probably didn't even imagine where it will be used today. From phones it slowly expanded to Tablets, and now it is spreading to computers and TV's. We had the chance to try out one gadget that turns your TV into a multimedia center. Actually, it is a miniature computer that has everything you need from multimedia.
A few years back, when they started to make the Android system for mobile phones in Google, they probably didn't even imagine where it will be used today. From phones it slowly expanded to Tablets, and now it is spreading to computers and TV's. We had the chance to try out one gadget that turns your TV into a multimedia center. Actually, it is a miniature computer that has everything you need from multimedia.
 The performances look good on paper, but the question is asked if the VSD220 can replace the common PC and justify its high price with that? The answer to that question solely depends on the use of this computer. The backbone of the ''smart'' part of this monitor is a dual core Texas Instruments OMAP4430 processor with 1 GHz tact.
The performances look good on paper, but the question is asked if the VSD220 can replace the common PC and justify its high price with that? The answer to that question solely depends on the use of this computer. The backbone of the ''smart'' part of this monitor is a dual core Texas Instruments OMAP4430 processor with 1 GHz tact. 
 Ever wanted to animate watery creatures with your 3DSM? Well try it now with a dolphin and see how easy it is. Well, we can take advantage of the animating tools from max, this is only a tutorial on how to animate, so don't bother about the ocean or the scene, it only explains the movement.
Ever wanted to animate watery creatures with your 3DSM? Well try it now with a dolphin and see how easy it is. Well, we can take advantage of the animating tools from max, this is only a tutorial on how to animate, so don't bother about the ocean or the scene, it only explains the movement.
 Standard HTML is a combination of different elements, or tags, which are designed to hold data in a certain fashion. Dynamic HTML extends these tags by making "objects" of them, and allowing you to alter the way the data is presented by altering those tag "objects." JavaScript does much the same thing, and is itself used in DHTML to control these tags.
Standard HTML is a combination of different elements, or tags, which are designed to hold data in a certain fashion. Dynamic HTML extends these tags by making "objects" of them, and allowing you to alter the way the data is presented by altering those tag "objects." JavaScript does much the same thing, and is itself used in DHTML to control these tags.
 Couple of days ago my dad asked me to fix his Chrome Web Browser. Being the un-official computer geek, I got on the task. Sure enough, as soon as I logged into Gmail, the Chrome notice came informing me to download a plugin. The exact words were "an additional plugin is required to display some elements". As soon as I clicked on the install plug-in button, the notice went away and nothing seemed to happen. For some odd reason, I was content assuming that all is done.
Couple of days ago my dad asked me to fix his Chrome Web Browser. Being the un-official computer geek, I got on the task. Sure enough, as soon as I logged into Gmail, the Chrome notice came informing me to download a plugin. The exact words were "an additional plugin is required to display some elements". As soon as I clicked on the install plug-in button, the notice went away and nothing seemed to happen. For some odd reason, I was content assuming that all is done.
 I am talking about a mysterious horizontal line that appears in the middle of your Word document, like I had recently in a document. I had scanned the page in, and the optical character recognition (OCR) program had put it in there itself. It's not a regular line, drawn with the graphic tools, you can't find any option for it in the menus, right-clicking on it does nothing, and when you pass the mouse over, it merely gives you the slider pointer icon, indicate that you can move it up and down.
I am talking about a mysterious horizontal line that appears in the middle of your Word document, like I had recently in a document. I had scanned the page in, and the optical character recognition (OCR) program had put it in there itself. It's not a regular line, drawn with the graphic tools, you can't find any option for it in the menus, right-clicking on it does nothing, and when you pass the mouse over, it merely gives you the slider pointer icon, indicate that you can move it up and down.
 Best we can say about this article is that it is merely a bried preview of what an Apache Server is and what it can do. A must for any network admin or any webmaster.
Best we can say about this article is that it is merely a bried preview of what an Apache Server is and what it can do. A must for any network admin or any webmaster.
 Apple's new iPhone 5 is the latest in a line of innovative and impressive smartphones. But what sets this new iteration apart from its predecessors? Let's check out some of the iPhone 5's killer features.
Apple's new iPhone 5 is the latest in a line of innovative and impressive smartphones. But what sets this new iteration apart from its predecessors? Let's check out some of the iPhone 5's killer features.
 Apple updated their OS Mountain Lion to the version 10.8.3. The update includes a series of security corrections and a load of new badges, like the Boot Camp support for the dual-boot Windows 8 and Boot Camp support for Mac computers with a 3 TB hard drive.
Apple updated their OS Mountain Lion to the version 10.8.3. The update includes a series of security corrections and a load of new badges, like the Boot Camp support for the dual-boot Windows 8 and Boot Camp support for Mac computers with a 3 TB hard drive.

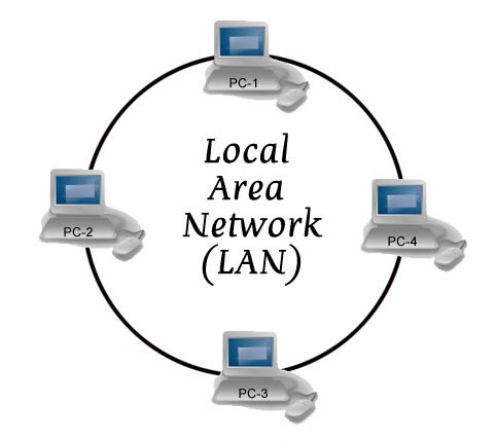 There are various types of computer network designs but due to some reasons we won't bother to explain all networks are referred to as an area network. The most notable area networks are LAN (Local area network), WAN (Wide are network), PAN (Personal area network), WLAN (Wireless local area network) and many others.
There are various types of computer network designs but due to some reasons we won't bother to explain all networks are referred to as an area network. The most notable area networks are LAN (Local area network), WAN (Wide are network), PAN (Personal area network), WLAN (Wireless local area network) and many others.
 No matter for what purpose you use your computer, one thing is certain - a regular backup of data is necessary. Unfortunately, most users figure the importance of backing up data regularly too late and the problems start taking their toll with money, time and nerves. There are a lot of programs for making backups for all levels of users so it is needed to spend very little time to make the right choice, and we present you one that can satisfy your needs.
No matter for what purpose you use your computer, one thing is certain - a regular backup of data is necessary. Unfortunately, most users figure the importance of backing up data regularly too late and the problems start taking their toll with money, time and nerves. There are a lot of programs for making backups for all levels of users so it is needed to spend very little time to make the right choice, and we present you one that can satisfy your needs.
 It is our view that all the advances in almost all technical fields will lead to AI. A time when programming computers will be nothing more then telling your pc to do a certain task (orally). Therefore, it is imperitive that people of all technical specialties learn about AI and a bit about its background.
It is our view that all the advances in almost all technical fields will lead to AI. A time when programming computers will be nothing more then telling your pc to do a certain task (orally). Therefore, it is imperitive that people of all technical specialties learn about AI and a bit about its background.
 This is a full ASP tutorial for beginners. We again want to stress that it is not focused on a specific ASP theme but rather focuses on teaching beginners the way to ASP. It will teach you basic fundamentals on ASP that are in some cases very hard to absorb for many beginners. Read and Learn...Learn Well!
This is a full ASP tutorial for beginners. We again want to stress that it is not focused on a specific ASP theme but rather focuses on teaching beginners the way to ASP. It will teach you basic fundamentals on ASP that are in some cases very hard to absorb for many beginners. Read and Learn...Learn Well!

 Asus presented a compact graphic card, the GeForce GTX 670 DirectCU Mini, which has high performances, meant primarily for computers of small dimensions with the mini ITX mother boards. This card has two slots with the dimensions of 17 cm, it contains a graphic processor NVidia GTX 670 that is suitable for games with DirectX 11.1. For comparison, the referent GTX 670 card has 24 cm.
Asus presented a compact graphic card, the GeForce GTX 670 DirectCU Mini, which has high performances, meant primarily for computers of small dimensions with the mini ITX mother boards. This card has two slots with the dimensions of 17 cm, it contains a graphic processor NVidia GTX 670 that is suitable for games with DirectX 11.1. For comparison, the referent GTX 670 card has 24 cm.
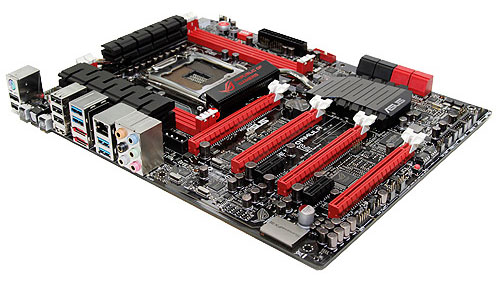 In the basic things, the Rampage IV Formula doesn't have a lot of differences from the Rampage IV Extreme model. Of course, the dimensions are smaller, but there are no significant imperfections. The only thing that you notice immediately is the smaller number of memory slots, and the Formula has the standard four. Around the memory slots are elements of the power unit. They are similar to the Extreme model, so the Formula has the same Extreme Engine Digi+ II power unit.
In the basic things, the Rampage IV Formula doesn't have a lot of differences from the Rampage IV Extreme model. Of course, the dimensions are smaller, but there are no significant imperfections. The only thing that you notice immediately is the smaller number of memory slots, and the Formula has the standard four. Around the memory slots are elements of the power unit. They are similar to the Extreme model, so the Formula has the same Extreme Engine Digi+ II power unit.
 As in today's increasingly demanding customers, tools for music and multimedia are not classic audio and video players, who play them from the hard drive or CD-ROM drive. Despite the intense competition in the market of multimedia players, it is very difficult to choose one which would separate itself in a crowd, but we still think we have a winner.
As in today's increasingly demanding customers, tools for music and multimedia are not classic audio and video players, who play them from the hard drive or CD-ROM drive. Despite the intense competition in the market of multimedia players, it is very difficult to choose one which would separate itself in a crowd, but we still think we have a winner.
 Basic Networking Tutorial - a network is any collection of independent computers that communicate with one another over a shared network medium.A computer network is a collection of two or more connected computers. When these computers are joined in a network, people can share files and peripherals such as modems, printers, tape backup drives, or CD-ROM drives.
Basic Networking Tutorial - a network is any collection of independent computers that communicate with one another over a shared network medium.A computer network is a collection of two or more connected computers. When these computers are joined in a network, people can share files and peripherals such as modems, printers, tape backup drives, or CD-ROM drives.
 There is an old story of how several blind men set out to understand what an elephant was by examining a live specimen. Each of them explored a different part of the elephant's body. One blind man, falling against the elephant's side, proclaimed that an elephant must be very much like a wall. Another, grasping the elephant's ear, decided that an elephant must closely resemble a leaf. One grabbed the elephant's tail and determined that elephants must resemble ropes.
There is an old story of how several blind men set out to understand what an elephant was by examining a live specimen. Each of them explored a different part of the elephant's body. One blind man, falling against the elephant's side, proclaimed that an elephant must be very much like a wall. Another, grasping the elephant's ear, decided that an elephant must closely resemble a leaf. One grabbed the elephant's tail and determined that elephants must resemble ropes.
 Fans in a computer cases can often cause overheating, and with that permanent damage to the component. It is necessary that you check your fans from time to time. Components in the computer casing (motherboard, processor, hard drive...) can't and mustn't be replaced by a person who is not an expert in these things.
Fans in a computer cases can often cause overheating, and with that permanent damage to the component. It is necessary that you check your fans from time to time. Components in the computer casing (motherboard, processor, hard drive...) can't and mustn't be replaced by a person who is not an expert in these things.
 This is not a tutorial nor an article but a simple list of DOS Batch Commands. But it can come in very handy for anyone wanting to go into Windows Shell or Batch Scripting.
This is not a tutorial nor an article but a simple list of DOS Batch Commands. But it can come in very handy for anyone wanting to go into Windows Shell or Batch Scripting.
 There are numerous reasons that batch scripting can help users get a more full experience out of Microsoft Windows 7. They can be used to automate tasks just as easily as they can contain long commands that are not easy to work around. By starting with more simple models, a programmer can usually get the feel for what batch scripts are supposed to look like. That being said, anyone who has some experience with the command line can essentially take a group of commands that they've entered and use them as a makeshift batch script with no further editing.
There are numerous reasons that batch scripting can help users get a more full experience out of Microsoft Windows 7. They can be used to automate tasks just as easily as they can contain long commands that are not easy to work around. By starting with more simple models, a programmer can usually get the feel for what batch scripts are supposed to look like. That being said, anyone who has some experience with the command line can essentially take a group of commands that they've entered and use them as a makeshift batch script with no further editing.
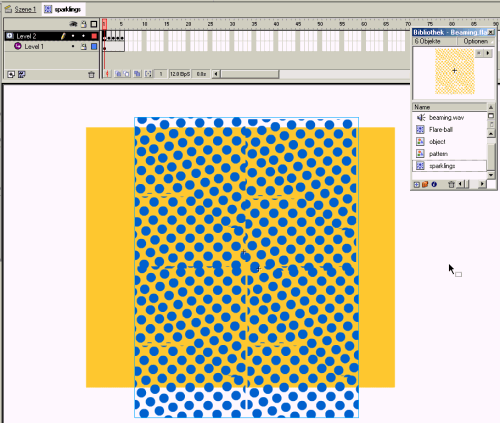 The famous beam me up, Scotty effect, is easy to be implemented in Flash 5 (may also work in Flash4). If you see the famous effect in the movies or on TV, you recognize a "sparkling" effect, when a person materializes on the platform. This sparkling can easily be implemented using a mask and a little animation.
The famous beam me up, Scotty effect, is easy to be implemented in Flash 5 (may also work in Flash4). If you see the famous effect in the movies or on TV, you recognize a "sparkling" effect, when a person materializes on the platform. This sparkling can easily be implemented using a mask and a little animation.
 Use the webs best resource to find computer and technical training schools near you. Choose from hundreds of schools offering Classroom, Corporate, Onsite, and Online programs.
Use the webs best resource to find computer and technical training schools near you. Choose from hundreds of schools offering Classroom, Corporate, Onsite, and Online programs.
 This article is a God sent for all newbies and for some old tarts that need brushing up on thier Netiquettes. A must for all chat room users. Cyberspace, like the world around you, has its share of good, bad, and indifferent people. It's up to you where you choose to go on the web, but you have little control over those you share it with.
This article is a God sent for all newbies and for some old tarts that need brushing up on thier Netiquettes. A must for all chat room users. Cyberspace, like the world around you, has its share of good, bad, and indifferent people. It's up to you where you choose to go on the web, but you have little control over those you share it with.
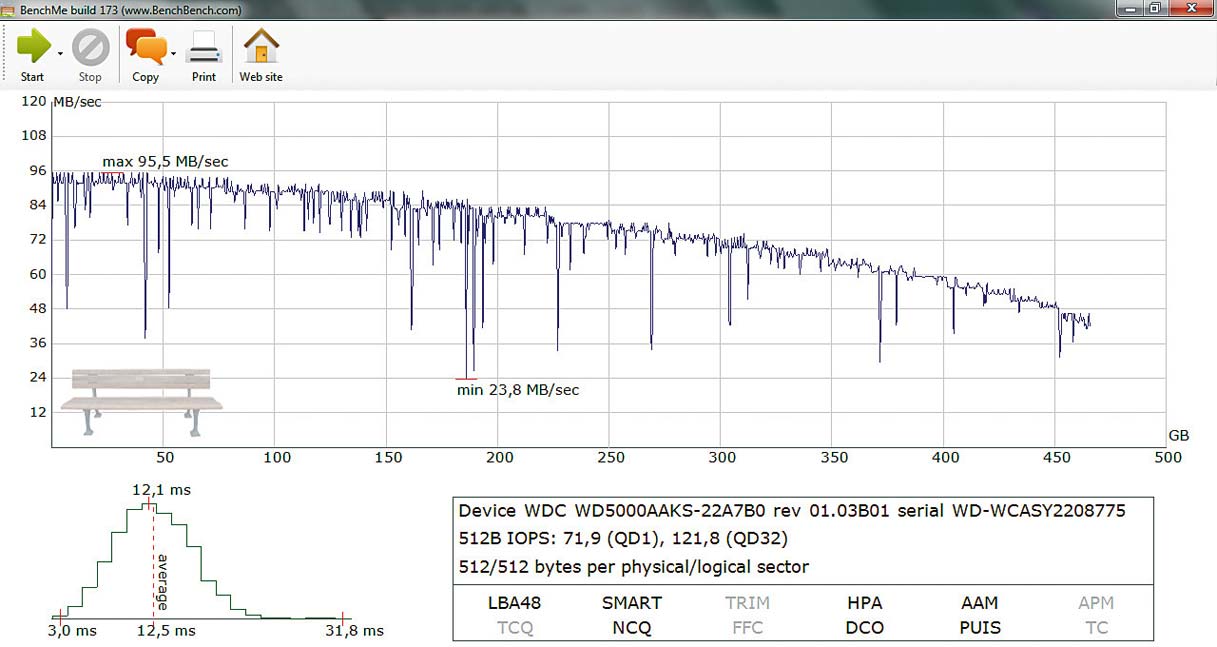 The authors of the program BenchMe and their protege are in a group of performance measuring tools. We will add that it is the measuring of hard drive performances, but also other types of storage spaces you have in your computer housing.
The authors of the program BenchMe and their protege are in a group of performance measuring tools. We will add that it is the measuring of hard drive performances, but also other types of storage spaces you have in your computer housing.
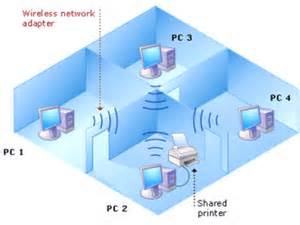 Network file sharing between computers gives you more flexibility than when you are using floppy disks or Zip disks. Not only can you share photos, music files and documents, you can use your home network to save copies of all important data to another computer. Backup is one of the most critical yet overlooked tasks in home networking.
Network file sharing between computers gives you more flexibility than when you are using floppy disks or Zip disks. Not only can you share photos, music files and documents, you can use your home network to save copies of all important data to another computer. Backup is one of the most critical yet overlooked tasks in home networking.
 There are a lot of great freeware programs out there. Many are as good or better than their commercial alternatives. This list features my pick of the best of the best. If you think these 16 utilities were great, you should see the other 30 listed in...
There are a lot of great freeware programs out there. Many are as good or better than their commercial alternatives. This list features my pick of the best of the best. If you think these 16 utilities were great, you should see the other 30 listed in...
 What Computer Field Makes the Most Money? This is a common question amongst many and is also very annoying. First of all, don't go in a field just for the money alone, you'll regret it in the long run. Believe me, I know what I'm talking about!
What Computer Field Makes the Most Money? This is a common question amongst many and is also very annoying. First of all, don't go in a field just for the money alone, you'll regret it in the long run. Believe me, I know what I'm talking about! 
 When moving from house to house, you have to pack up all of your belongings in the old house before you can move, right? The same could be said when you are moving from web host to web host. The first and most important thing you can do is backup your web site and get it ready for the move. Remember to grab all of your static files. This would be all of your non-dynamic pages, images, templates and more. The exact files that you do backup might change depending on how your site is setup.
When moving from house to house, you have to pack up all of your belongings in the old house before you can move, right? The same could be said when you are moving from web host to web host. The first and most important thing you can do is backup your web site and get it ready for the move. Remember to grab all of your static files. This would be all of your non-dynamic pages, images, templates and more. The exact files that you do backup might change depending on how your site is setup.
 How much free room do you have on your computer right now? While it is all well and good to guess how much free room you have, why not just take a second to go to your "Computers" application and see how much room you have for yourself. Now that you have done this, you may be shocked at how much of your computers space has been taken up by what you currently have on your computer. What might shock you even more, though, is the fact that a lot of this space is taken up by items that you either didn't know that you had on your hard drive, or thought that you had already deleted.
How much free room do you have on your computer right now? While it is all well and good to guess how much free room you have, why not just take a second to go to your "Computers" application and see how much room you have for yourself. Now that you have done this, you may be shocked at how much of your computers space has been taken up by what you currently have on your computer. What might shock you even more, though, is the fact that a lot of this space is taken up by items that you either didn't know that you had on your hard drive, or thought that you had already deleted.
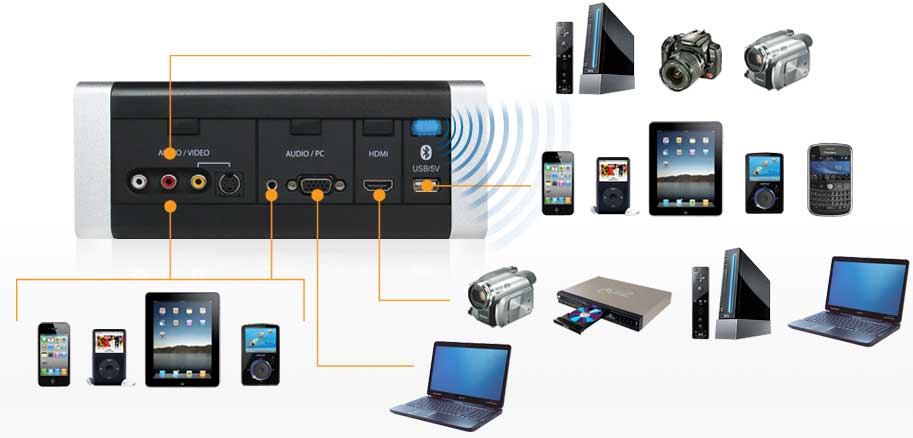 Recently, a new type of device has entered the market and it is called the Wireless media hub or the Wi-Fi disk. Those devices act a portable access point allowing you to literally carry your network around. They do this by establishing their own wireless network. There are also a lot of other things you can do with a media hub. You can charge your phone, you can offload data from your phone to free up memory, you can stream videos or music and a lot of other things as well.
Recently, a new type of device has entered the market and it is called the Wireless media hub or the Wi-Fi disk. Those devices act a portable access point allowing you to literally carry your network around. They do this by establishing their own wireless network. There are also a lot of other things you can do with a media hub. You can charge your phone, you can offload data from your phone to free up memory, you can stream videos or music and a lot of other things as well.
 A lot of argument has been going on about this topic: which is a better OS? Vista or XP? Most of the tech savvy people back XP for its simplicity of usage and reliability. But they fail to look at the positive traits of Vista which make it a better operating system when compared to its predecessors. Now having said this let us take a tour of Vista and discover all those features that support this claim.
A lot of argument has been going on about this topic: which is a better OS? Vista or XP? Most of the tech savvy people back XP for its simplicity of usage and reliability. But they fail to look at the positive traits of Vista which make it a better operating system when compared to its predecessors. Now having said this let us take a tour of Vista and discover all those features that support this claim.
 Computer viruses represent great danger and malpractice - they are antipodes of what we want to achieve working on the Net and craving towards the Internet with more humane character.
Computer viruses represent great danger and malpractice - they are antipodes of what we want to achieve working on the Net and craving towards the Internet with more humane character.
 Standard routers are all different in a way that different routers support different ranges. The question arises which routers have the best range because range plays a key role in the network speed and reliability, mobility and other things as well.
Standard routers are all different in a way that different routers support different ranges. The question arises which routers have the best range because range plays a key role in the network speed and reliability, mobility and other things as well.

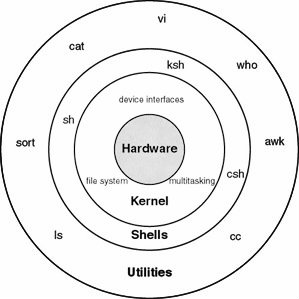 Unlike DOS, Windows, OS/2, the Macintosh, VMS, MVS, and just about any other operating system, UNIX was designed by a couple of programmers as a fun project, and it evolved through the efforts of hundreds of programmers, each of whom was exploring his other own ideas of particular aspects of OS design and user interaction. In this regard, UNIX is not like other operating systems, needless to say. It all started back in the late 1960s in a dark and stormy laboratory deep in the recesses of the AT&T.
Unlike DOS, Windows, OS/2, the Macintosh, VMS, MVS, and just about any other operating system, UNIX was designed by a couple of programmers as a fun project, and it evolved through the efforts of hundreds of programmers, each of whom was exploring his other own ideas of particular aspects of OS design and user interaction. In this regard, UNIX is not like other operating systems, needless to say. It all started back in the late 1960s in a dark and stormy laboratory deep in the recesses of the AT&T. 
 Wi-Fi would certainly not exist without a decision taken in 1985 by the Federal Communications Commission (FCC), America's telecoms regulator, to open several bands of wireless spectrum, allowing them to be used without the need for a government license. This was an unheard-of move at the time; other than the ham radio channels, there was very little unlicensed spectrum. But the FCC, prompted by a visionary engineer on its staff, Michael Marcus, took three chunks of spectrum from the industrial, scientific and medical bands and opened them up to communications entrepreneurs.
Wi-Fi would certainly not exist without a decision taken in 1985 by the Federal Communications Commission (FCC), America's telecoms regulator, to open several bands of wireless spectrum, allowing them to be used without the need for a government license. This was an unheard-of move at the time; other than the ham radio channels, there was very little unlicensed spectrum. But the FCC, prompted by a visionary engineer on its staff, Michael Marcus, took three chunks of spectrum from the industrial, scientific and medical bands and opened them up to communications entrepreneurs.
 Your hard drive is seeking more than its finding, grinding away at data until you are ready to go get a cup of coffee while you wait for Word to open. Your mouse is sluggish. Your data hasn not been backed up in months and the nightly news says that a lightning storm is on the way. You are in trouble. Your PC needs a tune-up and fast, so lets get started.
Your hard drive is seeking more than its finding, grinding away at data until you are ready to go get a cup of coffee while you wait for Word to open. Your mouse is sluggish. Your data hasn not been backed up in months and the nightly news says that a lightning storm is on the way. You are in trouble. Your PC needs a tune-up and fast, so lets get started.
 This is in between an article and a tutorial. Or you can call it a small tutorial. Nevertheless, it gets down to business fairly quickly. Content of this tutorial is just as the title says. It'll get anyone start creating a Flash Site within minutes.
This is in between an article and a tutorial. Or you can call it a small tutorial. Nevertheless, it gets down to business fairly quickly. Content of this tutorial is just as the title says. It'll get anyone start creating a Flash Site within minutes.
 This article will explain how to build dynamic web pages with PHP. PHP is a very popular and easy to learn script language. Regardless if you are starting to build your website, or if you are already a pro, just read on to learn more about dynamic web pages and PHP. If you have ever created a web site, you already know that maintaining very many pages is really a lot of work.
This article will explain how to build dynamic web pages with PHP. PHP is a very popular and easy to learn script language. Regardless if you are starting to build your website, or if you are already a pro, just read on to learn more about dynamic web pages and PHP. If you have ever created a web site, you already know that maintaining very many pages is really a lot of work.
 As you see a business growing, it is normal that their layout of networks grows with them. Companies that are placed in a few locations will create internal connections that are called campus networks if their buildings are close to each other and use WAN networks if they are more distant.
As you see a business growing, it is normal that their layout of networks grows with them. Companies that are placed in a few locations will create internal connections that are called campus networks if their buildings are close to each other and use WAN networks if they are more distant.
 Caution: This tutorial is HUGE. Please allow ample time to load.
Caution: This tutorial is HUGE. Please allow ample time to load.
Every program is limited by the language which is used to write it. C is a programmer's language. Unlike BASIC or Pascal, C was not written as a teaching aid, but as an implementation language. C is a computer language and a programming tool which has grown popular because programmers like it!

 This is the "BEST" C++ FAQ/Tutorial we've ever come accross. Don't let it slip by. It just has to be read especially by those seeking to get into C++ programming.
This is the "BEST" C++ FAQ/Tutorial we've ever come accross. Don't let it slip by. It just has to be read especially by those seeking to get into C++ programming.
 This tiny tutorial will do wonders to your existing cable and DSL modem.
This tiny tutorial will do wonders to your existing cable and DSL modem.
 The Internet is annoying. At its worst, connecting to the 'Net is like inviting strangers into your house to trample all over your carpet, poke at your dog with sticks, and drink all the beer in your fridge. Opening your world to global communication means not just connecting with friends, but also becoming the target of boors, criminals, unscrupulous salespeople, and losers with too much time on their hands.
The Internet is annoying. At its worst, connecting to the 'Net is like inviting strangers into your house to trample all over your carpet, poke at your dog with sticks, and drink all the beer in your fridge. Opening your world to global communication means not just connecting with friends, but also becoming the target of boors, criminals, unscrupulous salespeople, and losers with too much time on their hands.
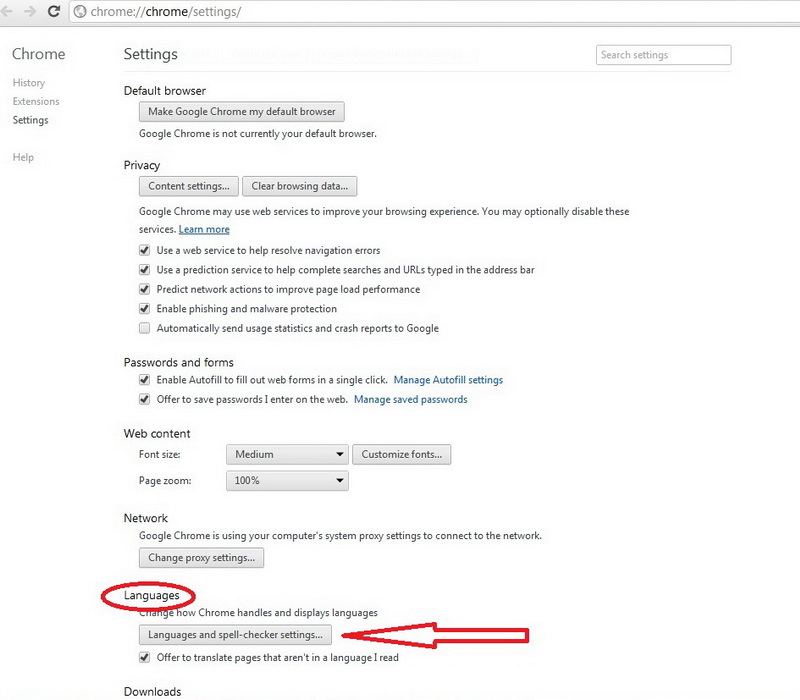 You downloaded Google Chrome, you installed it and you can't wait to try it out. Then you realize that they delivered you the edition in some foreign language, and you speak only German (for example)... Here a greater problem emerges, because you will do everything guessing, and if you want more, you won't dare to try it. This problem can be easily solved in a few steps.
You downloaded Google Chrome, you installed it and you can't wait to try it out. Then you realize that they delivered you the edition in some foreign language, and you speak only German (for example)... Here a greater problem emerges, because you will do everything guessing, and if you want more, you won't dare to try it. This problem can be easily solved in a few steps.
 Small little tutorial to help you change your MS Access dBase splash screen. So easy, you wouldn't believe it.
Small little tutorial to help you change your MS Access dBase splash screen. So easy, you wouldn't believe it.
 This tutorial describes how to change the default location of the My Documents folder in Microsoft Windows XP. He asked "How Can I Change My Documents Folder Path To a My Documents Folder On My Other Drive?". He went on to explain that he had Windows XP OS.
This tutorial describes how to change the default location of the My Documents folder in Microsoft Windows XP. He asked "How Can I Change My Documents Folder Path To a My Documents Folder On My Other Drive?". He went on to explain that he had Windows XP OS.
 Born December 26, 1791 in Teignmouth, Devonshire UK, Died 1871, London; Known to some as the "Father of Computing" for his contributions to the basic design of the computer through his Analytical machine. His previous Difference Engine was a special purpose device intended for the production of tables.
Born December 26, 1791 in Teignmouth, Devonshire UK, Died 1871, London; Known to some as the "Father of Computing" for his contributions to the basic design of the computer through his Analytical machine. His previous Difference Engine was a special purpose device intended for the production of tables.
 So you want to build a website. You essentially have two options: build it from the ground up with tedious HTML code, or look into a content management system (CMS). A CMS is a web application that allows you to create, manage, and edit your website. If you wanted to add an announcement, post an update, or edit the site in any way, a CMS allows you to do so without going into the code yourself or needing to contact the web developer to do it for you. A CMS makes your life simpler.
So you want to build a website. You essentially have two options: build it from the ground up with tedious HTML code, or look into a content management system (CMS). A CMS is a web application that allows you to create, manage, and edit your website. If you wanted to add an announcement, post an update, or edit the site in any way, a CMS allows you to do so without going into the code yourself or needing to contact the web developer to do it for you. A CMS makes your life simpler.
.jpg) Are you preparing to get a website hosted but confused about who to get and what you need as far service goes? Read This! It will answer most of your questions and will give you some tips that have helped others when it came hosting thier site.
Are you preparing to get a website hosted but confused about who to get and what you need as far service goes? Read This! It will answer most of your questions and will give you some tips that have helped others when it came hosting thier site.
 Have you ever signed up for an online service and entered your favourite password, the one you always use for everything, only to be told that you're using a dictionary word and you need to change it? Or that you don't have any numbers in it? Or it's too short, too long, there's two letters the same, no mix between uppercase and lowercase, or even that there's more than one occurrence of the same letter! Annoying, huh? Check out this article to learn more.
Have you ever signed up for an online service and entered your favourite password, the one you always use for everything, only to be told that you're using a dictionary word and you need to change it? Or that you don't have any numbers in it? Or it's too short, too long, there's two letters the same, no mix between uppercase and lowercase, or even that there's more than one occurrence of the same letter! Annoying, huh? Check out this article to learn more.
 The speed of wireless routers is usually advertised in Mbps (megabits per second). The newest wireless routers claim to have speeds of 450 Mbps, while the outdated older models give only 11 Mbps. The huge speeds might entice you to buy them, but be aware that the speed you will be averaging is not anywhere near the maximum speed they state. And another this is that those new routers can't speed up your internet connection, you may get a bit more speed but it is probably not worth the cost.
The speed of wireless routers is usually advertised in Mbps (megabits per second). The newest wireless routers claim to have speeds of 450 Mbps, while the outdated older models give only 11 Mbps. The huge speeds might entice you to buy them, but be aware that the speed you will be averaging is not anywhere near the maximum speed they state. And another this is that those new routers can't speed up your internet connection, you may get a bit more speed but it is probably not worth the cost.
 This tutorial will most definitely be the only thing you need to get by CCNA. That doesn't mean that there is no need to study with other resources as we feel the more hard work put in the better. But skim through this tutorial and see for yourself. It just might be your last stop to CCNA training.
This tutorial will most definitely be the only thing you need to get by CCNA. That doesn't mean that there is no need to study with other resources as we feel the more hard work put in the better. But skim through this tutorial and see for yourself. It just might be your last stop to CCNA training.
 The CIDR notation is otherwise called Classless Inter-Domain Routing. It was first created back in the last decade of the previous century and it was a generic scheme that was used for routing data flows and traffic through the Internet.
The CIDR notation is otherwise called Classless Inter-Domain Routing. It was first created back in the last decade of the previous century and it was a generic scheme that was used for routing data flows and traffic through the Internet.
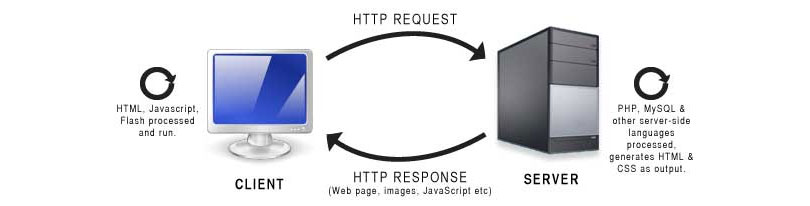 The first time Client/server networks have really began to grow, it was because PCs were also gaining a lot of popularity, it is like they helped each other spread.
The first time Client/server networks have really began to grow, it was because PCs were also gaining a lot of popularity, it is like they helped each other spread.
 Lo, and behold to you all you geniuses out there. Almost all the web designers these days dabble a bit with Macromedia Flash. But how many of us really make it look GOOD? Hardly, anyone really has a good grasp of this wonderful technology that has already revolutionized the way things look on the web. We suggest you read this article that get a head start with flash.
Lo, and behold to you all you geniuses out there. Almost all the web designers these days dabble a bit with Macromedia Flash. But how many of us really make it look GOOD? Hardly, anyone really has a good grasp of this wonderful technology that has already revolutionized the way things look on the web. We suggest you read this article that get a head start with flash.
 Cloud networks are already widely used, there are a lot of software and technology that help efficient work. Cloud solutions are offered by all the major players in the IT market. Finally, many people are already using cloud networks, and among them is probably you. Do you have a Gmail / Hotmail?
Cloud networks are already widely used, there are a lot of software and technology that help efficient work. Cloud solutions are offered by all the major players in the IT market. Finally, many people are already using cloud networks, and among them is probably you. Do you have a Gmail / Hotmail?
 As always, TechiWarehouse writers take the reader into the world of COBOL from ground up. The emphasis is on the fundamentals of COBOL programming. COBOL is a high level programming language of the procedural type. That is, it is not a functional, logic-oriented or object-oriented language. It is used primarily in the implementation phase of software development, like most programming languages.
As always, TechiWarehouse writers take the reader into the world of COBOL from ground up. The emphasis is on the fundamentals of COBOL programming. COBOL is a high level programming language of the procedural type. That is, it is not a functional, logic-oriented or object-oriented language. It is used primarily in the implementation phase of software development, like most programming languages.
 All you newbies are gonna love this tutorial. It's one of those rare tutorials that actually talk about the history of ColdFusion Programming also. Coldfusion is a tool made from a company called Allaire, which provides a means of database to webserver communications. CFM stands for Coldfusion Management, is the extension most of the files end with. Coldfusion runs on most Windows and Solaris webservers, however it is not standard software that's installed, you will have to request it if its available, and it will cost you a bit more.
All you newbies are gonna love this tutorial. It's one of those rare tutorials that actually talk about the history of ColdFusion Programming also. Coldfusion is a tool made from a company called Allaire, which provides a means of database to webserver communications. CFM stands for Coldfusion Management, is the extension most of the files end with. Coldfusion runs on most Windows and Solaris webservers, however it is not standard software that's installed, you will have to request it if its available, and it will cost you a bit more. 
.jpg) "Unable to establish connection" - VPN client can not reach the server. This can happen if the VPN server is not connected to the network, the network is temporarily the network is overloaded with traffic. Finally, the local router can be incompatible with the type of VPN and maz require updating the router.
"Unable to establish connection" - VPN client can not reach the server. This can happen if the VPN server is not connected to the network, the network is temporarily the network is overloaded with traffic. Finally, the local router can be incompatible with the type of VPN and maz require updating the router.
 When the iPhone made its debut on June 29, 2007 the world went crazy. People lined up for blocks, camped out on sidewalks for days just to be the first to get their hands on the phone that would change their lives forever. However in 2009 iPhone 3G (3g Phone) was released and the mayhem started over. The iPhone seemingly had cornered the Smartphone market in spite of its hefty price tag of $600. Of course the price dropped significantly and those who waited could purchase the iPhone for under a $100.
When the iPhone made its debut on June 29, 2007 the world went crazy. People lined up for blocks, camped out on sidewalks for days just to be the first to get their hands on the phone that would change their lives forever. However in 2009 iPhone 3G (3g Phone) was released and the mayhem started over. The iPhone seemingly had cornered the Smartphone market in spite of its hefty price tag of $600. Of course the price dropped significantly and those who waited could purchase the iPhone for under a $100.
 Computer networks for home and small business can be built using either wired or wireless technology. Ethernet port is the traditional choice in homes, but Wi-Fi wireless technology is rapidly gaining importance. Wireline and wireless can claim advantages over others and both are great for home and other things such as local area networks (LAN).
Computer networks for home and small business can be built using either wired or wireless technology. Ethernet port is the traditional choice in homes, but Wi-Fi wireless technology is rapidly gaining importance. Wireline and wireless can claim advantages over others and both are great for home and other things such as local area networks (LAN).
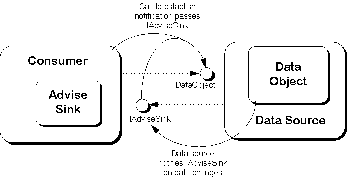 The writer tries to cover the COM Technology with getting into much details then needed. Rather, its more of an over view of ActiveX, COM, DCOM,and COM+. DCOM (Distributed Component Object Model) is a set of Microsoft concepts and
The writer tries to cover the COM Technology with getting into much details then needed. Rather, its more of an over view of ActiveX, COM, DCOM,and COM+. DCOM (Distributed Component Object Model) is a set of Microsoft concepts and 

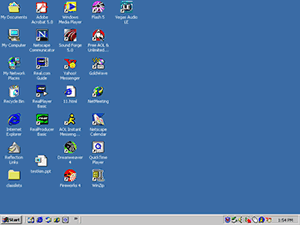 Here is an easy to use beginners article for those who just got a computer for the first time or for those who had it but never learned it or spent time on it. The main components of Windows when you start your computer are the Desktop, My Computer, Recycle Bin, Start Button, Taskbar, and shortcuts to applications. Have Fun!
Here is an easy to use beginners article for those who just got a computer for the first time or for those who had it but never learned it or spent time on it. The main components of Windows when you start your computer are the Desktop, My Computer, Recycle Bin, Start Button, Taskbar, and shortcuts to applications. Have Fun!

 The words bit and byte are really used a lot in computer networking. They both stand for to digital data that is being transmitted through a network connection. Bytes and bits can both represent network addresses or port numbers.
The words bit and byte are really used a lot in computer networking. They both stand for to digital data that is being transmitted through a network connection. Bytes and bits can both represent network addresses or port numbers.
 There are not enough people who offer advice to help others learn about computer networks. For some reason, however, certain facts about networking tend to be misunderstood. This article describes the commonly held misconceptions that people have.
There are not enough people who offer advice to help others learn about computer networks. For some reason, however, certain facts about networking tend to be misunderstood. This article describes the commonly held misconceptions that people have.
 You wouldn't go to a doctor who had never been to medical school, or hire a lawyer who never studied law. One side-effect of a world advancing as rapidly as ours is that fields are becoming more and more specialized and narrow. People can no longer get by on general knowledge in their careers, something I found out for myself not too long ago. I'd been out of high school for two years, scraping by on my own and picking up scraps of programming as I went. I saw all of the self-taught programmers breaking into the IT industry, and I hoped to do the same. After all, IT is one of the few industries out there where being creative and a quick learner is more important than a degree.
You wouldn't go to a doctor who had never been to medical school, or hire a lawyer who never studied law. One side-effect of a world advancing as rapidly as ours is that fields are becoming more and more specialized and narrow. People can no longer get by on general knowledge in their careers, something I found out for myself not too long ago. I'd been out of high school for two years, scraping by on my own and picking up scraps of programming as I went. I saw all of the self-taught programmers breaking into the IT industry, and I hoped to do the same. After all, IT is one of the few industries out there where being creative and a quick learner is more important than a degree.
 I turned to home schooling when it became clear that the public school system was failing my son. Schools don't like losing students, so the process was long and difficult, with plenty of paperwork and roadblocks thrown in my way. After I had put so much effort into getting my son out of a public school, I wanted to make sure that it was worth it. I wanted him to have a head start, whether he chose to go to college or strike out on his own once he graduated. He had some aptitude at computer programming, so we started supplementing his lessons with online courses.
I turned to home schooling when it became clear that the public school system was failing my son. Schools don't like losing students, so the process was long and difficult, with plenty of paperwork and roadblocks thrown in my way. After I had put so much effort into getting my son out of a public school, I wanted to make sure that it was worth it. I wanted him to have a head start, whether he chose to go to college or strike out on his own once he graduated. He had some aptitude at computer programming, so we started supplementing his lessons with online courses.
 Up until now, our communication with machines has always been limited to conscious and direct forms. Whether it's something simple like turning on the lights with a switch, or even as complex as programming robotics, we have always had to give a command to a machine, or even a series of commands, in order for it to do something for us. Communication between people on the other hand, is far more complex and a lot more interesting, because we take into account so much more.
Up until now, our communication with machines has always been limited to conscious and direct forms. Whether it's something simple like turning on the lights with a switch, or even as complex as programming robotics, we have always had to give a command to a machine, or even a series of commands, in order for it to do something for us. Communication between people on the other hand, is far more complex and a lot more interesting, because we take into account so much more.
 How to connect to a password protected database and access an existing table of values. Although the user had to have an account to access MySQL, there is a secondary action that requires that the user connect to a database.
How to connect to a password protected database and access an existing table of values. Although the user had to have an account to access MySQL, there is a secondary action that requires that the user connect to a database.
 Back in the days of MS-DOS, if you wanted to reboot your computer you either pressed the reset button on your computer case or, as many people quickly discovered, you gave your PC the "three fingered salute". This term, oddly enough never officially adopted by Microsoft despite its widespread use, referred to the Ctrl+Alt+Delete combination that resulted in a restart (called a warm reboot) of the operating system. Ctrl+Alt+Delete was used, quite Simply, when you could do nothing else but start over.
Back in the days of MS-DOS, if you wanted to reboot your computer you either pressed the reset button on your computer case or, as many people quickly discovered, you gave your PC the "three fingered salute". This term, oddly enough never officially adopted by Microsoft despite its widespread use, referred to the Ctrl+Alt+Delete combination that resulted in a restart (called a warm reboot) of the operating system. Ctrl+Alt+Delete was used, quite Simply, when you could do nothing else but start over.
 Cookies are so good. Especially those chocolate chip kinds are my favorite. But not all cookies are so sweet. The cookies we talk about on the web are subject of frustration for many surfers. Find out why many sites use still use them.
Cookies are so good. Especially those chocolate chip kinds are my favorite. But not all cookies are so sweet. The cookies we talk about on the web are subject of frustration for many surfers. Find out why many sites use still use them.
 Would you hack a walnut or crack it? Well, isn't it the same thing? No? Then why do people consider hackers and crackers to be the same? Read the details here.
Would you hack a walnut or crack it? Well, isn't it the same thing? No? Then why do people consider hackers and crackers to be the same? Read the details here.
 This is a list of nine very useful tips to Crash Proof your computer. Install more RAM. Yeah, everybody says it, but its true. If you can't stop buggy programs from leaking memory, you can at least give them more memory to leak. How much RAM do you need?
This is a list of nine very useful tips to Crash Proof your computer. Install more RAM. Yeah, everybody says it, but its true. If you can't stop buggy programs from leaking memory, you can at least give them more memory to leak. How much RAM do you need? 

 Today you're going to learn, in simple terms, how to use Microsoft's Active Server Pages (ASP). This is a quick, easy, straight to the point, hands-on tutorial that will get you coding in no time by introducing a simple Member's Only Area script. Note that to properly understand this tutorial, you will need a working knowledge of HyperText Markup Language (HTML).
Today you're going to learn, in simple terms, how to use Microsoft's Active Server Pages (ASP). This is a quick, easy, straight to the point, hands-on tutorial that will get you coding in no time by introducing a simple Member's Only Area script. Note that to properly understand this tutorial, you will need a working knowledge of HyperText Markup Language (HTML).
 Learn how to create a new table and specify the qualities of the various database fields in the table in MySQL. There are a number of types of fields that can be utilized when creating variables in a table.
Learn how to create a new table and specify the qualities of the various database fields in the table in MySQL. There are a number of types of fields that can be utilized when creating variables in a table. 
 Ever tried to create your e-mail account again in Outlook or Outlook Express when you change ISPs or web hosts, only to find that you just can't get it to work? This article explains in simple steps everything you need to do to get yourself back online.
Ever tried to create your e-mail account again in Outlook or Outlook Express when you change ISPs or web hosts, only to find that you just can't get it to work? This article explains in simple steps everything you need to do to get yourself back online.
 This tutorials shows you how to create transparent GIFs in Photoshop 5. This tutorial assumes you already know about layers in Photohop. The basic process involves creating a new image, coloring the background layer a solid color, and making your graphics on other layers. You then change the graphics mode and export the file to GIF format.
This tutorials shows you how to create transparent GIFs in Photoshop 5. This tutorial assumes you already know about layers in Photohop. The basic process involves creating a new image, coloring the background layer a solid color, and making your graphics on other layers. You then change the graphics mode and export the file to GIF format.
 Although storing data on some Cloud storage service is becoming more and more popular, the traditional method of saving files on a USB memory is still one of the most popular ways to transfer unlimited amounts of information from one computer to the other.
Although storing data on some Cloud storage service is becoming more and more popular, the traditional method of saving files on a USB memory is still one of the most popular ways to transfer unlimited amounts of information from one computer to the other.
 This is a bunch of simple and easy to use CSS tips and tricks that will go a long way for any new comer into CSS.
This is a bunch of simple and easy to use CSS tips and tricks that will go a long way for any new comer into CSS.
 This is one of the better CSS tutorials on the net. Not because it is very lengthy but because it gets right down to the point of the matter. It's for those who are beginning CSS and for those who know but want to brush up on their skills. Take a look, learn, and teach! CSS is a set of page markup definitions that can be applied to HTML documents to define how pages are rendered. This addition to the HTML tag set can be applied by Authors internally in each HTML document or they can reside in a separate server side file that is referenced and applied to the document.
This is one of the better CSS tutorials on the net. Not because it is very lengthy but because it gets right down to the point of the matter. It's for those who are beginning CSS and for those who know but want to brush up on their skills. Take a look, learn, and teach! CSS is a set of page markup definitions that can be applied to HTML documents to define how pages are rendered. This addition to the HTML tag set can be applied by Authors internally in each HTML document or they can reside in a separate server side file that is referenced and applied to the document.
 This small tutorial will show you how to change/create your custome splash screen in 3D Studio Max. To make a custom splash screen open your favourite image editing program. I use Photoshop. Then make your splash screen any size you want.
This small tutorial will show you how to change/create your custome splash screen in 3D Studio Max. To make a custom splash screen open your favourite image editing program. I use Photoshop. Then make your splash screen any size you want.
 This article will create a special shelf for the tools we use the most in MAYA. We want to create a special shelf for the tools we use the most, we want to keep it fairly clean and not over-crowd it, so we can find the items quickly, and have a small learning curve.
This article will create a special shelf for the tools we use the most in MAYA. We want to create a special shelf for the tools we use the most, we want to keep it fairly clean and not over-crowd it, so we can find the items quickly, and have a small learning curve.
 This week we are discussing some areas of employment that needs some real coverage in general. Check what CyberSlacker is and if you are one of them.
This week we are discussing some areas of employment that needs some real coverage in general. Check what CyberSlacker is and if you are one of them.
 Cloud network devices are very important to us, so the company D-Link did something about that and they came up with a new network device. D-Link is unveiling another member of their family of Clouds: DNS-320L (Cloud ShareCenter 2-Bay Network Storage Enclosure).
Cloud network devices are very important to us, so the company D-Link did something about that and they came up with a new network device. D-Link is unveiling another member of their family of Clouds: DNS-320L (Cloud ShareCenter 2-Bay Network Storage Enclosure).
.png) This time we had the chance to try out a product from the Chinese firm D-Link, a renowned manufacturer of computer networking equipment. It is a product that is called Cloud Router and is classified by the marking DIR-605L. In the package, next to the router, you get a voltage adapter (5V DC, 1A), LAN cable, CD with instructions and software, as well as printed documentation.
This time we had the chance to try out a product from the Chinese firm D-Link, a renowned manufacturer of computer networking equipment. It is a product that is called Cloud Router and is classified by the marking DIR-605L. In the package, next to the router, you get a voltage adapter (5V DC, 1A), LAN cable, CD with instructions and software, as well as printed documentation.
 If your Mac is shiny and new or even shiny and used you might have a high confidence that your system will never fail. The saying goes: 'Pride goeth before the fall!' Take heed, no system, brand new or otherwise, is immune from data loss, a premature hard drive failure, or data corruption. Therefore, if you are still drawn in to this article then I am properly doing my job. I am trying to help you arm yourself to do battle against your eventual war with data loss. The good news is that there is a plethora of software out there branded as data recovery software for Mac.
If your Mac is shiny and new or even shiny and used you might have a high confidence that your system will never fail. The saying goes: 'Pride goeth before the fall!' Take heed, no system, brand new or otherwise, is immune from data loss, a premature hard drive failure, or data corruption. Therefore, if you are still drawn in to this article then I am properly doing my job. I am trying to help you arm yourself to do battle against your eventual war with data loss. The good news is that there is a plethora of software out there branded as data recovery software for Mac.
 We are going to discuss Data Replication. What in the world is Data Replication you ask? Well, we asked the same question when heard of it at first. But then, this is what this article is going to explain. No need for us to take away the mystery before reading the article.
We are going to discuss Data Replication. What in the world is Data Replication you ask? Well, we asked the same question when heard of it at first. But then, this is what this article is going to explain. No need for us to take away the mystery before reading the article.
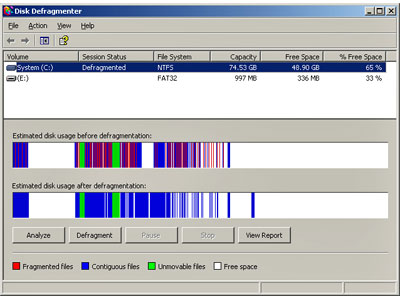 Defragmenting the hard drives on a system with the Windows XP operating system is a little different from the method in Windows 98/Me. The operation is done by using one of the Microsoft Management Consoles.
Defragmenting the hard drives on a system with the Windows XP operating system is a little different from the method in Windows 98/Me. The operation is done by using one of the Microsoft Management Consoles.
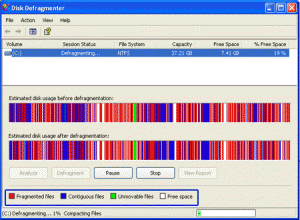 This article will show you a whole new way of defragmenting you computer and will explain why exactly we should defrag our computers every now and then.
This article will show you a whole new way of defragmenting you computer and will explain why exactly we should defrag our computers every now and then.
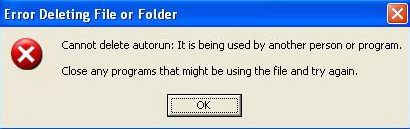 Find out many ways you can delete your undeletable files. When XP refuses to delete/modify a file; simply jump into the command prompt (Start>Run>"cmd") and modify the file from there. Windows-DOS seems to work around this bug. No need to wade through complex procedures for this one.
Find out many ways you can delete your undeletable files. When XP refuses to delete/modify a file; simply jump into the command prompt (Start>Run>"cmd") and modify the file from there. Windows-DOS seems to work around this bug. No need to wade through complex procedures for this one.
 The new model from the Dell series P (Professional) is embellished with thin edges and slightly curved lines, in a combination of mate black and gray. As a part of the highest class of the Dell offer, it has the right to a special treatment, so the quality of production of this screen is on the highest level, and it can also dance, you can rotate it in all axes.
The new model from the Dell series P (Professional) is embellished with thin edges and slightly curved lines, in a combination of mate black and gray. As a part of the highest class of the Dell offer, it has the right to a special treatment, so the quality of production of this screen is on the highest level, and it can also dance, you can rotate it in all axes.
 This is a Delphi tutorial that was probably made in a hap-hazard way but from what we gauge, its right on the money. For beginners as well as for moderate programmers. Delphi provides all the tools you need to develop, test and deploy Windows applications, including a large number of so-called reusable components.
Borland Delphi, in it's latest version, provides a cross platform solution when used with Borland Kylix - Borland's RAD tool for the Linux platform.
This is a Delphi tutorial that was probably made in a hap-hazard way but from what we gauge, its right on the money. For beginners as well as for moderate programmers. Delphi provides all the tools you need to develop, test and deploy Windows applications, including a large number of so-called reusable components.
Borland Delphi, in it's latest version, provides a cross platform solution when used with Borland Kylix - Borland's RAD tool for the Linux platform.

 Much like your car, your PC may sometimes alert you to the fact that something is wrong. When you take your car to the repair shop you probably tell the technician that it is making some strange noise that you have never heard before. This often helps the technician diagnose the problem.
Much like your car, your PC may sometimes alert you to the fact that something is wrong. When you take your car to the repair shop you probably tell the technician that it is making some strange noise that you have never heard before. This often helps the technician diagnose the problem.
Computers have the same advantage. Often the noises that a PC makes will tell you what the problem is. I have tried to match the noise, tough to do when writing it, with the problem. Listen to your PC and then check below to see if you hear a match. Remember, if your PC is making noise that it didn't make when it was new means it has a problem and depending on the severity could cause permanent damage.

 DoS stand for denial-of-service attack, a type of attack on a network that is designed to bring the network to its knees by flooding it with useless traffic. While DoS attacks do not usually result in information theft or any security loss for a company, they can cost an organization both time and money while their network services are down.
DoS stand for denial-of-service attack, a type of attack on a network that is designed to bring the network to its knees by flooding it with useless traffic. While DoS attacks do not usually result in information theft or any security loss for a company, they can cost an organization both time and money while their network services are down.
 Check out the background on DHTML and how a beginner should go about learning it. This tutorial is for those who have already been acquainted with HTML and have a solid HTML grasp. Once that is established, this tutorial is a piece of cake. DHTML is NOT a scripting language (like JavaScript), but merely a browser feature- or enhancement- that gives your browser the ability to be dynamic. DHTML is a collection of features that together, enable your web page to be dynamic.
Check out the background on DHTML and how a beginner should go about learning it. This tutorial is for those who have already been acquainted with HTML and have a solid HTML grasp. Once that is established, this tutorial is a piece of cake. DHTML is NOT a scripting language (like JavaScript), but merely a browser feature- or enhancement- that gives your browser the ability to be dynamic. DHTML is a collection of features that together, enable your web page to be dynamic. 
 Ever make it just in time for work after driving through rush hour traffic and realize that you've left an important file on your computer at home? Or have you ever had to work late in the office because you don't have access to files, applications, or shared resources at home? Well maybe your life has just become way easier. Introducing, GoToMyPC! A wonderful little service that'll let you access your home or work computer from anywhere! It takes two minutes to download this amazing software onto your computer and you'll have the power to access your computer from any web browser on any computer. A simple little technology of PC-to-PC connection or as GoToMyPC calls it, "Remote-Access Solution" will go a long way for anyone.
Ever make it just in time for work after driving through rush hour traffic and realize that you've left an important file on your computer at home? Or have you ever had to work late in the office because you don't have access to files, applications, or shared resources at home? Well maybe your life has just become way easier. Introducing, GoToMyPC! A wonderful little service that'll let you access your home or work computer from anywhere! It takes two minutes to download this amazing software onto your computer and you'll have the power to access your computer from any web browser on any computer. A simple little technology of PC-to-PC connection or as GoToMyPC calls it, "Remote-Access Solution" will go a long way for anyone.
 This is a good article to show you the differences between spyware and adware. Shows you what you can do to avoid them and protect yourself once infested. Adware is any computer program or software package in which advertisements or other marketing material are included with or automatically loaded by the software and displayed or played back after installation.
This is a good article to show you the differences between spyware and adware. Shows you what you can do to avoid them and protect yourself once infested. Adware is any computer program or software package in which advertisements or other marketing material are included with or automatically loaded by the software and displayed or played back after installation.
 ASP.NET pages have several semantic changes from existing ASP pages. The following issues are the ones most likely to affect you. Because of ASP Net's compiled nature, it supports only a single language on a page. However, it is still possible to have multiple pages, each with a separate language, within a single application.
ASP.NET pages have several semantic changes from existing ASP pages. The following issues are the ones most likely to affect you. Because of ASP Net's compiled nature, it supports only a single language on a page. However, it is still possible to have multiple pages, each with a separate language, within a single application.
 This article will discuss the differences between the Linux and Windows operating software's; we discuss some of the pro's and con's of each system. From this point forward we will discuss some of the more prominent ways in which Linux deferrers from Windows.
This article will discuss the differences between the Linux and Windows operating software's; we discuss some of the pro's and con's of each system. From this point forward we will discuss some of the more prominent ways in which Linux deferrers from Windows.
 There are various types of Internet connections, and each one of them has different properties. This text should help you determine which is best for you.
There are various types of Internet connections, and each one of them has different properties. This text should help you determine which is best for you.
 Windows startup after a sudden shutdown leads to an annoying feature chkdsk. It automatically checks the entire drive for any infected files. This checking can be skipped by pressing any key before it starts during the blue screen...
Windows startup after a sudden shutdown leads to an annoying feature chkdsk. It automatically checks the entire drive for any infected files. This checking can be skipped by pressing any key before it starts during the blue screen...
 Whenever either Windows crashes, you will be asked if you want to send an error report to Microsoft. It's annoying, so here's a way to disable it.
Whenever either Windows crashes, you will be asked if you want to send an error report to Microsoft. It's annoying, so here's a way to disable it.
 Sick of seeing the Outlook Express splash screen every time you open the program? This settings will allow you to remove it. For Outlook 4.0 and below the key is [HKEY_CURRENT_USER\Software\Microsoft\Outlook Express]
Sick of seeing the Outlook Express splash screen every time you open the program? This settings will allow you to remove it. For Outlook 4.0 and below the key is [HKEY_CURRENT_USER\Software\Microsoft\Outlook Express]
 Did you recently find out that after your PC starts up fresh, your internet doesn't work? So you probably tried everything and the only thing that seems to work is to disable the "Local Area Connection" (adapter), and then to enable it back again. At least that's what happened to me.
Did you recently find out that after your PC starts up fresh, your internet doesn't work? So you probably tried everything and the only thing that seems to work is to disable the "Local Area Connection" (adapter), and then to enable it back again. At least that's what happened to me.
I've had this problem for almost a year now but I finally want it stop. All the resources online tell me that it's probably my network driver that may need an update. Well, all my drivers are updated, and the problem still remains. Now What? Okay, I'll be honest... I don't know why it happens but 1 out of every 10 or 12 PC's will come across this problem.

 Article discusses computer history as far back as 5,000 years! Amazing story on the history of the computer. It was 1642. That year the 18-year-old son of a French tax collector, or the well known Blaise Pascal, invented what he called a numerical wheel calculator to help his father with his duties.
Article discusses computer history as far back as 5,000 years! Amazing story on the history of the computer. It was 1642. That year the 18-year-old son of a French tax collector, or the well known Blaise Pascal, invented what he called a numerical wheel calculator to help his father with his duties.
 It's a very common problem that many newbies almost always ignore to correct; that when you try to the Disk Cleanup tool, it may stop responding and you may receive the following message. Disk Cleanup is calculating how much space you will be able to free on (C:). This may take a few minutes to complete. Scanning: Compress old files
It's a very common problem that many newbies almost always ignore to correct; that when you try to the Disk Cleanup tool, it may stop responding and you may receive the following message. Disk Cleanup is calculating how much space you will be able to free on (C:). This may take a few minutes to complete. Scanning: Compress old files
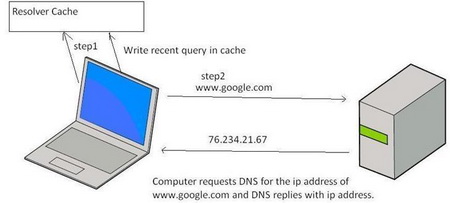 To help speed up Web browsing, Windows XP comes with a local cache containing any DNS addresses that have been looked up recently. Once an URL has been resolved by an Internet name server into a numerical IP, the information is stored locally. Anytime your browser requests an URL, Windows XP first looks in the local cache to see if it is there before querying the external name server used by your ISP. If it finds the resolved URL locally it uses that IP. This is supposed to save time and cut down on Web traffic.
To help speed up Web browsing, Windows XP comes with a local cache containing any DNS addresses that have been looked up recently. Once an URL has been resolved by an Internet name server into a numerical IP, the information is stored locally. Anytime your browser requests an URL, Windows XP first looks in the local cache to see if it is there before querying the external name server used by your ISP. If it finds the resolved URL locally it uses that IP. This is supposed to save time and cut down on Web traffic.
 This DOS tutorial will completely get you off the right way if you're new to DOS. Remember, DOS is "not dead". It's just been tucked away under the carpet as the newer versions of Windows keep rolling out the assembly line. However, DOS is still an excellent choice to automate tons of chores.
This DOS tutorial will completely get you off the right way if you're new to DOS. Remember, DOS is "not dead". It's just been tucked away under the carpet as the newer versions of Windows keep rolling out the assembly line. However, DOS is still an excellent choice to automate tons of chores.
 Using Peer to Peer networks to download music for no cost is an activity that is, although not very much approved, hugely popular in youth and even in adults.
Using Peer to Peer networks to download music for no cost is an activity that is, although not very much approved, hugely popular in youth and even in adults.
 There are two key advantages that VPN gives to organizations who are seeking to have safe and secure networks and offer them to their client base. Those advantages are a lot less money to pay and a great network scalability. It is also very easy to use, so clients that join VPN networks won't find it difficult to do what they want.
There are two key advantages that VPN gives to organizations who are seeking to have safe and secure networks and offer them to their client base. Those advantages are a lot less money to pay and a great network scalability. It is also very easy to use, so clients that join VPN networks won't find it difficult to do what they want.
 For those who have never encountered these types of services, this is how Dropbox works. You first need to download a small app from the official site and then install it on your computer which you will put in the system tray. In your Home folder a subfolder will be created called Dropbox and that will serve the purpose of a local folder for online synchronization. Everything you put in that folder will be put online immediately. Everything you delete will be removed from the Web.
For those who have never encountered these types of services, this is how Dropbox works. You first need to download a small app from the official site and then install it on your computer which you will put in the system tray. In your Home folder a subfolder will be created called Dropbox and that will serve the purpose of a local folder for online synchronization. Everything you put in that folder will be put online immediately. Everything you delete will be removed from the Web.
 Creating a duplicate movie clip in flash is not the most useful thing you'll encounter. However, it is a good skill to have as it incorporates creating a tween, and writing your own actionscript.
Creating a duplicate movie clip in flash is not the most useful thing you'll encounter. However, it is a good skill to have as it incorporates creating a tween, and writing your own actionscript.
 This weeks article will explain to you all those Digital Disk Formats that are out there. A very insightful article written to bring the confusion to end, don't miss it. DVD shorts for digital versatile disc or digital video disc, a type of optical disk technology similar to the CD-ROM. A DVD holds a minimum of 4.7GB of data, enough for a full-length movie.
This weeks article will explain to you all those Digital Disk Formats that are out there. A very insightful article written to bring the confusion to end, don't miss it. DVD shorts for digital versatile disc or digital video disc, a type of optical disk technology similar to the CD-ROM. A DVD holds a minimum of 4.7GB of data, enough for a full-length movie. 
 We cannot have our networks secured from anyone unless we know a bit about security itself. Well here is your chance to get to know what is involved in E-Security. And remember, "There Always Watching"! The owners of storage and processing systems must take very specific steps to protect their assets and monitor their networks to counter the security threats.
We cannot have our networks secured from anyone unless we know a bit about security itself. Well here is your chance to get to know what is involved in E-Security. And remember, "There Always Watching"! The owners of storage and processing systems must take very specific steps to protect their assets and monitor their networks to counter the security threats. 
 Internet business is a very important thing. It can bring you a lot of things, primarily money, but it can also help you make new contacts and meet new people. But internet business is not an overly simple thing. There are a lot of things you need to know before venturing in the world of internet business.
Internet business is a very important thing. It can bring you a lot of things, primarily money, but it can also help you make new contacts and meet new people. But internet business is not an overly simple thing. There are a lot of things you need to know before venturing in the world of internet business.
 Style Sheets in many ways is even easier to get a grip of than even HTML yet very few people use it because of lack of insight into this technology. Well dont lack any longer, get your behind here and read all about it. Cascading style sheets (CSS) are an elegantly designed extension to the Web and one of the greatest hopes for recapturing the Web's ideal of separation of presentation and content.
Style Sheets in many ways is even easier to get a grip of than even HTML yet very few people use it because of lack of insight into this technology. Well dont lack any longer, get your behind here and read all about it. Cascading style sheets (CSS) are an elegantly designed extension to the Web and one of the greatest hopes for recapturing the Web's ideal of separation of presentation and content. 
 Learning at your own pace and at low cost. This is the essential description of this concept in a few words. Anybody who deals with this topic in detail knows that it needs much more self-discipline to take a course at home than going to a seminar. While searching for appropriate courses on the Internet, there is one fact evident: Available offers mostly consist of static HTML-pages that may be spiced-up with some illustrations at best. Many presentations are more like a textbook or article than interactive Internet content.
Learning at your own pace and at low cost. This is the essential description of this concept in a few words. Anybody who deals with this topic in detail knows that it needs much more self-discipline to take a course at home than going to a seminar. While searching for appropriate courses on the Internet, there is one fact evident: Available offers mostly consist of static HTML-pages that may be spiced-up with some illustrations at best. Many presentations are more like a textbook or article than interactive Internet content.


 Many guidelines have been published about computer-related stress injuries. This page summarizes some of my favorite suggestions. Unfortunately, this page reflects the sad voice of experience. I have used these exercises myself, after suffering from injuries with my hand, wrist, arm, back, and eyes. If I had followed my own advice, I might have been in better shape today.
Many guidelines have been published about computer-related stress injuries. This page summarizes some of my favorite suggestions. Unfortunately, this page reflects the sad voice of experience. I have used these exercises myself, after suffering from injuries with my hand, wrist, arm, back, and eyes. If I had followed my own advice, I might have been in better shape today.
 Once you have learned some programming languages, you feel yourself completely prepared to enter into the programming world, and start working on the programming languages that you have learned. Many students also feel that they have learned extra things which might be helpful in their programming careers. The matter of fact is that the real world is entirely different from what you have been taught in the classrooms.
Once you have learned some programming languages, you feel yourself completely prepared to enter into the programming world, and start working on the programming languages that you have learned. Many students also feel that they have learned extra things which might be helpful in their programming careers. The matter of fact is that the real world is entirely different from what you have been taught in the classrooms.
 The Epson WorkForce printer series managed to make a serious competition to laser devices in the office surroundings. With the goal of suppressing laser devices right from the segment where they are most often used - in everyday printing of black and white documents, Epson offered a monochromatic printer WorkForce M100 as an alternative.
The Epson WorkForce printer series managed to make a serious competition to laser devices in the office surroundings. With the goal of suppressing laser devices right from the segment where they are most often used - in everyday printing of black and white documents, Epson offered a monochromatic printer WorkForce M100 as an alternative.
 Research that has recently been conducted in the USA says that the number of sold E-books, for the first time, was more than the number of paper editions. Epubor Ultimate Converter has simplified the conversion of the format. It supports a larger number of known formats, as well as e-book readers, it doesn't even have to know what formats that reader knows. It is enough to choose from the list of devices it has a device for which it wants to.
Research that has recently been conducted in the USA says that the number of sold E-books, for the first time, was more than the number of paper editions. Epubor Ultimate Converter has simplified the conversion of the format. It supports a larger number of known formats, as well as e-book readers, it doesn't even have to know what formats that reader knows. It is enough to choose from the list of devices it has a device for which it wants to.
 Brief discussion on hacking and how it affects our war on terrorism. And how some hacking is in the interest of the US while some hacking hurts us in this current war. Writer also mentions role of Hackers, Crackers, and also Phreakers.
Brief discussion on hacking and how it affects our war on terrorism. And how some hacking is in the interest of the US while some hacking hurts us in this current war. Writer also mentions role of Hackers, Crackers, and also Phreakers.
 Managed hosting differs from standard hosting in that customers are supplied not only with an unshared, dedicated server, but with a full array of management services as well. Managed hosting has sometimes been described as "hands-free hosting" or "worry-free hosting." While these terms may be somewhat hyperbolic, it's certainly true that managed providers strive to relieve their customers of most routine hosting chores.
Managed hosting differs from standard hosting in that customers are supplied not only with an unshared, dedicated server, but with a full array of management services as well. Managed hosting has sometimes been described as "hands-free hosting" or "worry-free hosting." While these terms may be somewhat hyperbolic, it's certainly true that managed providers strive to relieve their customers of most routine hosting chores.
 This article was submitted by one of the visitors. It seems to have been written a long time ago however, the information in it is invaluable. Find out what a hacker is from a hackers point of view. It just may surprise you to hear what the writer has to say.
This article was submitted by one of the visitors. It seems to have been written a long time ago however, the information in it is invaluable. Find out what a hacker is from a hackers point of view. It just may surprise you to hear what the writer has to say.
 The mouse is probably the most used periphery on computers. The touchscreen technology is a standard on many devices in the past few years, so the mouse is resisting from being replaced from the throne. But, what if we want to move the cursor in a different way for some reason? Well, if you own a web camera and a program called eViacam, you can easily do that by simply moving your face.
The mouse is probably the most used periphery on computers. The touchscreen technology is a standard on many devices in the past few years, so the mouse is resisting from being replaced from the throne. But, what if we want to move the cursor in a different way for some reason? Well, if you own a web camera and a program called eViacam, you can easily do that by simply moving your face.
 Everywhere you go, you're bound to get them. Popup ads claiming you've just won a million dollars, popup ads "alerting" you that your computer is vulnerable to hackers, and popup ads for some questionable websites. So, what can you do about them?
Everywhere you go, you're bound to get them. Popup ads claiming you've just won a million dollars, popup ads "alerting" you that your computer is vulnerable to hackers, and popup ads for some questionable websites. So, what can you do about them?
 Do you like tinkering with Windows Command Line? It is an awesome way to learn batch scripting. But at times you may have a series of batch files that you would want to run or execute. Well, many folks do not know but there is a method that is used to do exactly that.
Do you like tinkering with Windows Command Line? It is an awesome way to learn batch scripting. But at times you may have a series of batch files that you would want to run or execute. Well, many folks do not know but there is a method that is used to do exactly that.
 Already now we can take a look at what is in the period in front of us and try to predict what is waiting on the fields of new gadgets, computer technologies and consumer technology. The last train for Nokia, Blackberry and Yahoo! Yesterdays giants are now trying to rediscover the way to profit. Will Nokia place all their eggs in Microsoft basket? What new things can the Blackberry (RIM) offer on the smartphone platform that has made their earlier concept obsolete. Can Yahoo become relevant again?
Already now we can take a look at what is in the period in front of us and try to predict what is waiting on the fields of new gadgets, computer technologies and consumer technology. The last train for Nokia, Blackberry and Yahoo! Yesterdays giants are now trying to rediscover the way to profit. Will Nokia place all their eggs in Microsoft basket? What new things can the Blackberry (RIM) offer on the smartphone platform that has made their earlier concept obsolete. Can Yahoo become relevant again?
 Upon request of some visitor in our forum. If you have been dealing with Outlook Express and depending on it for your emails then you must know this.
Upon request of some visitor in our forum. If you have been dealing with Outlook Express and depending on it for your emails then you must know this.
 I figure I can't be the only Gamer/coder out there that doesn't still want to run this program. I know there are better Macro creating options out there but the ease and speed/price of this program I've used since 1997 and I'm hoping someone knows how to get it to run in Windows 7.
I figure I can't be the only Gamer/coder out there that doesn't still want to run this program. I know there are better Macro creating options out there but the ease and speed/price of this program I've used since 1997 and I'm hoping someone knows how to get it to run in Windows 7.
 Social networks on the Internet today represent contents that are very popular among the online users, especially among young people. Besides being given some kind of trend, which contributes to their popularity, they bring new possibilities in communication and they make it easier to make contacts and the use and sharing of various contents, which makes them appealing.
Social networks on the Internet today represent contents that are very popular among the online users, especially among young people. Besides being given some kind of trend, which contributes to their popularity, they bring new possibilities in communication and they make it easier to make contacts and the use and sharing of various contents, which makes them appealing.
 If you don't know what Facebook is (if you have been hiding under a rock for the past 9 years) it is an online social networking service, whose name stems from the colloquial name for the book given to students at the start of the academic year by some university administrations in the United States to help students get to know each other.
If you don't know what Facebook is (if you have been hiding under a rock for the past 9 years) it is an online social networking service, whose name stems from the colloquial name for the book given to students at the start of the academic year by some university administrations in the United States to help students get to know each other.
 Here's how to put an icon on your desktop that'll shut down your machine quickly. Buried deep inside Windows XP lurks a little-known program called shutdown.
Here's how to put an icon on your desktop that'll shut down your machine quickly. Buried deep inside Windows XP lurks a little-known program called shutdown.

 Here we have another version of the Fedora, more precisely the eighteenth. Let us remind ourselves, Fedora begins its life back in early 2003. As a free distribution that came out of the developers house RedHat team with the goal to achieve predominance in the field of free Linux distributions. Ten years later, they managed what they intended to and today Fedora is definitely one of the best distributions you can find.
Here we have another version of the Fedora, more precisely the eighteenth. Let us remind ourselves, Fedora begins its life back in early 2003. As a free distribution that came out of the developers house RedHat team with the goal to achieve predominance in the field of free Linux distributions. Ten years later, they managed what they intended to and today Fedora is definitely one of the best distributions you can find.
 Just like their human creators and developers, computers can be broken down into a series of generations, each with their own distinct technology and feature set. At the current time, many computer scientists break computing into four separate generations, with an exciting fifth generation currently on the horizon. This new generation of computing, which takes the form of so-called artificial intelligence, will be unlike its predecessors -- noted more for its features than its hardware.
Just like their human creators and developers, computers can be broken down into a series of generations, each with their own distinct technology and feature set. At the current time, many computer scientists break computing into four separate generations, with an exciting fifth generation currently on the horizon. This new generation of computing, which takes the form of so-called artificial intelligence, will be unlike its predecessors -- noted more for its features than its hardware.
 With the increase of capacity in hard drives and the increase of speed of the Internet there is the growth of available multimedia material on users computers. Sometimes it is difficult to find your way in a bunch of files and directories, where there are countless episodes of favorite shows or hours of movies that are waiting for some free time. Although modern file managers have advanced sorting options, renaming or some other searching, they still are not meant for handling a large number of files with multimedia content, that can be pretty diverse.
With the increase of capacity in hard drives and the increase of speed of the Internet there is the growth of available multimedia material on users computers. Sometimes it is difficult to find your way in a bunch of files and directories, where there are countless episodes of favorite shows or hours of movies that are waiting for some free time. Although modern file managers have advanced sorting options, renaming or some other searching, they still are not meant for handling a large number of files with multimedia content, that can be pretty diverse. 
 This small BATCH tutorial will become your door-way to becoming a good batch files creator or even a great one. Batch files make our lives a bit easier without a doubt. Learn how you can create your batch files within minutes. No experience needed.
This small BATCH tutorial will become your door-way to becoming a good batch files creator or even a great one. Batch files make our lives a bit easier without a doubt. Learn how you can create your batch files within minutes. No experience needed.
 ...however, I soon discovered that Photoshop CS3 would freeze and crash the system whenever I attempted to save a file, even though it would function perfectly normally in every other way. I would have reported this as a blog post to 'rebut' the installation trick, except that it made absolutely no sense that the problem should be related to the installation and, additionally, I had received messages from others that had used the registry hack to successfully install CS3 under XP SP1 and were having no problems.
...however, I soon discovered that Photoshop CS3 would freeze and crash the system whenever I attempted to save a file, even though it would function perfectly normally in every other way. I would have reported this as a blog post to 'rebut' the installation trick, except that it made absolutely no sense that the problem should be related to the installation and, additionally, I had received messages from others that had used the registry hack to successfully install CS3 under XP SP1 and were having no problems.
 Flash is the web designers most powerful tool for creating interactive websites, and to provide memorable digital experiences to the visitors. With flash web design, companies can create professional designs and interactive content, embellished with video, graphics and animation. Flash animations certainly make a website bustle with life due to the presence of animation that can arrest the visitor's attention.
Flash is the web designers most powerful tool for creating interactive websites, and to provide memorable digital experiences to the visitors. With flash web design, companies can create professional designs and interactive content, embellished with video, graphics and animation. Flash animations certainly make a website bustle with life due to the presence of animation that can arrest the visitor's attention. 
 This tutorial covers the basic concepts of flash and animation and how to make a Flash movie. Would be a great tutorial for the beginning level.
This tutorial covers the basic concepts of flash and animation and how to make a Flash movie. Would be a great tutorial for the beginning level.
 OK guys, this script is a simple file based counter. This is meant for sites that do not run a db and instead, use a file and a cookie. It isn't the best I've seen but it's simple. Consider this as a tutorial.
OK guys, this script is a simple file based counter. This is meant for sites that do not run a db and instead, use a file and a cookie. It isn't the best I've seen but it's simple. Consider this as a tutorial.
 The fourth generation of computers began around 1975 and lasted until around 1985. It recognizes that period of computer history when the integrated circuit chip evolved into the microprocessor, a "computer on a chip." As a result, the first functional desktop computers came into being, beginning with the hobbyist DIY experimental models, such as the Altair 8800 mail-order kit, and progressing to the early commercial models such as the Commodore and the Tandy TRS-80.
The fourth generation of computers began around 1975 and lasted until around 1985. It recognizes that period of computer history when the integrated circuit chip evolved into the microprocessor, a "computer on a chip." As a result, the first functional desktop computers came into being, beginning with the hobbyist DIY experimental models, such as the Altair 8800 mail-order kit, and progressing to the early commercial models such as the Commodore and the Tandy TRS-80.

 The term Flipbook is used for electronic books that mimic the look and usability of classic books. The pages are flipped in the same way as in paper editions, and if you want, you can turn on the sound that the paper makes when flipping. All is subordinated to the feeling that comes with holding a book. That is done by the conversion of PDF in Flash format.
The term Flipbook is used for electronic books that mimic the look and usability of classic books. The pages are flipped in the same way as in paper editions, and if you want, you can turn on the sound that the paper makes when flipping. All is subordinated to the feeling that comes with holding a book. That is done by the conversion of PDF in Flash format.
 Increase your sales and dramatically lower your costs by using freelancers. The average job is under $200!
Increase your sales and dramatically lower your costs by using freelancers. The average job is under $200!
 Many products come and go into the market. But only a few find a stable position in it and establish their supremacy over all other competitors. Similarly, many operating systems have made entry into the international arena of computers but only a few have proven to be outright successful ones.
Many products come and go into the market. But only a few find a stable position in it and establish their supremacy over all other competitors. Similarly, many operating systems have made entry into the international arena of computers but only a few have proven to be outright successful ones.
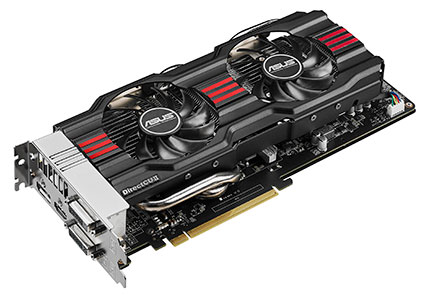 Asus Presented the graphic card GeForce GTX 770 DirectCU II. The card combines a redesigned DirectCU II cooling, digital control of power DIGI+VRM and durable Super Alloy Power components on the newest graphic card from the highest class.
Asus Presented the graphic card GeForce GTX 770 DirectCU II. The card combines a redesigned DirectCU II cooling, digital control of power DIGI+VRM and durable Super Alloy Power components on the newest graphic card from the highest class. 
 This tutorial discusses miscellaneous points about reference, cheating, and why we like certain types of images better than others.
This tutorial discusses miscellaneous points about reference, cheating, and why we like certain types of images better than others.
 This tutorial is a general Oracle Tutorial and should not be confused for Oracle Certification Tutorial. It will get any beginner up and running and will be a handy too for the advanced user as well.
This tutorial is a general Oracle Tutorial and should not be confused for Oracle Certification Tutorial. It will get any beginner up and running and will be a handy too for the advanced user as well.
 The history of computer development is often referred to in reference to the different generations of computing devices. A generation refers to the state of improvement in the development of a product. This term is also used in the different advancements of computer technology. With each new generation, the circuitry has gotten smaller and more advanced than the previous generation before it. As a result of the miniaturization, speed, power, and memory of computers has proportionally increased. New discoveries are constantly being developed that affect the way we live, work and play.
The history of computer development is often referred to in reference to the different generations of computing devices. A generation refers to the state of improvement in the development of a product. This term is also used in the different advancements of computer technology. With each new generation, the circuitry has gotten smaller and more advanced than the previous generation before it. As a result of the miniaturization, speed, power, and memory of computers has proportionally increased. New discoveries are constantly being developed that affect the way we live, work and play.
 But how? If you have computer skill but no experience (or qualifications), the employment agencies will tell you the same old line, "You need experience before anyone will look at you."
But how? If you have computer skill but no experience (or qualifications), the employment agencies will tell you the same old line, "You need experience before anyone will look at you."
It's just plain old Catch-22. You need the work to get the experience but you can't get that first job to give you a track record and therefore verifiable experience. With this logic, it amazes me that anyone actually gets into IT!
Qualifications help but even that is no guarantee nowadays of getting an IT Job. And what do you do when you don't have qualifications but you want to start now? I mean right now, not 3 months later after you've paid a fortune for certification and given up your job to have enough study time.
All is not lost. You have two alternatives.

 The tutorial answers many common questions people have about WAMP. The ultimate goal of this tutorial is to help you determine if WAMP is the solution you are looking for by providing the advantages and disadvantages of WAMP. WAMP is a powerful backend web development and hosting environment integrated from Apache, MySQL and PHP. Using Apache as a web server, MySQL as a database server, and PHP as a server side script engine, WAMP controls all these components using an intuitive interface.
The tutorial answers many common questions people have about WAMP. The ultimate goal of this tutorial is to help you determine if WAMP is the solution you are looking for by providing the advantages and disadvantages of WAMP. WAMP is a powerful backend web development and hosting environment integrated from Apache, MySQL and PHP. Using Apache as a web server, MySQL as a database server, and PHP as a server side script engine, WAMP controls all these components using an intuitive interface.
 Aivia Osmium is a keyboard meant for gamers, named after the worlds most dense element, suggesting that the new product is characterized by toughness, but also mass. The mechanical pressure keys don't offer a lot of resistance, and it's very comfortable to use. The keys react after 2 millimeters, and the maximum movement is 4 millimeters. The keys have a back lighting, which is customized by a little wheel in the top area, next to the sound control wheel. On the left side of the control area there is 5 macro keys, essential for gaming. You can use a driver to assign a certain function to ...
Aivia Osmium is a keyboard meant for gamers, named after the worlds most dense element, suggesting that the new product is characterized by toughness, but also mass. The mechanical pressure keys don't offer a lot of resistance, and it's very comfortable to use. The keys react after 2 millimeters, and the maximum movement is 4 millimeters. The keys have a back lighting, which is customized by a little wheel in the top area, next to the sound control wheel. On the left side of the control area there is 5 macro keys, essential for gaming. You can use a driver to assign a certain function to ...
 When talking about external hard drives, lately we often think about companies that don't have making hard drives as their primary area of work. That situation points to that external hard drives are still confection and expendable goods. Because of that it was our pleasure to test a hard drive from the oldest producer of hard drives there is - Seagate.
When talking about external hard drives, lately we often think about companies that don't have making hard drives as their primary area of work. That situation points to that external hard drives are still confection and expendable goods. Because of that it was our pleasure to test a hard drive from the oldest producer of hard drives there is - Seagate.
 Lets take a look at the grim reality of the US job market. Get a glimpse of all that's in and out.
Lets take a look at the grim reality of the US job market. Get a glimpse of all that's in and out.
 Mountain bikers use space-age alloy components to reduce the heft of their rides. NASCAR mechanics tune their cars engines for days before the weekend race. The ultimate purpose of these alterations, of course, is to increase speed, and you dont have to be a rabid sports jock to appreciate quickness especially if you are a PC user enduring agonizingly slow startups.
Mountain bikers use space-age alloy components to reduce the heft of their rides. NASCAR mechanics tune their cars engines for days before the weekend race. The ultimate purpose of these alterations, of course, is to increase speed, and you dont have to be a rabid sports jock to appreciate quickness especially if you are a PC user enduring agonizingly slow startups.
 If you have not dived into the Chrome Flags - experimental laboratory with new features, now is the time to do so. Only search "chrome :/ / flags" on the network and get a list of interesting settings, though some will work on your OS and some will not. If you are using Windows, Linux or Chrome Os, this setting will fill passwords for you when you open the page to create your account. All you need is to find the "Enable Password Generation".
If you have not dived into the Chrome Flags - experimental laboratory with new features, now is the time to do so. Only search "chrome :/ / flags" on the network and get a list of interesting settings, though some will work on your OS and some will not. If you are using Windows, Linux or Chrome Os, this setting will fill passwords for you when you open the page to create your account. All you need is to find the "Enable Password Generation".
 Google Drive is in many ways modeled on Dropbox, but it is typical of Google, the emphasis is placed on linking with other services offered by the company. For example, if you use Google Docs, and had taken the documents, at the first sync they will be copied in your local folder, or space for Google Docs documents will automatically be associated with Google Drive. Free users get 5 GB of free space, but it should be noted that the area is common to Google Drive and the pictures you post in Google+ albums (if you use this service).
Google Drive is in many ways modeled on Dropbox, but it is typical of Google, the emphasis is placed on linking with other services offered by the company. For example, if you use Google Docs, and had taken the documents, at the first sync they will be copied in your local folder, or space for Google Docs documents will automatically be associated with Google Drive. Free users get 5 GB of free space, but it should be noted that the area is common to Google Drive and the pictures you post in Google+ albums (if you use this service).
 If you're like myself, you would easily come to a realization that web compatible fonts are down-right dull for content and even more so for content headlines. People have come up with many ingenious ways to counter this problem. However, each of these methods has its downside. Remember the most important aspect of Google Web Fonts; they not only look good, but they are just fonts to the search engines that spider your website.
If you're like myself, you would easily come to a realization that web compatible fonts are down-right dull for content and even more so for content headlines. People have come up with many ingenious ways to counter this problem. However, each of these methods has its downside. Remember the most important aspect of Google Web Fonts; they not only look good, but they are just fonts to the search engines that spider your website.

 However, when 40% of the US Govt.'s own websites fail security tests, there is no sense of respect there but a shear lack thereof. The article mainly talks about DNS Security Extension (DNSSEC) which is an added security measure to DNS. However, DNSSEC itself is not the only method to be implemented by far.
However, when 40% of the US Govt.'s own websites fail security tests, there is no sense of respect there but a shear lack thereof. The article mainly talks about DNS Security Extension (DNSSEC) which is an added security measure to DNS. However, DNSSEC itself is not the only method to be implemented by far.
 If you ever had a problem dividing partitions and working with file systems on your Linux OS, we have a cure for you. It is called GParted Partition Editor, and in the case you have installed some GNOME distribution, it is likely that you have encountered it.
If you ever had a problem dividing partitions and working with file systems on your Linux OS, we have a cure for you. It is called GParted Partition Editor, and in the case you have installed some GNOME distribution, it is likely that you have encountered it.
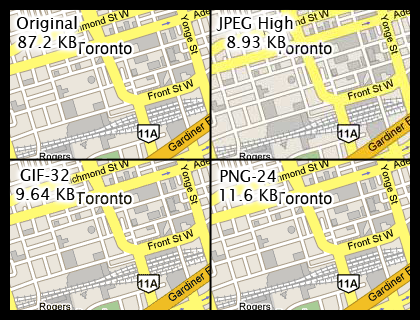 Here is a little insight that one ought to have when it comes to graphics on the web. Learn the difference between JPEG, GIFs, and PNG file formats. It could come handy someday so check it out.
Here is a little insight that one ought to have when it comes to graphics on the web. Learn the difference between JPEG, GIFs, and PNG file formats. It could come handy someday so check it out.
 Greenshot is a great program that does its job perfectly. For every stated option in the menu there exists a corresponding shortcut, so the button 'PrintScreen' will turn on the saving of a region, 'Shift+PrintScreen' captures the last selected part, 'Alt+PrintScreen' saves the active window and 'Ctrl+PrintScreen' the whole screen.
Greenshot is a great program that does its job perfectly. For every stated option in the menu there exists a corresponding shortcut, so the button 'PrintScreen' will turn on the saving of a region, 'Shift+PrintScreen' captures the last selected part, 'Alt+PrintScreen' saves the active window and 'Ctrl+PrintScreen' the whole screen.
 Excel is a very useful tool and if you regularly work on computers you should know as much as possible about it. In the following text two options in Excel will be explained, grouping subtotals and hiding worksheets.Imagine you are working on sales in stores that are located on various locations....
Excel is a very useful tool and if you regularly work on computers you should know as much as possible about it. In the following text two options in Excel will be explained, grouping subtotals and hiding worksheets.Imagine you are working on sales in stores that are located on various locations....
 Here are some quick tips to stay safe on the net from con artists and thier scams. This is more of a survival guide then a tech related column.
Here are some quick tips to stay safe on the net from con artists and thier scams. This is more of a survival guide then a tech related column.
 Listening to music on a computer is such a silly thing that it is almost implies. In Linux, and other free systems, there are a lot of programs with this purpose, from console players to advanced multimedia managers. The offer is more than enough and everybody will surely find what fits him, but it is hard to stand out in that crowd.
Listening to music on a computer is such a silly thing that it is almost implies. In Linux, and other free systems, there are a lot of programs with this purpose, from console players to advanced multimedia managers. The offer is more than enough and everybody will surely find what fits him, but it is hard to stand out in that crowd.
 Dont worry, its not a history lesson. Well maybe it is, but its worth knowing where it originated from. Hacking is rapidly becoming a problem not only to big time corporations but also to simple individuals like ourselves.
Dont worry, its not a history lesson. Well maybe it is, but its worth knowing where it originated from. Hacking is rapidly becoming a problem not only to big time corporations but also to simple individuals like ourselves.
 Many hackers have decided that if they're going to learn computer security by breaking into servers, those servers might as well belong to people they don't like.
Many hackers have decided that if they're going to learn computer security by breaking into servers, those servers might as well belong to people they don't like.
 If you're reading this, chances are you haven't yet signed up for Paypal. So let's keep reading a bit more about it. If you haven't signed up yet, this article will most definetly save you a lot of worries, especially if you are a small business owner.
If you're reading this, chances are you haven't yet signed up for Paypal. So let's keep reading a bit more about it. If you haven't signed up yet, this article will most definetly save you a lot of worries, especially if you are a small business owner.
 Everyone has a computer. Everyone needs a computer. And, most everyone spends way too much money on a computer that doesn't end up performing as well as it could. Computer manufacturers - or should we say computer assemblers, because that's really all they are - are phenomenal marketers who use information asymmetry to their advantage. Basically, computer assemblers bank on the fact that you, the consumer, do not know enough about computers. This allows them to sell you computers that cost more ...
Everyone has a computer. Everyone needs a computer. And, most everyone spends way too much money on a computer that doesn't end up performing as well as it could. Computer manufacturers - or should we say computer assemblers, because that's really all they are - are phenomenal marketers who use information asymmetry to their advantage. Basically, computer assemblers bank on the fact that you, the consumer, do not know enough about computers. This allows them to sell you computers that cost more ...

 A brief and concise picture of the developement and history of the Internet. Where it started, why it started and major milestones. Around the mid sixties, two computers located in different geographical areas within the US were connected using a 1200 bps phone line.
A brief and concise picture of the developement and history of the Internet. Where it started, why it started and major milestones. Around the mid sixties, two computers located in different geographical areas within the US were connected using a 1200 bps phone line. 
 As the title says, its the history behind several cyber services that we take for granted so easily these days. Ever wonder what the story behind the @ sign was, how and why the inventors of the the email used this symbol? Find out all this here along with other various things in our history lesson this week.
As the title says, its the history behind several cyber services that we take for granted so easily these days. Ever wonder what the story behind the @ sign was, how and why the inventors of the the email used this symbol? Find out all this here along with other various things in our history lesson this week.
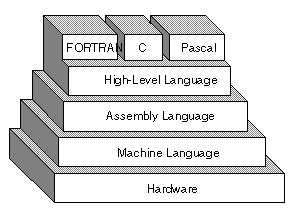 Programming languages date backalmost to the invention of the digital computer in the 1940s.
Programming languages date backalmost to the invention of the digital computer in the 1940s.
 Internetworking with TCP/IP has been around for many years-almost as many years as Unix has been available. TCP/IP, or Transmission Control Protocol/Internet Protocol, grew out of the work that was done with the Defense Advanced Research Projects Agency, or DARPA. In 1969, DARPA sponsored a project that became known as the ARPANET. This network mainly provided high-bandwidth connectivity between the major computing sites in government, educational, and research laboratories.
Internetworking with TCP/IP has been around for many years-almost as many years as Unix has been available. TCP/IP, or Transmission Control Protocol/Internet Protocol, grew out of the work that was done with the Defense Advanced Research Projects Agency, or DARPA. In 1969, DARPA sponsored a project that became known as the ARPANET. This network mainly provided high-bandwidth connectivity between the major computing sites in government, educational, and research laboratories.
 Origin of computers was a gradual development from the room size UNIVACS to the hand held palm tops today. This improvement was possible due to the discovery of many new technologies which reduced processing time, size and cost. Computer history is classified into generations based on the discovery which led to major change. The computers in these generations differ greatly from its previous and next ones.
Origin of computers was a gradual development from the room size UNIVACS to the hand held palm tops today. This improvement was possible due to the discovery of many new technologies which reduced processing time, size and cost. Computer history is classified into generations based on the discovery which led to major change. The computers in these generations differ greatly from its previous and next ones.
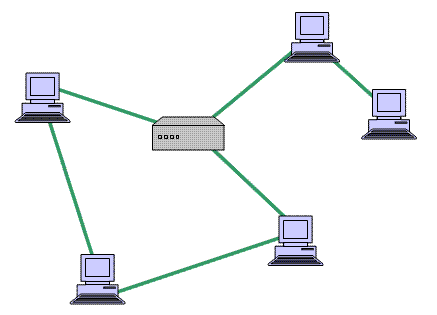 Mesh networking is a way of connecting a few devices between themselves. In that way there are many paths that lead to the destination device.In that way if one path clogs up there are many other paths that can be used to avoid slowness and problems. If there was only one path and there was a problem there would be slowness and many other problems, in this way you can avoid them almost completely.
Mesh networking is a way of connecting a few devices between themselves. In that way there are many paths that lead to the destination device.In that way if one path clogs up there are many other paths that can be used to avoid slowness and problems. If there was only one path and there was a problem there would be slowness and many other problems, in this way you can avoid them almost completely.
 Standard default values are usually used by routers for their Wi-Fi radio settings. The variations of of wireless protocols that will be supported by the router are managed by the Wi-Fi mode. What frequency band will be used by a wireless router for radio communication is determined by the Wi-Fi channel number. The usual Wi-Fi channel numbers in most countries are somewhere between 1 and 11.
Standard default values are usually used by routers for their Wi-Fi radio settings. The variations of of wireless protocols that will be supported by the router are managed by the Wi-Fi mode. What frequency band will be used by a wireless router for radio communication is determined by the Wi-Fi channel number. The usual Wi-Fi channel numbers in most countries are somewhere between 1 and 11.
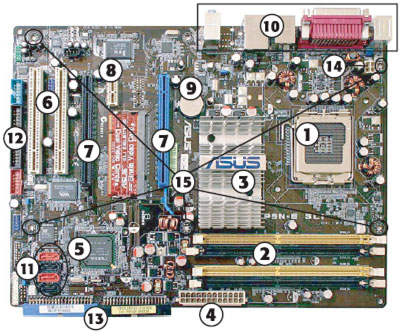 In the event of taking an existing computer in for repairs only to be told that a new motherboard is needed, it may sound like it is very expensive to buy. The good news is that motherboards come by very cheap compared to purchasing a new PC. Many online retailers specializing in computer parts sell motherboards for under $100 for a board that meets the requirements of building a high-end computer for a lot more, although there are boards that cost more for what a builder needs for the ultimate custom PC.
In the event of taking an existing computer in for repairs only to be told that a new motherboard is needed, it may sound like it is very expensive to buy. The good news is that motherboards come by very cheap compared to purchasing a new PC. Many online retailers specializing in computer parts sell motherboards for under $100 for a board that meets the requirements of building a high-end computer for a lot more, although there are boards that cost more for what a builder needs for the ultimate custom PC.
 I think we discussed wee bit more then what was expected of us on this one. You wont see "hacking" discussed more openly then this. It is all here people! Learn how others hack into computers and how you can prevent them from hacking into yours.
I think we discussed wee bit more then what was expected of us on this one. You wont see "hacking" discussed more openly then this. It is all here people! Learn how others hack into computers and how you can prevent them from hacking into yours.
 Ever wonder what'll happen when all the possible IP addresses will be taken? Remember when the phone companies ran out of 800 numbers? Well the same thing is about to happen with IP addresses and quickly. With IP V-6 every person on earth could have a million uniquely addressees and the individually locatable IP devices Read all about it here.
Ever wonder what'll happen when all the possible IP addresses will be taken? Remember when the phone companies ran out of 800 numbers? Well the same thing is about to happen with IP addresses and quickly. With IP V-6 every person on earth could have a million uniquely addressees and the individually locatable IP devices Read all about it here.


 To be a good programmer is difficult and noble. The hardest part of making real a collective vision of a software project is dealing with one's coworkers and customers. Writing computer programs is important and takes great intelligence and skill. But it is really child's play compared to everything else that a good programmer must do to make a software system that succeeds for both the customer and myriad colleagues for whom she is partially responsible. In this essay I attempt to summarize as concisely as possible those things that I wish someone had explained to me when I was twenty-one.
To be a good programmer is difficult and noble. The hardest part of making real a collective vision of a software project is dealing with one's coworkers and customers. Writing computer programs is important and takes great intelligence and skill. But it is really child's play compared to everything else that a good programmer must do to make a software system that succeeds for both the customer and myriad colleagues for whom she is partially responsible. In this essay I attempt to summarize as concisely as possible those things that I wish someone had explained to me when I was twenty-one.

 This article is all about the pros and cons of web hosting companies - including the scams and some tips on how to avoid them. After reading this article, you should be more equipped when the time comes for you to make the big decision.
This article is all about the pros and cons of web hosting companies - including the scams and some tips on how to avoid them. After reading this article, you should be more equipped when the time comes for you to make the big decision.
.png) In this guide we will show you how to get rid of unwanted "trash" that keeps piling up when you are using Microsoft Windows.
In this guide we will show you how to get rid of unwanted "trash" that keeps piling up when you are using Microsoft Windows. 
 Reviewing documents is a cumbersome task within itself, not to mention writing tiny notes in the margins and by the time you finished, you can hardly read what you have written. But what if there was a way to make comments in a Microsoft Word document right on the screen, would you use it?
Reviewing documents is a cumbersome task within itself, not to mention writing tiny notes in the margins and by the time you finished, you can hardly read what you have written. But what if there was a way to make comments in a Microsoft Word document right on the screen, would you use it?
Of course you would. Not only can you make comments on screen, but you can also track changes made to word documents. Now that your interest has been peaked, you want to learn how to use it?


 It is a great feeling to have state of the art home network. But the moment you leave the house, all of the network is out of reach. This is not always the case, if you know what you are doing of course. You can be thousands of miles away and still use your network to the full advantage.
It is a great feeling to have state of the art home network. But the moment you leave the house, all of the network is out of reach. This is not always the case, if you know what you are doing of course. You can be thousands of miles away and still use your network to the full advantage.
 Do you need to copy a heavy file from another laptop without using pen drive or connecting cables? Of course, this can be done by using electronic transfer methods like ftp or online data storage systems. However, these methods are not only time consuming, they often lead to increased data transfer costs. Moreover, what if there is no internet connectivity available in the immediate vicinity? Under such circumstances, you can connect two laptops through Bluetooth and exchange files seamlessly.
Do you need to copy a heavy file from another laptop without using pen drive or connecting cables? Of course, this can be done by using electronic transfer methods like ftp or online data storage systems. However, these methods are not only time consuming, they often lead to increased data transfer costs. Moreover, what if there is no internet connectivity available in the immediate vicinity? Under such circumstances, you can connect two laptops through Bluetooth and exchange files seamlessly.
 Learn how to display information that is stored n the database table in various ways with MySQL.
Learn how to display information that is stored n the database table in various ways with MySQL.

 Sometimes, we get stressed when everything happens all at once. When this happens, a person should take a deep breath and try to find something to do for a few minutes to get their mind off of the problem. A person could take a walk, listen to some music, read the newspaper or do an activity that will give them a fresh perspective on things.
Sometimes, we get stressed when everything happens all at once. When this happens, a person should take a deep breath and try to find something to do for a few minutes to get their mind off of the problem. A person could take a walk, listen to some music, read the newspaper or do an activity that will give them a fresh perspective on things.
 Defragmenting your hard drive is very important for a fast and secure computer. If you notice your computer working slowly, defragmenting is the first thing you should do. You need to know how to do this process safely and with that delay the buying of a new computer.
Defragmenting your hard drive is very important for a fast and secure computer. If you notice your computer working slowly, defragmenting is the first thing you should do. You need to know how to do this process safely and with that delay the buying of a new computer.
 YouTube is a video sharing website on which users can upload as well as share videos. Almost 200 million user's logon to the website daily to share and watch videos posted on YouTube. Registered user of the website can upload personal videos to this website and allow other users to view their videos online.
YouTube is a video sharing website on which users can upload as well as share videos. Almost 200 million user's logon to the website daily to share and watch videos posted on YouTube. Registered user of the website can upload personal videos to this website and allow other users to view their videos online.But do you know that you can also download videos from YouTube and watch them later without any internet connectivity. Earlier, all the videos on YouTube were in flash video format, which were of poor quality and were not compatible with other devices. However, visitors can now watch and share videos in different formats like high definition, mp4 and other popular format.

 ...the display settings were displayed... on the TV screen. Which I couldn't see. A nice little catch-22 there. Not to worry, there is a solution. For applications that do not show up in the taskbar. The desktop settings window does not show up in the taskbar, so you can't do it as described above. Here's what to do.
...the display settings were displayed... on the TV screen. Which I couldn't see. A nice little catch-22 there. Not to worry, there is a solution. For applications that do not show up in the taskbar. The desktop settings window does not show up in the taskbar, so you can't do it as described above. Here's what to do.

.jpg) It will probably happen that you have to connect into a wireless router in order to do some updates on the routers configuration. In order to gain access to the wireless router and it's configuration you need to be familiar with the IP address of the router and also you need to know the admin password and the username of the wireless router. It is not bad if you are knowledgeable in router problems and fixing those problems.
It will probably happen that you have to connect into a wireless router in order to do some updates on the routers configuration. In order to gain access to the wireless router and it's configuration you need to be familiar with the IP address of the router and also you need to know the admin password and the username of the wireless router. It is not bad if you are knowledgeable in router problems and fixing those problems.
 The thing that most people complain about when it comes to Microsoft's Surface tablet is that it has a lot less usable space on the disc than what is said in the advertisement. Microsoft announced in November exactly how much free space you can expect on the disc in the Surface tablet.
The thing that most people complain about when it comes to Microsoft's Surface tablet is that it has a lot less usable space on the disc than what is said in the advertisement. Microsoft announced in November exactly how much free space you can expect on the disc in the Surface tablet.
 When you connect to the Internet, your home computer (or network router) is assigned a public IP address. As you visit Web sites or other Internet servers, that public IP address is transmitted and recorded in log files kept on those servers. Access logs leave a trail of your Internet activity.
When you connect to the Internet, your home computer (or network router) is assigned a public IP address. As you visit Web sites or other Internet servers, that public IP address is transmitted and recorded in log files kept on those servers. Access logs leave a trail of your Internet activity. 
 First, contact your service provider and make sure they do their job properly and provide the service they should. Or maybe your package is obsolete and the company will upgrade it either for free or for a small fee.
First, contact your service provider and make sure they do their job properly and provide the service they should. Or maybe your package is obsolete and the company will upgrade it either for free or for a small fee.
 How could you enjoy your favorite music or the sound effects of movies and games without a quality sound card. In the following article you will find the description that is necessary to install a sound card. These instructions will be useful for most AMD and Intel computers that use the latest Windows operating systems.
How could you enjoy your favorite music or the sound effects of movies and games without a quality sound card. In the following article you will find the description that is necessary to install a sound card. These instructions will be useful for most AMD and Intel computers that use the latest Windows operating systems. 
 IDE (Integrated Development Environment) represents an integrated development environment in which you can develop applications. This tutorial will be useful to all those that considering doing programing...
IDE (Integrated Development Environment) represents an integrated development environment in which you can develop applications. This tutorial will be useful to all those that considering doing programing...
 WordPress is the most popular blogging platform and content managing system (CMS, Content Management System). It is an open source platform that offers a lot to adjust. WordPress is a free platform mostly used by blogger.
WordPress is the most popular blogging platform and content managing system (CMS, Content Management System). It is an open source platform that offers a lot to adjust. WordPress is a free platform mostly used by blogger.
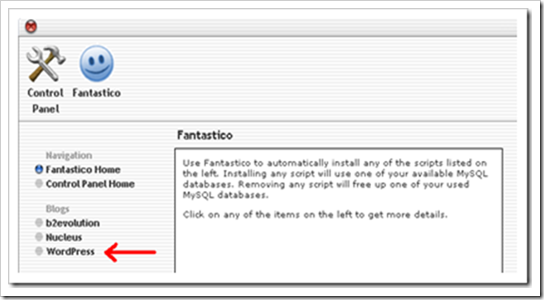 ...This page is called a WordPress Dashboard. Get to know this part because you will be using it a lot. That is the matrix of your Web page. All changes on your Web page will go through the Dashboard.
...This page is called a WordPress Dashboard. Get to know this part because you will be using it a lot. That is the matrix of your Web page. All changes on your Web page will go through the Dashboard.
 Microsoft Power Point is a powerful program that enables you to present information and your ideas in an interesting and effective way. In the following text you will find tips on how to make an interesting Power Point presentation and how to present it to the audience.
Microsoft Power Point is a powerful program that enables you to present information and your ideas in an interesting and effective way. In the following text you will find tips on how to make an interesting Power Point presentation and how to present it to the audience.
 There are situations when you have taken pictures, you wrote, downloaded, your secret passwords etc. should not be available to anyone that use or see your computer. Whether it is kids, parents or someone that will temporarily work on your computer, you have the right for privacy and there are ways to protect your content.
There are situations when you have taken pictures, you wrote, downloaded, your secret passwords etc. should not be available to anyone that use or see your computer. Whether it is kids, parents or someone that will temporarily work on your computer, you have the right for privacy and there are ways to protect your content.
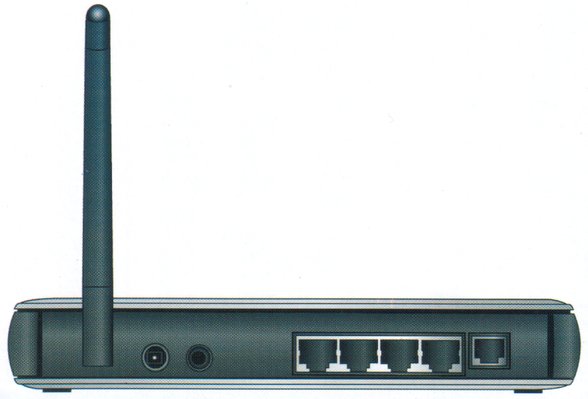 You should always change your routers default password. That is a must. It is because the generic router passwords can be found all over the Internet. This information can be found by hackers and they could use it to break into your router and cause you a lot of problems.
You should always change your routers default password. That is a must. It is because the generic router passwords can be found all over the Internet. This information can be found by hackers and they could use it to break into your router and cause you a lot of problems.


 How many times have we come across TW visitor saying "How do I recover files" or "I deleted files from the recycling bin...how do I restore deleted files?"
How many times have we come across TW visitor saying "How do I recover files" or "I deleted files from the recycling bin...how do I restore deleted files?"
Well, don't worry and be happy that you came across this little article on TechiWarehouse.Com.
You can often successfully recover deleted files from a PC, it all depends on what has happened since the files were deleted.

 It has probably happened to you that you accidentally delete some file, and then in a hurry tried to get it back but you again, by accident, clicked on empty recycle bin and lost that file forever. Imagine that there is a solution for this. Of course there is one, and with the help of the program Recuva.
It has probably happened to you that you accidentally delete some file, and then in a hurry tried to get it back but you again, by accident, clicked on empty recycle bin and lost that file forever. Imagine that there is a solution for this. Of course there is one, and with the help of the program Recuva.
 Portable Document Format or PDF is a popular document created by Adobe, which can hold text, fonts, images and graphics. This particular kind of document has been immensely successful die to its portability and platform independence. Even if the images and graphics used in PDF are heavy, the actual size of document is very small, hence, facilitates easy transfer through various methods.
Portable Document Format or PDF is a popular document created by Adobe, which can hold text, fonts, images and graphics. This particular kind of document has been immensely successful die to its portability and platform independence. Even if the images and graphics used in PDF are heavy, the actual size of document is very small, hence, facilitates easy transfer through various methods.
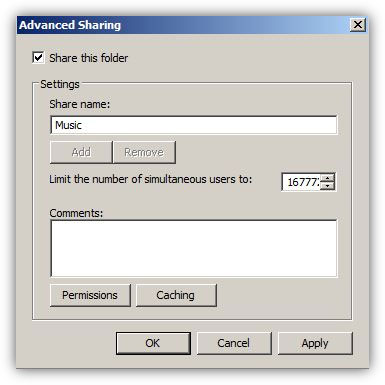 In organizations or home setups where there are multiple computers connected to each other, in order to transfer files from one computer to another administrators use to share the folders on one computer (generally known as file server) and make them accessible from all other computers in the network. In order to do so administrators normally configure and set NTFS and share permissions on the shared folders which, as a result, help them control the accessibility of user accounts or groups on them.
In organizations or home setups where there are multiple computers connected to each other, in order to transfer files from one computer to another administrators use to share the folders on one computer (generally known as file server) and make them accessible from all other computers in the network. In order to do so administrators normally configure and set NTFS and share permissions on the shared folders which, as a result, help them control the accessibility of user accounts or groups on them.

 The words "free" and "app" can often bring to the fore the greedy kid inside the individuals from the tech savvy brigade - people like yourself for example. Even so, when the aforementioned pair of words combines you just can't help hankering after this technological treat - of course much to the detriment of your smart phone in numerous cases. Mobile phone spy software can ensure that your cell phone goes kaput and hence it is extremely important that you steer clear of the spyware for your Android phone. Here's how you can do it...
The words "free" and "app" can often bring to the fore the greedy kid inside the individuals from the tech savvy brigade - people like yourself for example. Even so, when the aforementioned pair of words combines you just can't help hankering after this technological treat - of course much to the detriment of your smart phone in numerous cases. Mobile phone spy software can ensure that your cell phone goes kaput and hence it is extremely important that you steer clear of the spyware for your Android phone. Here's how you can do it...
 Today we are going to present you two tutorials in Excel. We are going to talk about tracking changes and number formatting in Excel.
Today we are going to present you two tutorials in Excel. We are going to talk about tracking changes and number formatting in Excel. 
 Using the reset a password disc is the right solution if you have prepared before, but what happens if you didn't take the needed steps before you have lost your password? If this is truly the case, you have to use a special program that will enable unlocking your operating system. The best free option is Ophcrack, a program that guesses the code by using a special program called "the rainbow table".
Using the reset a password disc is the right solution if you have prepared before, but what happens if you didn't take the needed steps before you have lost your password? If this is truly the case, you have to use a special program that will enable unlocking your operating system. The best free option is Ophcrack, a program that guesses the code by using a special program called "the rainbow table".
 Has your computer started working sloppy or slowly? Did you get to the conclusion that it is necessary to upgrade your RAM memory? Don't be afraid, for the process of upgrading your RAM memory you won't need any special equipment or any special training. It is just necessary to know what is inside of your computer.
Has your computer started working sloppy or slowly? Did you get to the conclusion that it is necessary to upgrade your RAM memory? Don't be afraid, for the process of upgrading your RAM memory you won't need any special equipment or any special training. It is just necessary to know what is inside of your computer.
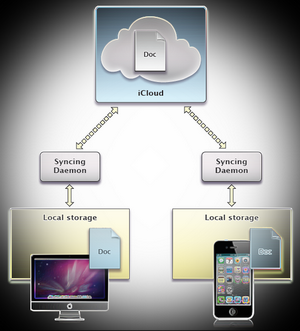 If you are using Android, BlackBerry or Apple phone you can print whatever you want, no matter where you are. It is necessary to have an installed Cloud print app on your phone and to have a Gmail account. The application itself has the possibility of printing all files, pictures, drawings, SMS, contacts, scanned documents, notes, attachments that you got by Gmail, calendars, Facebook, various storage you use on Google Drive, Dropbox, etc. More precisely, every document stored in your phone.
If you are using Android, BlackBerry or Apple phone you can print whatever you want, no matter where you are. It is necessary to have an installed Cloud print app on your phone and to have a Gmail account. The application itself has the possibility of printing all files, pictures, drawings, SMS, contacts, scanned documents, notes, attachments that you got by Gmail, calendars, Facebook, various storage you use on Google Drive, Dropbox, etc. More precisely, every document stored in your phone.
 Overclocking your graphic card is a popular way to get some more speed out of it, and it exists for a long time. Till now, the approach to this problem was almost identical no matter what the manufacturer, category or model it was. With the new NVIDIA graphic processor things are a bit more complicated, because new technology is being introduced that is called Dynamic Overclocking.
Overclocking your graphic card is a popular way to get some more speed out of it, and it exists for a long time. Till now, the approach to this problem was almost identical no matter what the manufacturer, category or model it was. With the new NVIDIA graphic processor things are a bit more complicated, because new technology is being introduced that is called Dynamic Overclocking. 
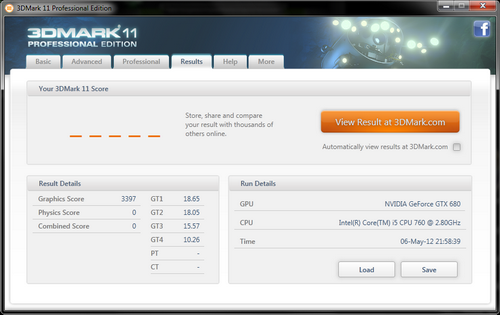 The first step is to go to the settings and unlocking the possibility of changing voltage if you want to get the maximum values. After that we will look what the maximum frequency for the GPU is at unchanged values for the voltage and the rpm of the fan. We will leave the memory for the end, because the principle of its overclocking is the same for every other graphic card, because dynamic overclocking doesn't apply for it.
The first step is to go to the settings and unlocking the possibility of changing voltage if you want to get the maximum values. After that we will look what the maximum frequency for the GPU is at unchanged values for the voltage and the rpm of the fan. We will leave the memory for the end, because the principle of its overclocking is the same for every other graphic card, because dynamic overclocking doesn't apply for it.
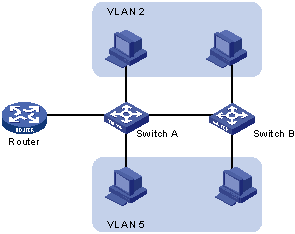 A VLAN is a grouping of computers that is logically segmented by functions, project teams, or applications without regard to the physical location of users. Similar to routers, VLANs offer an effective mechanism for setting up firewalls in a switch fabric, protecting the network against broadcast problems that are potentially dangerous, and maintaining all the performance benefits of switching. You can create these firewalls by assigning switch ports or users to specific VLAN groups in single switches and across multiple connected switches, which will increase security easily and inexpensively by segmenting the network.
A VLAN is a grouping of computers that is logically segmented by functions, project teams, or applications without regard to the physical location of users. Similar to routers, VLANs offer an effective mechanism for setting up firewalls in a switch fabric, protecting the network against broadcast problems that are potentially dangerous, and maintaining all the performance benefits of switching. You can create these firewalls by assigning switch ports or users to specific VLAN groups in single switches and across multiple connected switches, which will increase security easily and inexpensively by segmenting the network. 
 The company Android was created by four enthusiasts from California, a long time before the name appeared in public. It was in October 2003. And their goal was to develop "smarter mobile phones that take care of the users demands more". The development flowed silently without a lot of talking to the public. As it usually happens, when enthusiast develop something big without the help of sponsors, the financing didn't go smoothly.
The company Android was created by four enthusiasts from California, a long time before the name appeared in public. It was in October 2003. And their goal was to develop "smarter mobile phones that take care of the users demands more". The development flowed silently without a lot of talking to the public. As it usually happens, when enthusiast develop something big without the help of sponsors, the financing didn't go smoothly.
 Check out the new breed of Web Applications and how they interact on the web. Used primarily as a means for businesses to communicate with each other and with clients, Web services allow organizations to communicate data without intimate knowledge of each other's IT systems behind the firewall.
Check out the new breed of Web Applications and how they interact on the web. Used primarily as a means for businesses to communicate with each other and with clients, Web services allow organizations to communicate data without intimate knowledge of each other's IT systems behind the firewall.
 You've got a great website but now what? Ever wonder how the masses will get to your site? Your site is great, maybe even better than great but your site is competing with MILLIONS of other similar sites. TW suggests you learn the nitty gritty of search engines and use it to your advantage from this article.
You've got a great website but now what? Ever wonder how the masses will get to your site? Your site is great, maybe even better than great but your site is competing with MILLIONS of other similar sites. TW suggests you learn the nitty gritty of search engines and use it to your advantage from this article.
 Although the computer is mostly firm, the upper part of the screen bends a little bit under pressure. The 13 inch screen is pretty controversial: the picture is just fine when you are straight in front of the screen, but if you move to the left or to the right the picture becomes blurry. If you even more, it is very difficult to use. The screen has standard resolution, and it is handled by a graphic core HD 4000 processor Ivy Bridge which means that Spectre will handle moderate intensity games.
Although the computer is mostly firm, the upper part of the screen bends a little bit under pressure. The 13 inch screen is pretty controversial: the picture is just fine when you are straight in front of the screen, but if you move to the left or to the right the picture becomes blurry. If you even more, it is very difficult to use. The screen has standard resolution, and it is handled by a graphic core HD 4000 processor Ivy Bridge which means that Spectre will handle moderate intensity games.
 Envy x2 is based on the Intel Atom Z2760 processor for minimal consumption. Two cores enable it decent performances, comparable to competitor tablets and enough for your everyday activities, but compared to classic portables this model is not a speed champion and is not suitable with demanding processor tasks and playing complicated games.
Envy x2 is based on the Intel Atom Z2760 processor for minimal consumption. Two cores enable it decent performances, comparable to competitor tablets and enough for your everyday activities, but compared to classic portables this model is not a speed champion and is not suitable with demanding processor tasks and playing complicated games.
 The speed of printing is modest, only 5.5 pages a minute in standard quality, but that is a price that is needed to be paid for a long battery life and relatively small dimensions. The quality of printing is in rank with full blooded HP printers so the quality of the printed text is usable even in the worst draft mode. The input tray takes 50 leafs of paper, and an unpleasant surprise is that there is no output tray,
The speed of printing is modest, only 5.5 pages a minute in standard quality, but that is a price that is needed to be paid for a long battery life and relatively small dimensions. The quality of printing is in rank with full blooded HP printers so the quality of the printed text is usable even in the worst draft mode. The input tray takes 50 leafs of paper, and an unpleasant surprise is that there is no output tray,
 Multifunction devices are the most popular choice when buying a device to work with documents. When it comes to home users and small offices, the advantage of devices that combine a printer and scanner (and make a photocopier) comes down to the fact that they take up less space on your desk.
Multifunction devices are the most popular choice when buying a device to work with documents. When it comes to home users and small offices, the advantage of devices that combine a printer and scanner (and make a photocopier) comes down to the fact that they take up less space on your desk.
 HTML5 is the latest buzz word in web development world. It comes with a lot of cool, new features and most importantly it aims at bringing consistency to the whole process of web development. The code is much cleaner, neater and standardized. For example, web software developers can replace the div tags with neat HTML5 elements. This also means that web developers across the board can read and understand code better even if they know nothing about the language because of the standardization. This also ensures that web developers building new hosted web applications can understand the features better and integrate well with it. The overall semantics would improve because of the new HTML elements and it would be easy to see the structure of the code and determine the header, footer, navigators etc.
HTML5 is the latest buzz word in web development world. It comes with a lot of cool, new features and most importantly it aims at bringing consistency to the whole process of web development. The code is much cleaner, neater and standardized. For example, web software developers can replace the div tags with neat HTML5 elements. This also means that web developers across the board can read and understand code better even if they know nothing about the language because of the standardization. This also ensures that web developers building new hosted web applications can understand the features better and integrate well with it. The overall semantics would improve because of the new HTML elements and it would be easy to see the structure of the code and determine the header, footer, navigators etc.
 Programmers of Web apps like Kevin Sweeney, that works on a famous video sharing site called Vimeo with its headquarters in New York, already accepted these new tools that have been built in HTML5. "We were forced to rely on external add-ons like Adobe Flash or Quick Time, that we had to build in on our web pages. The thing that will be accomplished by the use of HTML5 is their removal from the code so that these things are directly supported", says he.
Programmers of Web apps like Kevin Sweeney, that works on a famous video sharing site called Vimeo with its headquarters in New York, already accepted these new tools that have been built in HTML5. "We were forced to rely on external add-ons like Adobe Flash or Quick Time, that we had to build in on our web pages. The thing that will be accomplished by the use of HTML5 is their removal from the code so that these things are directly supported", says he.
 HTML5 is partially responsible for the war between search engines in the last few years. A decade before Chrome, Firefox and Safari they didn't exist while the updating and improving of Internet Explorer was rare. Today desktop and mobile search engines are updated very often following the appearance of the new HTML5 functions.
HTML5 is partially responsible for the war between search engines in the last few years. A decade before Chrome, Firefox and Safari they didn't exist while the updating and improving of Internet Explorer was rare. Today desktop and mobile search engines are updated very often following the appearance of the new HTML5 functions.
 This is easy as heck CSS tutorial for the beginners. It will show you how you can add your own color customized scroll bar for your own site. Don't forget: If using CSS rules within the open and close
This is easy as heck CSS tutorial for the beginners. It will show you how you can add your own color customized scroll bar for your own site. Don't forget: If using CSS rules within the open and close
 Today, I was browsing through some free font sites when decided to take a break. Upon my return, I saw what at once seemed like a computer virus protection software alerting me of a possible infection. However, I could tell this was fake because I never installed that antivirus software. I've always relied on AVG and Avira as my primier free antivirus firewall software.
Today, I was browsing through some free font sites when decided to take a break. Upon my return, I saw what at once seemed like a computer virus protection software alerting me of a possible infection. However, I could tell this was fake because I never installed that antivirus software. I've always relied on AVG and Avira as my primier free antivirus firewall software.
 A very brief overview on Internet Explorer 6. Microsoft has designed Internet Explorer to make it easier for you to get the most from the World Wide Web. If you browse sites in other languages, IE can update your computer with the character sets needed to view these sites correctly.
A very brief overview on Internet Explorer 6. Microsoft has designed Internet Explorer to make it easier for you to get the most from the World Wide Web. If you browse sites in other languages, IE can update your computer with the character sets needed to view these sites correctly.
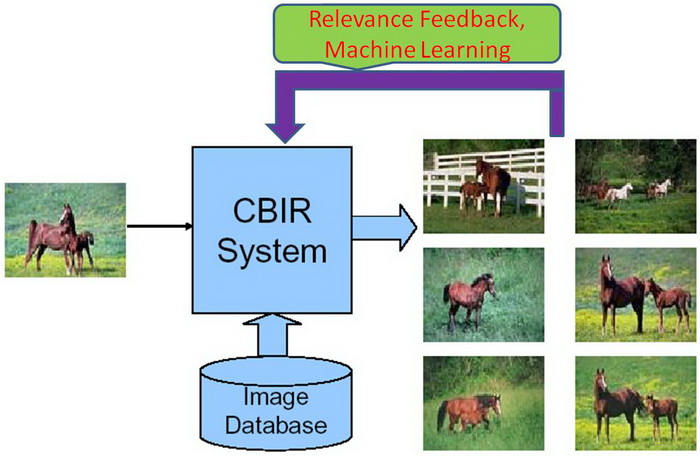 Over the last 10 years Content based image retrieval (CBIR) or Content-based visual information retrieval (CBVIR) has been one on the most researched areas in the field of computer vision. The availability of large and steadily growing amounts of multimedia and visual data, and the development of the Internet create the need to make thematic approach methods that offer more than simple text-based queries or requests based on matching exact database fields.
Over the last 10 years Content based image retrieval (CBIR) or Content-based visual information retrieval (CBVIR) has been one on the most researched areas in the field of computer vision. The availability of large and steadily growing amounts of multimedia and visual data, and the development of the Internet create the need to make thematic approach methods that offer more than simple text-based queries or requests based on matching exact database fields.
 Because Web Development societie is advancing rapidly, it is clear that some types of media are at an advantage over others. Individuals have never had the chance to in such a powerful way influence public opinion. There are many questions that arise in front of us when we think about the impact of the Web and on society in general.
Because Web Development societie is advancing rapidly, it is clear that some types of media are at an advantage over others. Individuals have never had the chance to in such a powerful way influence public opinion. There are many questions that arise in front of us when we think about the impact of the Web and on society in general.
 It used to be that businesses had a major influence on what types of products and services were available to the general public. In the early days of the Internet, networking LAN technologies and needs were the driving force behind the creation of many software applications and tools that users accessed. The growing popularity of the World Wide Web with casual computer users led to a paradigm shift in how to approach usable software solutions for these users. Simple to install and use software applications such as file sharing, e-mail and instant chat programs were instantly popular.
It used to be that businesses had a major influence on what types of products and services were available to the general public. In the early days of the Internet, networking LAN technologies and needs were the driving force behind the creation of many software applications and tools that users accessed. The growing popularity of the World Wide Web with casual computer users led to a paradigm shift in how to approach usable software solutions for these users. Simple to install and use software applications such as file sharing, e-mail and instant chat programs were instantly popular.
 TCP is a common transport protocol that is used in almost all the internet applications. The main problem with the TCP is that TCP falsely assume the packet loss as congestion. The TCP sender detects a packet loss when a time out happens or duplicate acknowledgements happen.
TCP is a common transport protocol that is used in almost all the internet applications. The main problem with the TCP is that TCP falsely assume the packet loss as congestion. The TCP sender detects a packet loss when a time out happens or duplicate acknowledgements happen. 
 It seems to us today that our survival depends on it! Thank God, it is not like that, but information technology is applied in all spheres of life. There are many advantages - the systematic storage of information to an unlimited number of copies and not decaying in a physical sense.In practical terms, availability and cost of intangible form is reduced to almost zero, and the environment is 100% safe.
It seems to us today that our survival depends on it! Thank God, it is not like that, but information technology is applied in all spheres of life. There are many advantages - the systematic storage of information to an unlimited number of copies and not decaying in a physical sense.In practical terms, availability and cost of intangible form is reduced to almost zero, and the environment is 100% safe. 
 Information from a research that the research company IDC conducted for the Business Software Alliance (BSA) show that 36% of bought software in 2006. is pirate software. In a research IDC has analyzed the use of software in a 102 different countries across the world and it is estimated that the software that was installed on all computers in these countries was worth 105 billion dollars, and that the sale of legal software has risen for about 9 percent.
Information from a research that the research company IDC conducted for the Business Software Alliance (BSA) show that 36% of bought software in 2006. is pirate software. In a research IDC has analyzed the use of software in a 102 different countries across the world and it is estimated that the software that was installed on all computers in these countries was worth 105 billion dollars, and that the sale of legal software has risen for about 9 percent.
 Information technology is mostly referred to as consisting out of three main parts. Those three parts are decision support, business software and computational data processing. Those three terms were first mention in a Harvard article. That article is usually considered to be the birthplace of modern IT. They were working on the go and by doing so set the foundation for modern information technology. Modern IT involves computer tech support, business software development, information security, business computer network and database administration jobs.
Information technology is mostly referred to as consisting out of three main parts. Those three parts are decision support, business software and computational data processing. Those three terms were first mention in a Harvard article. That article is usually considered to be the birthplace of modern IT. They were working on the go and by doing so set the foundation for modern information technology. Modern IT involves computer tech support, business software development, information security, business computer network and database administration jobs.
 Ever wonder why CNN keeps talking about technology when it comes to recent news of terrorism? Well thats because our biggest resource is "information" and its "specific distribution". Read all about what our threats, weaknesses, and how we are preparing for countering these threats.
Ever wonder why CNN keeps talking about technology when it comes to recent news of terrorism? Well thats because our biggest resource is "information" and its "specific distribution". Read all about what our threats, weaknesses, and how we are preparing for countering these threats.
 Ever wanted to run your own home web server? Now you can! This article will give you the lowdown on Microsoft web servers and third party web servers for use on Windows operating systems.
Ever wanted to run your own home web server? Now you can! This article will give you the lowdown on Microsoft web servers and third party web servers for use on Windows operating systems.

 This is not a very difficult task, but it is not a very easy one. It should probably take you somewhere around 5 minutes, but you have to have the knowledge needed to do this. If you want to acquire that knowledge, read this text about installing the Client for Microsoft Networks.
This is not a very difficult task, but it is not a very easy one. It should probably take you somewhere around 5 minutes, but you have to have the knowledge needed to do this. If you want to acquire that knowledge, read this text about installing the Client for Microsoft Networks.
 IM really began to take off in the mid-90s with AOLs Instant Messenger. Soon other IM systems began to proliferate, including Yahoo Messenger, ICQ and MSN Messenger. All of these had buddy lists which could be used to add contacts, and presence which enabled you to see which of your contacts were online, available, busy, etc. The problem was that none of these applications could interoperate, so an end user had to install several IM clients in order to talk to friends using different systems.
IM really began to take off in the mid-90s with AOLs Instant Messenger. Soon other IM systems began to proliferate, including Yahoo Messenger, ICQ and MSN Messenger. All of these had buddy lists which could be used to add contacts, and presence which enabled you to see which of your contacts were online, available, busy, etc. The problem was that none of these applications could interoperate, so an end user had to install several IM clients in order to talk to friends using different systems.
 The representatives of the Intel company have held a press conference to present a plan to introduce new possibilities on a large number of mobile devices such as Smart phones, Tablets and Ultrabook devices. Intel has introduced a new platform of low consumption based the Atom processors (code name Lexington) and a referent design that could reach a number of 500 million sales till 2015. The partners that will support this platform are Acer, Lava International and Safaricom.
The representatives of the Intel company have held a press conference to present a plan to introduce new possibilities on a large number of mobile devices such as Smart phones, Tablets and Ultrabook devices. Intel has introduced a new platform of low consumption based the Atom processors (code name Lexington) and a referent design that could reach a number of 500 million sales till 2015. The partners that will support this platform are Acer, Lava International and Safaricom.
 The new dual-core Atom SoC (Clover Trail+) platform has been announced, as well as the new LTE solution and the "Bay Trail" technology, the efforts that this company puts in presenting mobile devices and Smartphones on the market in the development with the help of the platform based on the Intel Atom Z2420 processor. The new Intel Atom platform (Clover Trail+) brings the leading performances in high economy and a great battery autonomy.
The new dual-core Atom SoC (Clover Trail+) platform has been announced, as well as the new LTE solution and the "Bay Trail" technology, the efforts that this company puts in presenting mobile devices and Smartphones on the market in the development with the help of the platform based on the Intel Atom Z2420 processor. The new Intel Atom platform (Clover Trail+) brings the leading performances in high economy and a great battery autonomy.
.jpg) The oceans account for over two thirds of our planet. They were the cradle of life, and now play a crucial role in its preservation. The Ocean Project has over the past twenty years grown from a handful of aquariums, zoos and museums in North America, to a global organization that today has more than 1,700 institutions worldwide. The primary task of Ocean project is to preserve and popularize maritime lifestyle. The official Web site of the organization has the current news of this year's celebration of the 8th June, World day of Oceans.
The oceans account for over two thirds of our planet. They were the cradle of life, and now play a crucial role in its preservation. The Ocean Project has over the past twenty years grown from a handful of aquariums, zoos and museums in North America, to a global organization that today has more than 1,700 institutions worldwide. The primary task of Ocean project is to preserve and popularize maritime lifestyle. The official Web site of the organization has the current news of this year's celebration of the 8th June, World day of Oceans.
 The official website for the most popular operating system based on Linux has recently gone through extensive changes and improvements. This page now has fewer major categories, subsections are organized much clearer, and the search window is constantly available. Images and text are now adapted for mobile devices. With clear instructions and explanations of the characteristics of this OS you have the option to consult the community and the development team. For users who want to test Ubuntu there is no better destination on the web.
The official website for the most popular operating system based on Linux has recently gone through extensive changes and improvements. This page now has fewer major categories, subsections are organized much clearer, and the search window is constantly available. Images and text are now adapted for mobile devices. With clear instructions and explanations of the characteristics of this OS you have the option to consult the community and the development team. For users who want to test Ubuntu there is no better destination on the web.
 A simple example using MySQL in conjunction with PHP for generating an interactive web site. PHP is an exciting addition to HTML that is allowing web designers to create new pages on the Internet that have dynamic content. In other words, each time a page is accessed, the data on that page might contain different information than the last time it was viewed.
A simple example using MySQL in conjunction with PHP for generating an interactive web site. PHP is an exciting addition to HTML that is allowing web designers to create new pages on the Internet that have dynamic content. In other words, each time a page is accessed, the data on that page might contain different information than the last time it was viewed.
 You know you are addicted to internet if ...You kiss your girlfriend's home page...or...
You know you are addicted to internet if ...You kiss your girlfriend's home page...or...
 This is something that can come in handy for those of you who are simply curious about internet backbone speeds.
This is something that can come in handy for those of you who are simply curious about internet backbone speeds.
 From sending an instant message to a friend, to e-mailing co-workers, to placing phone calls, to conducting video conferences, the Internet offers a number of ways to communicate. One of the fastest-growing forms of Internet communications is instant messaging, or IM. An IM communications service enables you to create a kind of private chat room with another individual in order to communicate in real-time over the Internet.
From sending an instant message to a friend, to e-mailing co-workers, to placing phone calls, to conducting video conferences, the Internet offers a number of ways to communicate. One of the fastest-growing forms of Internet communications is instant messaging, or IM. An IM communications service enables you to create a kind of private chat room with another individual in order to communicate in real-time over the Internet.

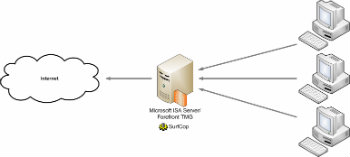 This weeks article discusses the nitty gritties of Server and Network Security and how to implement them. ISA Server uses Cache Array Routing Protocol (CARP) to enable a Web proxy array of virtually unlimited size for high availability and accelerated Web access. Internet Security and Acceleration (ISA) Server was built to enable companies to customize and extend their security and management features for optimum security and network performance by using a wide range of third-party solutions.
This weeks article discusses the nitty gritties of Server and Network Security and how to implement them. ISA Server uses Cache Array Routing Protocol (CARP) to enable a Web proxy array of virtually unlimited size for high availability and accelerated Web access. Internet Security and Acceleration (ISA) Server was built to enable companies to customize and extend their security and management features for optimum security and network performance by using a wide range of third-party solutions.
 The successor to Office 2000 includes hundreds of new features for users and support staff alike. But installation is unlikely to be straightforward. In some ways, Office XP is a revolutionary step, yet in other ways it can be seen more as a gentle evolution. On the revolution side of the equation, Microsoft is billing Office XP as the start of the .NET revolution
The successor to Office 2000 includes hundreds of new features for users and support staff alike. But installation is unlikely to be straightforward. In some ways, Office XP is a revolutionary step, yet in other ways it can be seen more as a gentle evolution. On the revolution side of the equation, Microsoft is billing Office XP as the start of the .NET revolution

 HTML (Hyper Text Markup Language) is a basic language that is used for defining web pages and consists of elements (marked with tags) and the content. HTML is not a program language. HTML documents are accessed using browsers like Mozilla Firefox, Google Chrome, Safari etc. For creating HTML documents you can use any text editor like for example Notepad, but it's recommended a more advanced program (Notepad++, Dreamweaver, NetBeans, Coda, etc.)
HTML (Hyper Text Markup Language) is a basic language that is used for defining web pages and consists of elements (marked with tags) and the content. HTML is not a program language. HTML documents are accessed using browsers like Mozilla Firefox, Google Chrome, Safari etc. For creating HTML documents you can use any text editor like for example Notepad, but it's recommended a more advanced program (Notepad++, Dreamweaver, NetBeans, Coda, etc.)
.jpg) Yesterday we brought you the first part of the free tutorial "Introduction to HTML", and you can read it here. Today you have a chance to read the final part of this free HTML introduction tutorial. Tables have been used before to make the structure of the page, which is outdated and is not valid by HTML standards, but tables are still used for the tabular display of a text.
Yesterday we brought you the first part of the free tutorial "Introduction to HTML", and you can read it here. Today you have a chance to read the final part of this free HTML introduction tutorial. Tables have been used before to make the structure of the page, which is outdated and is not valid by HTML standards, but tables are still used for the tabular display of a text.
 This tutorial will go through many aspects of the track view in 3D Studio MAX. The track view is often a mysterious and confusing element to "tweaking" many animation settings in 3dsmax. Well, I may be exaggerating a bit about the mysterious part, but the confusing part is true if you are unfamiliar with what the track view is all about.
This tutorial will go through many aspects of the track view in 3D Studio MAX. The track view is often a mysterious and confusing element to "tweaking" many animation settings in 3dsmax. Well, I may be exaggerating a bit about the mysterious part, but the confusing part is true if you are unfamiliar with what the track view is all about. 
 IP address conflicts are a pretty serious thing. They happen when there are two computers that are using the same IP address. If this happens, the computers can work offline only, the Internet is out of reach. There are many ways this can happen and here are some of them.
IP address conflicts are a pretty serious thing. They happen when there are two computers that are using the same IP address. If this happens, the computers can work offline only, the Internet is out of reach. There are many ways this can happen and here are some of them.
 Sniffing and spoofing are security threats that target the lower layers of the networking infrastructure supporting applications that use the Internet. Users do not interact directly with these lower layers and are typically completely unaware that they exist. Without a deliberate consideration of these threats, it is impossible to build effective security into the higher levels. Sniffing is a passive security attack in which a machine separate from the intended destination reads data on a network. The term "sniffing" comes from the notion of "sniffing the ether" in an Ethernet network and is a bad pun on the two meanings of the word "ether." Passive security attack are those that do not alter the normal flow of data on a communication link or inject data into the link.
Sniffing and spoofing are security threats that target the lower layers of the networking infrastructure supporting applications that use the Internet. Users do not interact directly with these lower layers and are typically completely unaware that they exist. Without a deliberate consideration of these threats, it is impossible to build effective security into the higher levels. Sniffing is a passive security attack in which a machine separate from the intended destination reads data on a network. The term "sniffing" comes from the notion of "sniffing the ether" in an Ethernet network and is a bad pun on the two meanings of the word "ether." Passive security attack are those that do not alter the normal flow of data on a communication link or inject data into the link.
 The new 3G Apple iPhone was released recently, to an audience who were pretty much on the edge of their seats with anticipation. The reviews have been largely favourable, with many bordering on zealous, such as the review by Alex Iskold on Read Write Web. In the review, which really isn't all that long, Iskold manages to tell us seven times that the iPhone is the new personal computer. In fact, according to Iskold, the new iPhone is the world's first really personal computer, and he seems pretty excited about that.
The new 3G Apple iPhone was released recently, to an audience who were pretty much on the edge of their seats with anticipation. The reviews have been largely favourable, with many bordering on zealous, such as the review by Alex Iskold on Read Write Web. In the review, which really isn't all that long, Iskold manages to tell us seven times that the iPhone is the new personal computer. In fact, according to Iskold, the new iPhone is the world's first really personal computer, and he seems pretty excited about that.
 We have all heard about someone shopping over the Internet more or less successfully and we can just vaguely remember how it all works. This text will break some dilemmas and enlighten Internet shopping.
We have all heard about someone shopping over the Internet more or less successfully and we can just vaguely remember how it all works. This text will break some dilemmas and enlighten Internet shopping.

 Step into the realm of IT Certifications. Where millions have entered and zillions have flunked. Ah, that didnt sound right, mathematically speaking that is. Anyway, if your one of the few breeds that like to get your hands on a certification and get ahead in your work place, it is strongly recommended that you read this article. Its not made with grueling details and gets right down to the point. So check it out, you probably owe it to yourself by now!
Step into the realm of IT Certifications. Where millions have entered and zillions have flunked. Ah, that didnt sound right, mathematically speaking that is. Anyway, if your one of the few breeds that like to get your hands on a certification and get ahead in your work place, it is strongly recommended that you read this article. Its not made with grueling details and gets right down to the point. So check it out, you probably owe it to yourself by now!
 Perhaps it is time for a career change, or you are fresh out of high school and the idea of four more years of schooling does not appeal to you. After much research you have decided to embark upon a career in the Information Technology field. Not a bad choice, especially since Technology changes every day.
You are faced with the choice of education. As previously stated, going to computer school for four years to get a computer science degree is not an option but there is another option, IT Boot Camp. And IT Boot Camps solely focus on a very limited number of IT Certifications. So there can be MCSE Boot Camps that may focus on just that.
Perhaps it is time for a career change, or you are fresh out of high school and the idea of four more years of schooling does not appeal to you. After much research you have decided to embark upon a career in the Information Technology field. Not a bad choice, especially since Technology changes every day.
You are faced with the choice of education. As previously stated, going to computer school for four years to get a computer science degree is not an option but there is another option, IT Boot Camp. And IT Boot Camps solely focus on a very limited number of IT Certifications. So there can be MCSE Boot Camps that may focus on just that.
 In this article, we would like to point out the obvious IT Jobs that at times get overlooked. Find out what's out there and which information technology is the right choice for you. From people that create laptop computers to folks that do web design to developers that come up with computer software concepts from scratch. Also a bit at the end about computer schools and computer training.
In this article, we would like to point out the obvious IT Jobs that at times get overlooked. Find out what's out there and which information technology is the right choice for you. From people that create laptop computers to folks that do web design to developers that come up with computer software concepts from scratch. Also a bit at the end about computer schools and computer training.
 Knowledge from the area of programing is on the first place on a list of the most wanted IT skills in 2013. A pole that was made for the American market by Computerworld shows that from the 334 directors from the IT sector as high as 60% of them plan to hire candidates that have these skills. On the second place of wanted knowledge is the capability to manage information technology projects , and IT directors announce that they will hire about 40% of workers from this area.
Knowledge from the area of programing is on the first place on a list of the most wanted IT skills in 2013. A pole that was made for the American market by Computerworld shows that from the 334 directors from the IT sector as high as 60% of them plan to hire candidates that have these skills. On the second place of wanted knowledge is the capability to manage information technology projects , and IT directors announce that they will hire about 40% of workers from this area. 
 You think you got what it takes to learn the fine craft of Java? Well think no more! Find out first hand by evaluating this easy to read Java Tutorial. It is meant to be for the new comers to the world or Java. And I don't mean the coffee neither. The importance of object-oriented programming is that it enables programmers to organize their programs in ways that resemble the organization of objects in the real world, which makes programming easier and more logical. Using object- oriented programming, the overall programs are made up of many different components (called "objects"), each of which has a specific role in a program and can talk to the other components in predefined ways.
You think you got what it takes to learn the fine craft of Java? Well think no more! Find out first hand by evaluating this easy to read Java Tutorial. It is meant to be for the new comers to the world or Java. And I don't mean the coffee neither. The importance of object-oriented programming is that it enables programmers to organize their programs in ways that resemble the organization of objects in the real world, which makes programming easier and more logical. Using object- oriented programming, the overall programs are made up of many different components (called "objects"), each of which has a specific role in a program and can talk to the other components in predefined ways.
 This is the first part of several in JavaScript branch. It covers just as the title says, "Introduction". Primarily for readers who are just starting to get a bit involved in JavaScripting. Next part will be coming by next week. Oh, and remember, "It all starts with a good foundation". Before we start discussing Javascript and its capacities, let make one thing be clear - Java has nothing in common with Javascript apart from the first 4 letters. Java is a strongly typed, complied language developed by Sun Microsystems; Javascript, originally developed by Netscape is a lightweight interpreted language that was initially called Livescript.
This is the first part of several in JavaScript branch. It covers just as the title says, "Introduction". Primarily for readers who are just starting to get a bit involved in JavaScripting. Next part will be coming by next week. Oh, and remember, "It all starts with a good foundation". Before we start discussing Javascript and its capacities, let make one thing be clear - Java has nothing in common with Javascript apart from the first 4 letters. Java is a strongly typed, complied language developed by Sun Microsystems; Javascript, originally developed by Netscape is a lightweight interpreted language that was initially called Livescript.
 This is the second tutorial in three part JavaScript Tutorial series. It'll cover the language structure, the main body of JavaScript, the meat of the meal. Well, you kinda get the point by now. This part will provide a basic introduction to the Javascript language, Part 3 Common Scripts will discuss solutions to some common tasks faced by the javascripter.
This is the second tutorial in three part JavaScript Tutorial series. It'll cover the language structure, the main body of JavaScript, the meat of the meal. Well, you kinda get the point by now. This part will provide a basic introduction to the Javascript language, Part 3 Common Scripts will discuss solutions to some common tasks faced by the javascripter.
 This is the third and last tutorial in three part JavaScript Tutorial series. It covers the basic script structure as well as give examples of many widely used scripts. The readers have by now already grasp the basics of the JavaScript but this is the chery on the top. Now we shall look at what JavaScript can do, how it can be used to enhance the web experience. In this part we shall look at some of the tasks a JavaScript has to deal with on a regular basis.
This is the third and last tutorial in three part JavaScript Tutorial series. It covers the basic script structure as well as give examples of many widely used scripts. The readers have by now already grasp the basics of the JavaScript but this is the chery on the top. Now we shall look at what JavaScript can do, how it can be used to enhance the web experience. In this part we shall look at some of the tasks a JavaScript has to deal with on a regular basis.
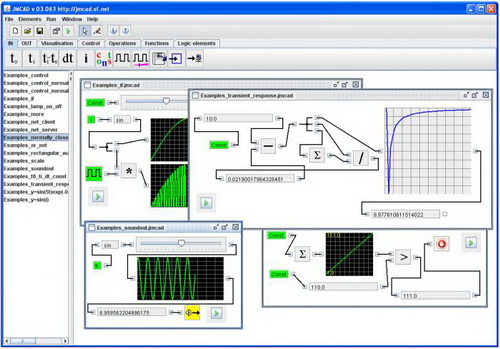 JMCAD is an open code software for modeling and simulating complex dynamic systems. It is written in Java and is available on all known operational systems. At first glance it can seem that there are not many available elements, but by combining and changing the parameters you can make and model very complex systems and in real time follow the influence of changes on an existing element.
JMCAD is an open code software for modeling and simulating complex dynamic systems. It is written in Java and is available on all known operational systems. At first glance it can seem that there are not many available elements, but by combining and changing the parameters you can make and model very complex systems and in real time follow the influence of changes on an existing element.
 This is the first in a line of new tutorials dedicated to Joomla! CMS. In the introductory tutorial we will explain the installation of Joomla! CMS, and later we will go through some basic administrations.This is a tutorial that is meant for the absolute beginners, it is simple and will explain the basics in a few words.
This is the first in a line of new tutorials dedicated to Joomla! CMS. In the introductory tutorial we will explain the installation of Joomla! CMS, and later we will go through some basic administrations.This is a tutorial that is meant for the absolute beginners, it is simple and will explain the basics in a few words.

 In this jQuery tutorial you can see the things that sets jQuery apart from other libraries. jQuery methods are divided in multiple groups that, when they are combined make his API. The thing that sets jQuery apart from other libraries are his very simple, yet very powerful methods. jQuery methods are divided in multiple groups that, when they are combined make his API.
In this jQuery tutorial you can see the things that sets jQuery apart from other libraries. jQuery methods are divided in multiple groups that, when they are combined make his API. The thing that sets jQuery apart from other libraries are his very simple, yet very powerful methods. jQuery methods are divided in multiple groups that, when they are combined make his API.
 This jQuery Tutorial assumes that you have a little previous knowledge of jQuery. It should be quite easy to follow it, if you go through each step, which will brought you at the end, before you move on to the next part of jQuery Tutorial.
This jQuery Tutorial assumes that you have a little previous knowledge of jQuery. It should be quite easy to follow it, if you go through each step, which will brought you at the end, before you move on to the next part of jQuery Tutorial.
 If you don't know anything about jQuery, here you can see jQuery Tutorial part III. jQuery - write less, do more. MANIPULATION - the Methods in this group are used to manipulate DOM elements. You can use them to do modifications, make new ones, copy, delete etc.
If you don't know anything about jQuery, here you can see jQuery Tutorial part III. jQuery - write less, do more. MANIPULATION - the Methods in this group are used to manipulate DOM elements. You can use them to do modifications, make new ones, copy, delete etc.
 This is the fourth part of our tutorials about jQuery. Today we bring to you part about jQuery Events. These methods are used for registering user actions in a browser and acting after the same ones, and also as a way to manipulate registered actions.
This is the fourth part of our tutorials about jQuery. Today we bring to you part about jQuery Events. These methods are used for registering user actions in a browser and acting after the same ones, and also as a way to manipulate registered actions.
 Hello and welcome to part V of this jQuery tutorial. This entire jQuery tutorial can be completed with any editor. Everything here is free, and we hope you like our work. If you do, feel free that you link to this tutorial on your website, blog or anywhere else where do you think is appropriate. Let knowledge be available to all.
Hello and welcome to part V of this jQuery tutorial. This entire jQuery tutorial can be completed with any editor. Everything here is free, and we hope you like our work. If you do, feel free that you link to this tutorial on your website, blog or anywhere else where do you think is appropriate. Let knowledge be available to all.
 JSPs have dynamic scripting capability that works in tandem with HTML code, separating the page logic from the static elements. JSPs are not restricted to any JSP hosting specific platform or server. It was originally created as an alternative to Microsoft's ASPs (Active Server Pages).
JSPs have dynamic scripting capability that works in tandem with HTML code, separating the page logic from the static elements. JSPs are not restricted to any JSP hosting specific platform or server. It was originally created as an alternative to Microsoft's ASPs (Active Server Pages).
.jpg) JustGage is a useful JavaScript plugin for generating and animating simple and effective dashboard gauges. It is based on the for vector drawing, so it is completely independent and self-adjusting. Considering that it is a clean SVG, it works in almost any browser: Chrome, Safari, Opera, Android, etc.
JustGage is a useful JavaScript plugin for generating and animating simple and effective dashboard gauges. It is based on the for vector drawing, so it is completely independent and self-adjusting. Considering that it is a clean SVG, it works in almost any browser: Chrome, Safari, Opera, Android, etc.
 Kindle Paperwhite is simple perfect. It comes with a new software that has removed a lot of unnecessary functions. No more voice text reading, no more headphones. You can go a page forward, a page backwards but you can not skip chapters anymore.
Kindle Paperwhite is simple perfect. It comes with a new software that has removed a lot of unnecessary functions. No more voice text reading, no more headphones. You can go a page forward, a page backwards but you can not skip chapters anymore.
 So I thought this morning I would try to be the optimist, and give reason to hope for the future of the Internet by drawing upon its present.
So I thought this morning I would try to be the optimist, and give reason to hope for the future of the Internet by drawing upon its present.Now, it may seem like there is less hope today than there was before. People are less kind. There is less trust around. I don't know. As a simple example, we could run a test here. How many people have ever hitchhiked? I know. How many people have hitchhiked within the past 10 years? Right. So what has changed? It's not better public transportation. So that's one reason to think that we might be declensionists, going in the wrong direction.

 When you hear that one USB flash drive costs about six hundred dollar, what do you think? Is it dipped in gold or covered in jewels? But, the Kingston HyperX Predator USB 3.0 justifies its price exclusively by the hardware that it has.
When you hear that one USB flash drive costs about six hundred dollar, what do you think? Is it dipped in gold or covered in jewels? But, the Kingston HyperX Predator USB 3.0 justifies its price exclusively by the hardware that it has.
 When it comes to cheaper SSD devices, The Kingston SSDNow V series doesn't need special introduction. As all other hardware components that are in the value class, these also have a solid ratio of price and quality. Although, as we know, favorable prices and SSD cards rarely go together.
When it comes to cheaper SSD devices, The Kingston SSDNow V series doesn't need special introduction. As all other hardware components that are in the value class, these also have a solid ratio of price and quality. Although, as we know, favorable prices and SSD cards rarely go together.
 Users of computers, whether professional or not, use the keyboard and mouse during their worktime on a computer. While the mouse is not problematic, the keyboard is an obstacle for many. The only way boost efficiency is to learn correct typing and by regular exercise achieve the desired speed. Luckily, the world of free software has in its collection programs that can help you.
Users of computers, whether professional or not, use the keyboard and mouse during their worktime on a computer. While the mouse is not problematic, the keyboard is an obstacle for many. The only way boost efficiency is to learn correct typing and by regular exercise achieve the desired speed. Luckily, the world of free software has in its collection programs that can help you.
 One of the common asked questions from those who are thinking about going to some GNU/Linux OS is can you install Total Commander (TC), the undisputed file manager for Windows. Its installation is possible with the use of Winea, although there are some decent replacements, like the Multi Commander, Thunar or the console Midnight Commander. They will all work perfectly, but...
One of the common asked questions from those who are thinking about going to some GNU/Linux OS is can you install Total Commander (TC), the undisputed file manager for Windows. Its installation is possible with the use of Winea, although there are some decent replacements, like the Multi Commander, Thunar or the console Midnight Commander. They will all work perfectly, but...
 We have reached the end of our series of tutorials about jQuery. We hope you've learned something new, or at least refresh the knowledge about jQuery.
We have reached the end of our series of tutorials about jQuery. We hope you've learned something new, or at least refresh the knowledge about jQuery. 
 Cooler Master has announced an advanced series of the Cooler Master Seidon Liquid Cooling System - the Seidon 120XL/240M. The Sedion 120XL and 240M and water blocks of high performances that are built from one piece of copper with special micro canals that maximize the dispersion of heat.
Cooler Master has announced an advanced series of the Cooler Master Seidon Liquid Cooling System - the Seidon 120XL/240M. The Sedion 120XL and 240M and water blocks of high performances that are built from one piece of copper with special micro canals that maximize the dispersion of heat.
 We all know that we need more bandwidth now, than we ever did in the past. There tons more online games, online movies, online collab work, you name it. And the past standards of Wifi namely 802.11a, 802.11b, 802.11g, 802.11n, and so on) were getting better and better; however, the 802.11ac does the trick. Well, atleast for now it is, until something better comes along.
We all know that we need more bandwidth now, than we ever did in the past. There tons more online games, online movies, online collab work, you name it. And the past standards of Wifi namely 802.11a, 802.11b, 802.11g, 802.11n, and so on) were getting better and better; however, the 802.11ac does the trick. Well, atleast for now it is, until something better comes along.
 In school, our teachers told us that putting off studying and cramming for a test was useless to everyone because, in their own words, "You're only hurting yourself." But who actually listened to them? I know I didn't. I skated through high school and came out of it nearly as empty-headed as when I came in. The public school system doesn't really care how much you learn, so long as you improve their test scores and don't cause much trouble. These low standards mean even average students quickly develop an inflated sense of self-worth.
In school, our teachers told us that putting off studying and cramming for a test was useless to everyone because, in their own words, "You're only hurting yourself." But who actually listened to them? I know I didn't. I skated through high school and came out of it nearly as empty-headed as when I came in. The public school system doesn't really care how much you learn, so long as you improve their test scores and don't cause much trouble. These low standards mean even average students quickly develop an inflated sense of self-worth.
 It is official: the Nokia 808 PureView is the last mobile phone with a Symbian platform.Symbian has been on its death bed for a long time. Nokia placed it in the "Maintenance mode" in October, and with the beginning of the last year Stiven Elop said that competition challenges can't be solved in that way. It looks like Symbian won't be missed.
It is official: the Nokia 808 PureView is the last mobile phone with a Symbian platform.Symbian has been on its death bed for a long time. Nokia placed it in the "Maintenance mode" in October, and with the beginning of the last year Stiven Elop said that competition challenges can't be solved in that way. It looks like Symbian won't be missed.
 The advantages of a USB flash memory over a CD or DVD are obvious and indisputable. The speed and efficiency of data manipulation, and the ever growing capacity, with the constant drop of prices made the popular flashes became the integral part of everybody's personal pocket inventory. When you add the fact that most new computers have the option to boot from transportable media, it is completely logical that this method will become popular and almost a default way to start live systems.
The advantages of a USB flash memory over a CD or DVD are obvious and indisputable. The speed and efficiency of data manipulation, and the ever growing capacity, with the constant drop of prices made the popular flashes became the integral part of everybody's personal pocket inventory. When you add the fact that most new computers have the option to boot from transportable media, it is completely logical that this method will become popular and almost a default way to start live systems.
 LinkedIn is the world's largest business professional social network where business people share experiences, participate in discussions, share interesting content and, of course, find new employers.
LinkedIn is the world's largest business professional social network where business people share experiences, participate in discussions, share interesting content and, of course, find new employers.
 LinkedIn is a very serious business network that was only intended for people who want to do business, but know it has opened it's doors to younger people who strive to be businessmen. LinkedIn has lowered the minimal age limit for it's users and it is now 13 in Europe and 14 in the USA.
LinkedIn is a very serious business network that was only intended for people who want to do business, but know it has opened it's doors to younger people who strive to be businessmen. LinkedIn has lowered the minimal age limit for it's users and it is now 13 in Europe and 14 in the USA.
.jpg) There are several ways of connecting to networks by using Linksys routers and they are:
There are several ways of connecting to networks by using Linksys routers and they are:1. The manual setup
This is probably the most hands on solution and it is possibly the best one. You will manually connect to a Linksys network by linking your computer to a Linksys router via Ethernet cable, then you open the browser and connect the router console on http://192.168.1.1/. This allows you to do many things such as changing a lot of router options and also many more things.

 Since the introduction of the power PC processor, developers have been actively striving to create a flavor of Linux that runs efficiently on Apple Hardware while retaining the Mac's trademark ease of use.
Since the introduction of the power PC processor, developers have been actively striving to create a flavor of Linux that runs efficiently on Apple Hardware while retaining the Mac's trademark ease of use.
 Do you often feel tethered to your home computer or other electronic devices? Tired of the endless cords to untangle under your office desk? Then it's time to go completely wireless! It's easier than ever to live a completely wireless lifestyle, thanks to innovations in the consumer and business electronics industries. Review some of the latest gadgets and services that will have you free-wheeling it in no time.
Do you often feel tethered to your home computer or other electronic devices? Tired of the endless cords to untangle under your office desk? Then it's time to go completely wireless! It's easier than ever to live a completely wireless lifestyle, thanks to innovations in the consumer and business electronics industries. Review some of the latest gadgets and services that will have you free-wheeling it in no time.
 From a technical point of view, the A10-5700 has four (ALU) cores and two FPU units. The default tact made out of solid 3,4 GHz sometimes goes up to 4 GHz. Frankly, it is about two values around which this APU gravitates the most and you will find it around them most of the time, no matter what the strain is.
From a technical point of view, the A10-5700 has four (ALU) cores and two FPU units. The default tact made out of solid 3,4 GHz sometimes goes up to 4 GHz. Frankly, it is about two values around which this APU gravitates the most and you will find it around them most of the time, no matter what the strain is.
 Logitech states that the main advantages of the K810 are the background lighting, the integrated battery, the bluetooth connection and its easy transferring from device to device. The manufacturer says that this keyboard is ideal for all that can connect to a Tablet, PC, smartphone, etc. On the backside you have all the possibilities described in detail, and it is not hard to conclude that Logitech has faith in the quality of manufacturing that characterizes the K810.
Logitech states that the main advantages of the K810 are the background lighting, the integrated battery, the bluetooth connection and its easy transferring from device to device. The manufacturer says that this keyboard is ideal for all that can connect to a Tablet, PC, smartphone, etc. On the backside you have all the possibilities described in detail, and it is not hard to conclude that Logitech has faith in the quality of manufacturing that characterizes the K810. 
 Manufacturers from time to time like to make a "field trip" and do something exotic, something dedicated only for one Operating system. This time it was the company Logitech that made a chargeable touchpad for use only on the Mac Operating system.
Manufacturers from time to time like to make a "field trip" and do something exotic, something dedicated only for one Operating system. This time it was the company Logitech that made a chargeable touchpad for use only on the Mac Operating system.
 Have you obtained your degree and are you looking for that job that will make you rich and famous in your field? Then you are not the first to be disappointed when you go out there with your resume. The recession has made everything slow down and while this is a hurdle that every generation faces the competition gets tougher with every year that passes. Having a degree with an experience makes you join the ranks of the hundreds in a similar position. Career counselors advise the addition of as many certification courses and addition career related courses to ...
Have you obtained your degree and are you looking for that job that will make you rich and famous in your field? Then you are not the first to be disappointed when you go out there with your resume. The recession has made everything slow down and while this is a hurdle that every generation faces the competition gets tougher with every year that passes. Having a degree with an experience makes you join the ranks of the hundreds in a similar position. Career counselors advise the addition of as many certification courses and addition career related courses to ...
 Gaming is headed in the wrong direction and that manufacturers have drifted out of touch with the gaming public. I too share Yamauchi's belief that gaming is headed in the wrong direction and that manufacturers have drifted out of touch with the gaming public, in rather dot-com fashion.
Gaming is headed in the wrong direction and that manufacturers have drifted out of touch with the gaming public. I too share Yamauchi's belief that gaming is headed in the wrong direction and that manufacturers have drifted out of touch with the gaming public, in rather dot-com fashion.
 I wanted to take bit of time to introduce you to Batch Scripting in Windows environment. If you have no idea what Batch Script is, then this is for you. Keep an eye out for Batch Scripting Tutorials and Scripts soon to come.
I wanted to take bit of time to introduce you to Batch Scripting in Windows environment. If you have no idea what Batch Script is, then this is for you. Keep an eye out for Batch Scripting Tutorials and Scripts soon to come.
 Better to face it. Your Mac isn't invincible, while it may be less vulnerable to viruses and spyware than PCs. It is possible for your Mac to get stolen or suffer from a hardware failure like a hard drive crash. If and when that happens, what will it be to you? Will it be a catastrophe, something that you just cannot get your head around, or will it be an expensive and annoying inconvenience but otherwise fine? It depends entirely on whether or not backup your data, and how well and how often.
Better to face it. Your Mac isn't invincible, while it may be less vulnerable to viruses and spyware than PCs. It is possible for your Mac to get stolen or suffer from a hardware failure like a hard drive crash. If and when that happens, what will it be to you? Will it be a catastrophe, something that you just cannot get your head around, or will it be an expensive and annoying inconvenience but otherwise fine? It depends entirely on whether or not backup your data, and how well and how often.
 When a misfortune finds you, it feels like a violation. The understanding and use of Mac photo recovery software will go a long ways to hopefully providing you comfort to recover precious, one-time photos and videos. Mac photo recovery software will be your ally when the unexpected happens. However, it is good that you clearly understand the causes of data file loss to improve your chances of recovering such files, whether they be photos, videos, music or other data files.
When a misfortune finds you, it feels like a violation. The understanding and use of Mac photo recovery software will go a long ways to hopefully providing you comfort to recover precious, one-time photos and videos. Mac photo recovery software will be your ally when the unexpected happens. However, it is good that you clearly understand the causes of data file loss to improve your chances of recovering such files, whether they be photos, videos, music or other data files.
 The following is a brief outline of the advantages and the disadvantages of Magento as a Shopping cart. It gives a detailed analysis of the reasons that one should choose Magento for, as well as things that they must be careful about while using Magento. . If the few disadvantages can be overcome, then it is surely one of the best shopping cart platforms.
The following is a brief outline of the advantages and the disadvantages of Magento as a Shopping cart. It gives a detailed analysis of the reasons that one should choose Magento for, as well as things that they must be careful about while using Magento. . If the few disadvantages can be overcome, then it is surely one of the best shopping cart platforms.
 Most of us store a large number of pictures from various events, occasions and happenings on our hard drive. Occasionally we sift through them to remind ourselves of some nice events or to show the pictures to someone else. The more creative ones with a little better program knowledge will make clips, in which slideshows of the desired pictures will be shown, and maybe with music. The less skilled ones can do the same if the install a program called PhotoFilmStrip.
Most of us store a large number of pictures from various events, occasions and happenings on our hard drive. Occasionally we sift through them to remind ourselves of some nice events or to show the pictures to someone else. The more creative ones with a little better program knowledge will make clips, in which slideshows of the desired pictures will be shown, and maybe with music. The less skilled ones can do the same if the install a program called PhotoFilmStrip.
 There is a common misconception amongst many computer enthusiasts that they need some $50 gizmo software to take screenshots. However, that's far from truth. The fact is that your computer is fully capable of creating screenshots all on its own with needing to spend any money, or install some software to achieve this goal. That said, a quality screenshot software may add some neat options to taking screenshots that you may not already have.
There is a common misconception amongst many computer enthusiasts that they need some $50 gizmo software to take screenshots. However, that's far from truth. The fact is that your computer is fully capable of creating screenshots all on its own with needing to spend any money, or install some software to achieve this goal. That said, a quality screenshot software may add some neat options to taking screenshots that you may not already have.
 Here are easy to apply tips and tricks to make your laptop batteries last for much longer periods of time. Charge and immediately discharge your batteries a few times before relying on them.
Here are easy to apply tips and tricks to make your laptop batteries last for much longer periods of time. Charge and immediately discharge your batteries a few times before relying on them. 
 If you want to create you don't always need to be a programer. You can just open the network and find sites designed for creating. Creating games on the network can be fun and easy, and after that you enjoy your own games. Down below you have one site that is purely made for creating an network platform game.
If you want to create you don't always need to be a programer. You can just open the network and find sites designed for creating. Creating games on the network can be fun and easy, and after that you enjoy your own games. Down below you have one site that is purely made for creating an network platform game.
 Since Google made its debut in September 1998, the web designers, developers, programmers, and consultants of this world have been going crazy ensuring that their websites are Google friendly. Just how do they do it?
Since Google made its debut in September 1998, the web designers, developers, programmers, and consultants of this world have been going crazy ensuring that their websites are Google friendly. Just how do they do it?
 How many of you had to fill out some sort of web form where you've been asked to read a distorted sequence of characters like this? How many of you found it really, really annoying? Okay, outstanding. So I invented that. Or I was one of the people who did it. That thing is called a CAPTCHA. And the reason it is there is to make sure you, the entity filling out the form, are actually a human and not some sort of computer program that was written to submit the form millions and millions of times.
How many of you had to fill out some sort of web form where you've been asked to read a distorted sequence of characters like this? How many of you found it really, really annoying? Okay, outstanding. So I invented that. Or I was one of the people who did it. That thing is called a CAPTCHA. And the reason it is there is to make sure you, the entity filling out the form, are actually a human and not some sort of computer program that was written to submit the form millions and millions of times. 
 In this tutorial, we are going to reproduce some of the logo effect of the film "Matrix" using MAYA particles and expressions.
In this tutorial, we are going to reproduce some of the logo effect of the film "Matrix" using MAYA particles and expressions.
 The hash function is a way of mapping a collection of information that can be various lengths in other values of fixed length. The values that the hash function gives are called hash values, codes, sums, checksums or simply hashes. MD5 is a cryptographic hash algorithm, which means that it takes information of arbitrary length and creates fixed lengths for it, a cryptographic hash value, in a way that any change of data (accidental or on purpose) leads to the change of that value.
The hash function is a way of mapping a collection of information that can be various lengths in other values of fixed length. The values that the hash function gives are called hash values, codes, sums, checksums or simply hashes. MD5 is a cryptographic hash algorithm, which means that it takes information of arbitrary length and creates fixed lengths for it, a cryptographic hash value, in a way that any change of data (accidental or on purpose) leads to the change of that value.
 This tutorial builds on what was discussed last week. This week you will be examining the code for an extended version of the members only section.
This tutorial builds on what was discussed last week. This week you will be examining the code for an extended version of the members only section.
 In computing, a keyboard shortcut or hotkey is a finite set of one or more keys that invoke a software or operating system operation when triggered by the user. Keyboard shortcuts are typically an alternate means for invoking one or more commands that would otherwise be accessible only through a menu, a pointing device, different levels of a user interface, or via a command console. The following is a list of all the known shortcuts for Microsoft Access Database.
In computing, a keyboard shortcut or hotkey is a finite set of one or more keys that invoke a software or operating system operation when triggered by the user. Keyboard shortcuts are typically an alternate means for invoking one or more commands that would otherwise be accessible only through a menu, a pointing device, different levels of a user interface, or via a command console. The following is a list of all the known shortcuts for Microsoft Access Database.
 XP, the operating system developed by Microsoft Corporation after the dawn of the millennium brought about novel, effective changes in the field of computers. Microsoft Vista which made its entry into the market in 2007 has got mixed reviews among users.
XP, the operating system developed by Microsoft Corporation after the dawn of the millennium brought about novel, effective changes in the field of computers. Microsoft Vista which made its entry into the market in 2007 has got mixed reviews among users.
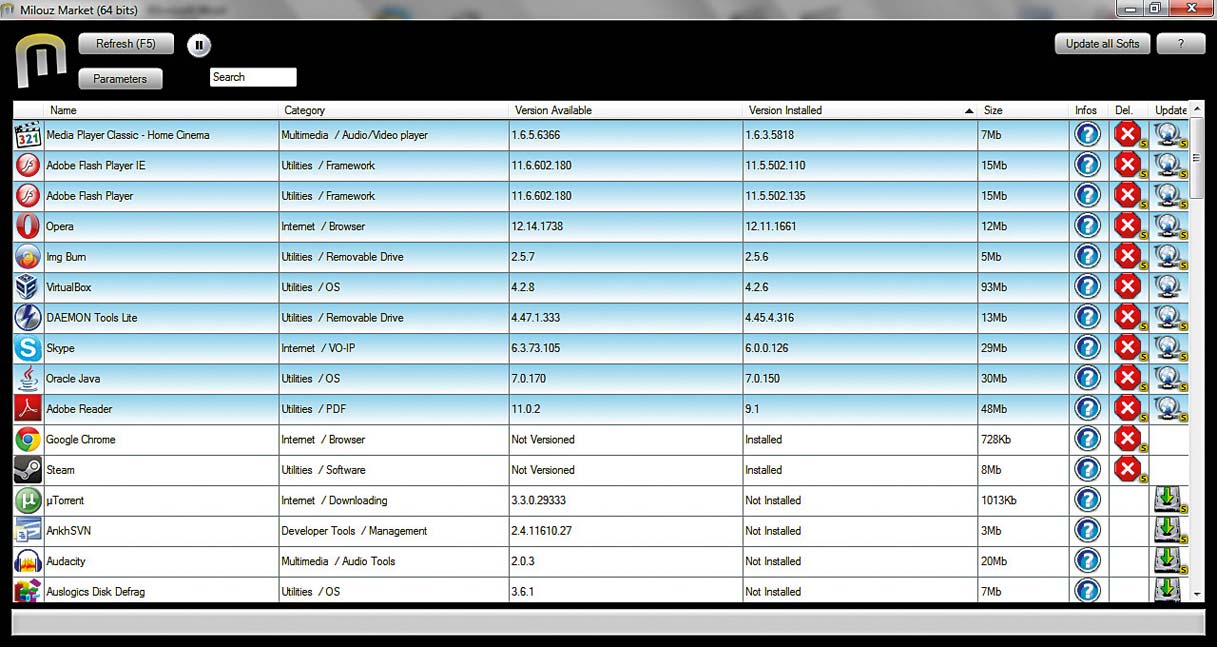 The first thing you will say when you start Milouz Market is "God, how ugly is this!". Really, the author of the program seems to have completely disregarded the visual side of his offspring and trapped it somewhere in the 90'. A bulky table, large icons without applied means for polishing, badly chosen colors...
The first thing you will say when you start Milouz Market is "God, how ugly is this!". Really, the author of the program seems to have completely disregarded the visual side of his offspring and trapped it somewhere in the 90'. A bulky table, large icons without applied means for polishing, badly chosen colors...
 All of us that like to make an old PC into a multimedia multipractic or simply own a PC computer linked to (HD)TV have a problem of remote control from the seat. Even smart TV's and Blu-ray players struggle with this problem.
All of us that like to make an old PC into a multimedia multipractic or simply own a PC computer linked to (HD)TV have a problem of remote control from the seat. Even smart TV's and Blu-ray players struggle with this problem.
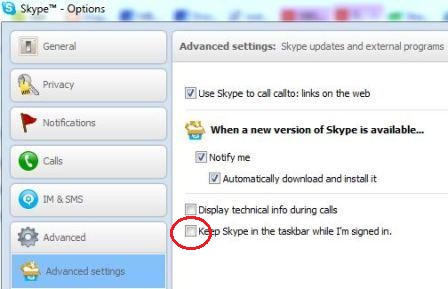 Since the appearance of the Windows 7 and its new design solutions, a lot of habits that we had on computers have been changed. For example, we are not minimizing applications to the system tray, but instead of that most software application are now making their icon on the Windows 7 Taskbar. A few of the latest apps are Skype, and Windows Live Messenger.
Since the appearance of the Windows 7 and its new design solutions, a lot of habits that we had on computers have been changed. For example, we are not minimizing applications to the system tray, but instead of that most software application are now making their icon on the Windows 7 Taskbar. A few of the latest apps are Skype, and Windows Live Messenger.
 Allow me the to take you into the wonderful world of the Palm OS. This is the system that today powers over 75% of the personal mobile handheld market.
Allow me the to take you into the wonderful world of the Palm OS. This is the system that today powers over 75% of the personal mobile handheld market.

 Even if you are not one of the 200 million people who use the social networking site Twitter, you must be aware of its impressive size For all Twitter users, and people who like a nice visualization of the flow of large amounts of data, we recommend Tweetping.
Even if you are not one of the 200 million people who use the social networking site Twitter, you must be aware of its impressive size For all Twitter users, and people who like a nice visualization of the flow of large amounts of data, we recommend Tweetping.
 FIREWALL - By its function it is an expanded capabilities gateway. Expansion refers primarily to prevent unauthorized access to the network in general. Aforementioned means that the network device provides control of traffic between the Internet and a local network in a way that all incoming Internet traffic is filtered according to defined filtering rules.
FIREWALL - By its function it is an expanded capabilities gateway. Expansion refers primarily to prevent unauthorized access to the network in general. Aforementioned means that the network device provides control of traffic between the Internet and a local network in a way that all incoming Internet traffic is filtered according to defined filtering rules.
 In many homes, the network can't easily reach all areas a person needs. This fact surprises many people. Stringing network cables to some rooms may prove impractical, of course. But even in wireless networks, "cold spots" where the Wi - Fi radio signals will not reach the corner of the bedroom, study or porches are also common. Be prepared that there is some planing needed in network installation.
In many homes, the network can't easily reach all areas a person needs. This fact surprises many people. Stringing network cables to some rooms may prove impractical, of course. But even in wireless networks, "cold spots" where the Wi - Fi radio signals will not reach the corner of the bedroom, study or porches are also common. Be prepared that there is some planing needed in network installation.
 TCP ports will popup almost with any application you use wether it is ICQ or FTP. It will soon be realized how good its knowledge is once you yourself will start applying it in day to day tech use. TCP/IP uses several protocols, the two main ones being TCP and IP.
TCP ports will popup almost with any application you use wether it is ICQ or FTP. It will soon be realized how good its knowledge is once you yourself will start applying it in day to day tech use. TCP/IP uses several protocols, the two main ones being TCP and IP.
 iOS has been governing the markets since its entry into the market. Each day brings in a new application that further increases its popularity.Apple has had a long history of being the blue eyed kid on the block. This results in a massive demand for iPhone and iPad applications. Also, since Apple allows only selective apps in its iTunes Gallery, it ensures that the apps are of high quality.
iOS has been governing the markets since its entry into the market. Each day brings in a new application that further increases its popularity.Apple has had a long history of being the blue eyed kid on the block. This results in a massive demand for iPhone and iPad applications. Also, since Apple allows only selective apps in its iTunes Gallery, it ensures that the apps are of high quality.
 The motherboard represents the logical foundation of the computer. In other words, everything that makes a computer a computer must be attached to the motherboard. From the CPU to storage devices, from RAM to printer ports, the motherboard provides the connections that help them work together.
The motherboard represents the logical foundation of the computer. In other words, everything that makes a computer a computer must be attached to the motherboard. From the CPU to storage devices, from RAM to printer ports, the motherboard provides the connections that help them work together.
 This is a very simple tutorial showing the readers how to add a motion blur affect to your pics. It's something I would recommend for a total beginner of PhotoShop as well.
This is a very simple tutorial showing the readers how to add a motion blur affect to your pics. It's something I would recommend for a total beginner of PhotoShop as well.
 This tutorial covers almost every part of Access database system. Its a sure shot for any beginner for MS Access.
This tutorial covers almost every part of Access database system. Its a sure shot for any beginner for MS Access.
 This is a usefull little guide for all you newbies out there in cyberspace. It will teach you some tricks that your co-workers and supervisors will admire.
This is a usefull little guide for all you newbies out there in cyberspace. It will teach you some tricks that your co-workers and supervisors will admire.
 We bring to you small MS-DOS tutorial. A list of all the MS-DOS commands that we know of compiled into one easy to read list. If there is anything bugging you with DOS commands or if you've been looking for that one particular command that you needed and couldn't remember?
We bring to you small MS-DOS tutorial. A list of all the MS-DOS commands that we know of compiled into one easy to read list. If there is anything bugging you with DOS commands or if you've been looking for that one particular command that you needed and couldn't remember?
 To rate the performance of the seven large-screen LCD monitors in our roundup, we turned to the industry standard utility, DisplayMate. Developed by DisplayMate Technologies (www.displaymate.com), the utility provides a set of specially designed screen images to test different aspects of a monitor's performance. DisplayMate provides a special script for LCD monitor testing, with almost two dozen tests that check resolution, bandwidth, pixel timing, tracking, grayscale, and color performance. The utility also tests for monitor problems.
To rate the performance of the seven large-screen LCD monitors in our roundup, we turned to the industry standard utility, DisplayMate. Developed by DisplayMate Technologies (www.displaymate.com), the utility provides a set of specially designed screen images to test different aspects of a monitor's performance. DisplayMate provides a special script for LCD monitor testing, with almost two dozen tests that check resolution, bandwidth, pixel timing, tracking, grayscale, and color performance. The utility also tests for monitor problems.
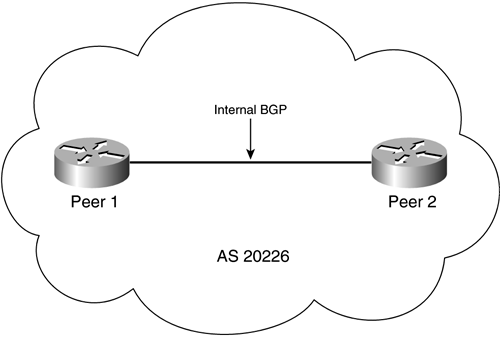 Today we are going to talk about multihoming networks. They are a way to share a few connection into external network. There is also a way to increase your network speed by using multihoming.
Today we are going to talk about multihoming networks. They are a way to share a few connection into external network. There is also a way to increase your network speed by using multihoming.
 You have probably encountered multiple lists of data, where you with the choosing of one piece of data you get another list filled, filtered by the chosen piece of information. For example, you would chose the state, then the city and finally the street.
You have probably encountered multiple lists of data, where you with the choosing of one piece of data you get another list filled, filtered by the chosen piece of information. For example, you would chose the state, then the city and finally the street.
 This article discusses some of the "So Called Facts" that we take for granted not admitting to ourselves that we honestly don't know. In most cases we aren't even sure of some of the things we believe about the IT world these days.
This article discusses some of the "So Called Facts" that we take for granted not admitting to ourselves that we honestly don't know. In most cases we aren't even sure of some of the things we believe about the IT world these days.
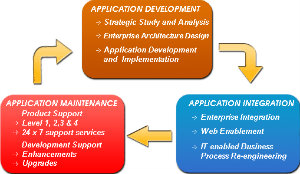 N-tier application architecture provides a model for developers to create a flexible and reusable application. By breaking up an application into tiers, developers only have to modify or add a specific layer, rather than have to rewrite the entire application over, if they decide to change technologies or scale up.
N-tier application architecture provides a model for developers to create a flexible and reusable application. By breaking up an application into tiers, developers only have to modify or add a specific layer, rather than have to rewrite the entire application over, if they decide to change technologies or scale up.
 What is the Internet backbone? Who runs the Internet backbone? Why can't I connect directly to the Internet backbone? Find out these questions in this edition of TW Articles.
What is the Internet backbone? Who runs the Internet backbone? Why can't I connect directly to the Internet backbone? Find out these questions in this edition of TW Articles.
 While you are trying to access your blog you notice that the page is loading very slowly. You see that Dropbox is syncing something and you know that YouTube is on. You have torrents you want to download. The easiest way would be to turn all that off and let the blog load, but that is not what you want.
While you are trying to access your blog you notice that the page is loading very slowly. You see that Dropbox is syncing something and you know that YouTube is on. You have torrents you want to download. The easiest way would be to turn all that off and let the blog load, but that is not what you want.
 The report on spending on online advertising - AdEx Benchmark 2012, which is annually published by IAB Europe, confirmed that 2012 was very successful when it comes to this industry, as it is the first time it surpassed the value of spending on advertising in print.
The report on spending on online advertising - AdEx Benchmark 2012, which is annually published by IAB Europe, confirmed that 2012 was very successful when it comes to this industry, as it is the first time it surpassed the value of spending on advertising in print.
 In this time, our children are using computers more and more. There have been discussions going on for years now about the use of computers in children. Some say the effects are good, some say the effects are bad, some say there are no effect at all. If you have a child and you are wondering if you are going to let your kid go on the network, read this text about children and networks.
In this time, our children are using computers more and more. There have been discussions going on for years now about the use of computers in children. Some say the effects are good, some say the effects are bad, some say there are no effect at all. If you have a child and you are wondering if you are going to let your kid go on the network, read this text about children and networks.
.jpg) "Burning" copies to optical (CD-ROM or DVD-ROM) discs is a very simple way if you want to back up your files, or anything else. You will be able to select folders and files you want to backup, and after that copy those files by using a computer CD/DVD writing program which does exactly that. You don't necessarily need to be connected to a network for the backing up if your computers have a CD-ROM or DVD-ROM writer.
"Burning" copies to optical (CD-ROM or DVD-ROM) discs is a very simple way if you want to back up your files, or anything else. You will be able to select folders and files you want to backup, and after that copy those files by using a computer CD/DVD writing program which does exactly that. You don't necessarily need to be connected to a network for the backing up if your computers have a CD-ROM or DVD-ROM writer.
 Microsoft Windows (and other personal operating systems) contain a built-in file sharing system. For example, the Windows folder can be shared over a local network (LAN) or the Internet by using Explorer as well as network drive mappings. You are also able to set restrictions on access security in order to control who can get the shared files.
Microsoft Windows (and other personal operating systems) contain a built-in file sharing system. For example, the Windows folder can be shared over a local network (LAN) or the Internet by using Explorer as well as network drive mappings. You are also able to set restrictions on access security in order to control who can get the shared files.
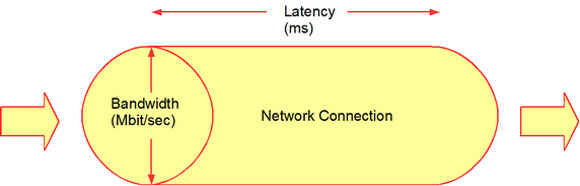 There are other things than bandwidth when you think of network speed. The other thing that many people don't know about is network latency which is a great contributor to the speed of a network. It stands for various delays that happen when a device is processing data that comes from the network. If you talk about a low latency connection it is the faster one because it has small delay and the bigger latency network connection have bigger delays so they are slower because of those delays.
There are other things than bandwidth when you think of network speed. The other thing that many people don't know about is network latency which is a great contributor to the speed of a network. It stands for various delays that happen when a device is processing data that comes from the network. If you talk about a low latency connection it is the faster one because it has small delay and the bigger latency network connection have bigger delays so they are slower because of those delays.
 This tutorial can be thought of as God sent. It will not only get you through Network+ Exam but is very hand resource for all those of you who are already in the networking field. Don't leave home without it!
This tutorial can be thought of as God sent. It will not only get you through Network+ Exam but is very hand resource for all those of you who are already in the networking field. Don't leave home without it!
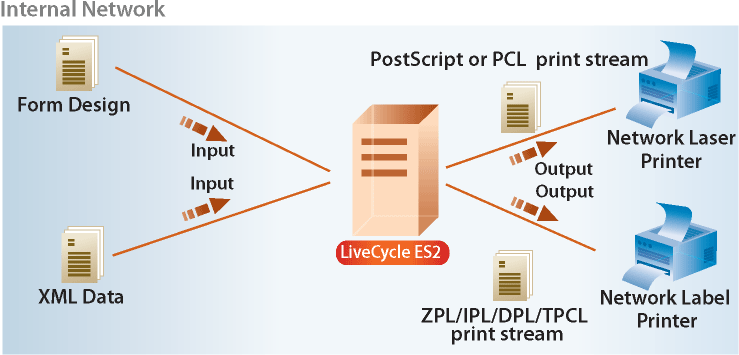 Printing in Windows is now easier. When you connect the printer to a computer or add a new printer or home network, you can begin printing. For most people this is all they have to do. Printing is easier because Windows supports most printers without the need for downloads or CDs. If you are using Windows 8, support for additional printers is available on the network through Windows Update.
Printing in Windows is now easier. When you connect the printer to a computer or add a new printer or home network, you can begin printing. For most people this is all they have to do. Printing is easier because Windows supports most printers without the need for downloads or CDs. If you are using Windows 8, support for additional printers is available on the network through Windows Update.
 We have all been the target of spammers. Imagine yourself sitting at home, by your computer and then the spamming begins. You are sure to get tons and tons of messages you don't want if you are the target of a spammer. But you are not the only one, read the text below to find out more.
We have all been the target of spammers. Imagine yourself sitting at home, by your computer and then the spamming begins. You are sure to get tons and tons of messages you don't want if you are the target of a spammer. But you are not the only one, read the text below to find out more.
 Here it depends on the quality of the video you are viewing. It is of course needed to have a basic network speed value, but if the quality of the video is really low you won't need much bandwidth and if the quality is 1080 p you will need good bandwidth. Also if the video you are watching features a lot of moving and effects higher bandwidth will be needed opposed to videos with less movement and effects.
Here it depends on the quality of the video you are viewing. It is of course needed to have a basic network speed value, but if the quality of the video is really low you won't need much bandwidth and if the quality is 1080 p you will need good bandwidth. Also if the video you are watching features a lot of moving and effects higher bandwidth will be needed opposed to videos with less movement and effects.
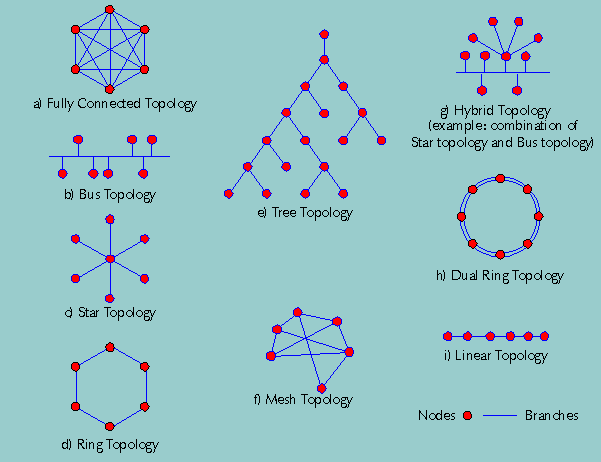 There are a lot of network terms, and sometimes they can be very confusing. In this article you will read some networks explained, and in tomorrows article you will read the second part of this text, and with that more network terms will be explained.
There are a lot of network terms, and sometimes they can be very confusing. In this article you will read some networks explained, and in tomorrows article you will read the second part of this text, and with that more network terms will be explained.
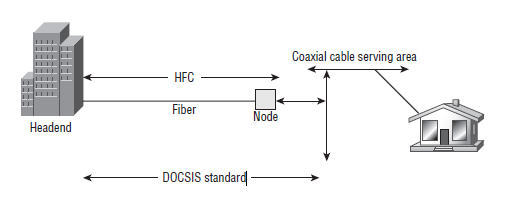 Asynchronous Balanced Mode - an HDLC (and derivative protocol) communication mode supporting peer-oriented, point-to- point communications between two stations, where either station can initiate transmission.
Asynchronous Balanced Mode - an HDLC (and derivative protocol) communication mode supporting peer-oriented, point-to- point communications between two stations, where either station can initiate transmission.
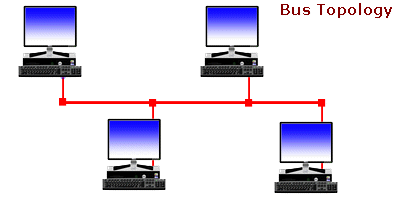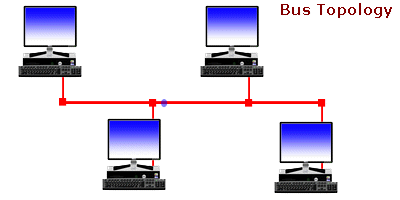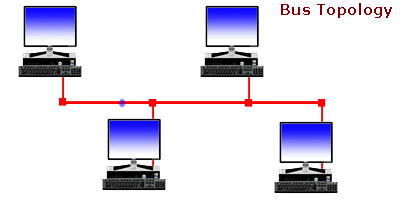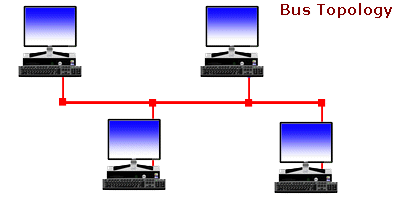 Ever wonder... how are all of these file, print, fax, and computer resources connected so as to allow the typical desktop computer to access them? Network topology refers to the way networked computers and network resources are connected. The three most widely used topologies are bus, ring, and star. Note that the following network topology diagrams are logical views of the topologies they represent and don’t necessarily match the physical (electrical) interconnections on the networks.
Ever wonder... how are all of these file, print, fax, and computer resources connected so as to allow the typical desktop computer to access them? Network topology refers to the way networked computers and network resources are connected. The three most widely used topologies are bus, ring, and star. Note that the following network topology diagrams are logical views of the topologies they represent and don’t necessarily match the physical (electrical) interconnections on the networks.
 A big thing people used to do some years back was to tweak their dial up. They did this because it was slows and they wanted it to be faster. The things they did usually were useless, but there are other things you can do that work.
A big thing people used to do some years back was to tweak their dial up. They did this because it was slows and they wanted it to be faster. The things they did usually were useless, but there are other things you can do that work.
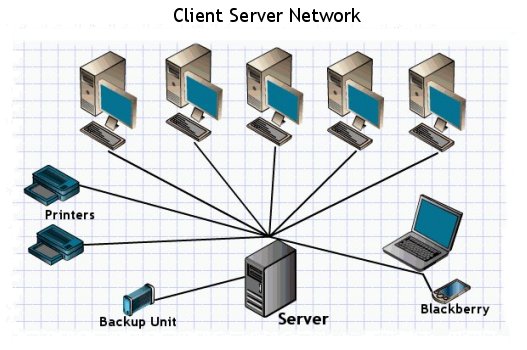 Computer network, according to their size and features they have, are classified into two main groups: A local area network (LAN) is the foundation of any network. It can be simple (two computers connected by a cable), or complex (hundreds of computers and peripheral devices in a large corporation).
Computer network, according to their size and features they have, are classified into two main groups: A local area network (LAN) is the foundation of any network. It can be simple (two computers connected by a cable), or complex (hundreds of computers and peripheral devices in a large corporation). 
 In any wired LAN environment it becomes necessary to take utmost care while selecting cables for the network setup. Engineers and administrators may select cable types according to the requirements of the LAN setup, budget involved in the infrastructure installation and the scalability of the network. Since cables play important role in any wired network infrastructure it becomes important for the administrators and engineers to select appropriate cable types so as to meet and fulfill the requirements of the organizations.
In any wired LAN environment it becomes necessary to take utmost care while selecting cables for the network setup. Engineers and administrators may select cable types according to the requirements of the LAN setup, budget involved in the infrastructure installation and the scalability of the network. Since cables play important role in any wired network infrastructure it becomes important for the administrators and engineers to select appropriate cable types so as to meet and fulfill the requirements of the organizations.
 This very much to the point guide highlights some important networking terms and topics and simplifies them to us, the mere mortals.
This very much to the point guide highlights some important networking terms and topics and simplifies them to us, the mere mortals.
.jpg) With increasing use of broadband connection on the network, especially for home users, there is more and more need to establish a home network. This is usually not a problem, since nearly all motherboards include network adapters. Network adapters in the form of cards are extremely cheap, and most routers using ADSL include a switch, which is usually not completely filled out. However, this way of connecting your computer may not always be the most suitable.
With increasing use of broadband connection on the network, especially for home users, there is more and more need to establish a home network. This is usually not a problem, since nearly all motherboards include network adapters. Network adapters in the form of cards are extremely cheap, and most routers using ADSL include a switch, which is usually not completely filled out. However, this way of connecting your computer may not always be the most suitable.
 Like a television program or a detective novel, the computer has the power to keep the user's attention is often much longer than they really wanted this. This is true for adults, but even more so for children. Because it often happens that children can not wait to come back to the computer. Is it therefore to say that the computer is a type of drug that can make their customers dependent? The authors of the book "Child and computer" are generally skeptical about this possibility.
Like a television program or a detective novel, the computer has the power to keep the user's attention is often much longer than they really wanted this. This is true for adults, but even more so for children. Because it often happens that children can not wait to come back to the computer. Is it therefore to say that the computer is a type of drug that can make their customers dependent? The authors of the book "Child and computer" are generally skeptical about this possibility.
 A new year brings new things. The company Chieftec introduced a new computer case designed for gamers that belongs to the popular Dragon family, and it has got the mark DX-02B. Unlike other solutions from the the Dragon family, the DX-02B has even better manufacturing quality, more powerful design and a very advanced cooling system that can chill even the hottest core components.
A new year brings new things. The company Chieftec introduced a new computer case designed for gamers that belongs to the popular Dragon family, and it has got the mark DX-02B. Unlike other solutions from the the Dragon family, the DX-02B has even better manufacturing quality, more powerful design and a very advanced cooling system that can chill even the hottest core components.
 Lexmark debuted on the market where Canon and HP ruled and it kept going forward - today Lexmark solutions stand shoulder to shoulder with the competition, and in certain parts are even better than them. An obvious improvement can be seen in solutions that have been presented by the start of this year.
Lexmark debuted on the market where Canon and HP ruled and it kept going forward - today Lexmark solutions stand shoulder to shoulder with the competition, and in certain parts are even better than them. An obvious improvement can be seen in solutions that have been presented by the start of this year.
 Noticed a new unusual TechiWareHouse? Well read all about it in this week's Techi Article. It's not just to let you know what we've done by also WHY! You webmasters out there can learn a thing or two, so get your butt over here.
Noticed a new unusual TechiWareHouse? Well read all about it in this week's Techi Article. It's not just to let you know what we've done by also WHY! You webmasters out there can learn a thing or two, so get your butt over here.
 The system of collecting information together in "files" which in turn are grouped in "directories" or "folders" provides a method for naming and addressing information that is familiar to most PC users. But the mechanics of how the information is actually physically placed on the hard drive and retrieved is not something most of us ever think about.
The system of collecting information together in "files" which in turn are grouped in "directories" or "folders" provides a method for naming and addressing information that is familiar to most PC users. But the mechanics of how the information is actually physically placed on the hard drive and retrieved is not something most of us ever think about.
 As always, M!cro$#!t was there to help us with their awesome and almost God-like helping hand by creating Page Transitions feature in their (then latest) MS FrontPage. And other software manufacturers followed MS like a pack of sheep trying to stay tight in a herd.
As always, M!cro$#!t was there to help us with their awesome and almost God-like helping hand by creating Page Transitions feature in their (then latest) MS FrontPage. And other software manufacturers followed MS like a pack of sheep trying to stay tight in a herd.
 What people need is a one stop computer expert and that's practically impossible to find. Today what happens is that people go to a computer expert and they find that they can either go to an expert in hardware, in software, in sales, or support. The sales guy is usually very friendly, pleasant, and nice but he doesn't know anything about the computer itself. He'll send you on to what he calls the tech staff...
What people need is a one stop computer expert and that's practically impossible to find. Today what happens is that people go to a computer expert and they find that they can either go to an expert in hardware, in software, in sales, or support. The sales guy is usually very friendly, pleasant, and nice but he doesn't know anything about the computer itself. He'll send you on to what he calls the tech staff...
 More and more companies are beginning to understand the importance of expert search engine optimization in their overall marketing efforts. In reality, expert search engine optimization really is an ongoing process.
More and more companies are beginning to understand the importance of expert search engine optimization in their overall marketing efforts. In reality, expert search engine optimization really is an ongoing process. 
 Google Translate and other free Internet services for translating enable users to access a text on any language, and the product quality ranges from impressive to not intelligent. Internet connects the world, but most people are still separated with language barriers. That is why the mechanical translators like Google Translate, Microsoft Bing and Sistran are a bridge to other languages.
Google Translate and other free Internet services for translating enable users to access a text on any language, and the product quality ranges from impressive to not intelligent. Internet connects the world, but most people are still separated with language barriers. That is why the mechanical translators like Google Translate, Microsoft Bing and Sistran are a bridge to other languages.
 Open Source Ecology is a network of farmers, engineers, and supporters that for the last two years has been creating the Global Village Construction Set, The GVCS lowers the barriers to entry into farming, building, and manufacturing and can be seen as a life-size lego-like set of modular tools that can create entire economies, whether in rural Missouri, where the project was founded, in urban redevelopment, or in the developing world.
Open Source Ecology is a network of farmers, engineers, and supporters that for the last two years has been creating the Global Village Construction Set, The GVCS lowers the barriers to entry into farming, building, and manufacturing and can be seen as a life-size lego-like set of modular tools that can create entire economies, whether in rural Missouri, where the project was founded, in urban redevelopment, or in the developing world.
 Windows can be a tough patient sometimes, especially when it comes to doing some simple tasks. For example, take the association assigning, ie. connecting two installed programs with certain extensions. Instead of reducing the job to a double click with the mouse, the process often needs to be repeated over and over again, chasing program on the hard drive, and in some cases you are completely left without the help of the system(exotic extension).
Windows can be a tough patient sometimes, especially when it comes to doing some simple tasks. For example, take the association assigning, ie. connecting two installed programs with certain extensions. Instead of reducing the job to a double click with the mouse, the process often needs to be repeated over and over again, chasing program on the hard drive, and in some cases you are completely left without the help of the system(exotic extension).
 This setting will rearrange files on the hard drive when the computer is idle thus improving the performance of the system. The computer must be restarted before the changes take effect.
This setting will rearrange files on the hard drive when the computer is idle thus improving the performance of the system. The computer must be restarted before the changes take effect.
 Another brief overview of good computer house cleaning. Dont miss out this very fundamental article. It WILL go a long way. Just like dust and dirt can build up around the house, your computer will build a collection of bits and pieces of information that you need to clean up.
Another brief overview of good computer house cleaning. Dont miss out this very fundamental article. It WILL go a long way. Just like dust and dirt can build up around the house, your computer will build a collection of bits and pieces of information that you need to clean up.
 Oracle is one of the most popular commercial databases, and it is characterized by high reliability and speed. Oracle has released a free version of their server titled Oracle Database Express Edition. The current version is called 11, which has limitations in the form of maximum memory size of 1GB and one processor, but it is completely free and can be used for smaller projects, web applications, and more.
Oracle is one of the most popular commercial databases, and it is characterized by high reliability and speed. Oracle has released a free version of their server titled Oracle Database Express Edition. The current version is called 11, which has limitations in the form of maximum memory size of 1GB and one processor, but it is completely free and can be used for smaller projects, web applications, and more.
 This tutorial will show you how to make a somewhat complex procedural material that would work for some strange organic object with 3D Studio Max. To start, make a sphere, this will be the object we are using to test the material on. Next setup some lights around it so it gives even lighting and more interesting highlights. Also on the sphere add a displacement approx modifier and click on the high button in its rollout.
This tutorial will show you how to make a somewhat complex procedural material that would work for some strange organic object with 3D Studio Max. To start, make a sphere, this will be the object we are using to test the material on. Next setup some lights around it so it gives even lighting and more interesting highlights. Also on the sphere add a displacement approx modifier and click on the high button in its rollout.
 This will be most handy for anyone using any version of Outlook or Outlook express. You'll learn all the hotkeys, tips and tricks. Don't miss it.
This will be most handy for anyone using any version of Outlook or Outlook express. You'll learn all the hotkeys, tips and tricks. Don't miss it.
 In 2008, global economy saw the worst downturn in decades. Some even compared it to the "Great Depression" of 1930s. Millions all over the world lost their jobs and consequently their homes that they had on mortgage. It is believed that crisis spiraled through inability to repay the mortgage loans. US took the major hit of this slowdown and millions lost their means of livelihood. Big financial companies went bankrupt overnight leading to a large head count of jobless people in America. While all this was happening there were countries like India, China, and Philippines who were snapping up jobs generated inside the US borders.
In 2008, global economy saw the worst downturn in decades. Some even compared it to the "Great Depression" of 1930s. Millions all over the world lost their jobs and consequently their homes that they had on mortgage. It is believed that crisis spiraled through inability to repay the mortgage loans. US took the major hit of this slowdown and millions lost their means of livelihood. Big financial companies went bankrupt overnight leading to a large head count of jobless people in America. While all this was happening there were countries like India, China, and Philippines who were snapping up jobs generated inside the US borders.
 The future of the music industry relies on adding value - not on racking up lawsuits. All the P2P network users receive through their downloading is the music itself, in electronic form and perhaps the chance to download cover art which can be printed off in an unprofessional manner using a household printer.
The future of the music industry relies on adding value - not on racking up lawsuits. All the P2P network users receive through their downloading is the music itself, in electronic form and perhaps the chance to download cover art which can be printed off in an unprofessional manner using a household printer. 
 Parallelism has sometimes been viewed as a rare and exotic sub area of computing, interesting but of little relevance to the average programmer. A study of trends in applications, computer architecture, and networking shows that this view is no longer tenable. Parallelism is becoming ubiquitous, and parallel programming is becoming central to the programming enterprise. A parallel computer is a set of processors that are able to work cooperatively to solve a computational problem.
Parallelism has sometimes been viewed as a rare and exotic sub area of computing, interesting but of little relevance to the average programmer. A study of trends in applications, computer architecture, and networking shows that this view is no longer tenable. Parallelism is becoming ubiquitous, and parallel programming is becoming central to the programming enterprise. A parallel computer is a set of processors that are able to work cooperatively to solve a computational problem. 
 Each icon in the system tray represents a utility program that is currently running in your system. If you have a bunch of icons in your system tray, your system is a prime candidate for cleaning.
Each icon in the system tray represents a utility program that is currently running in your system. If you have a bunch of icons in your system tray, your system is a prime candidate for cleaning.
 With this tutorial you should start from if you are beginner at Pascal. It will take you from a low to a moderately high level of Pascal programming. Both C and Pascal are considered High Level Languages. They use English type statements that are converted to machine statements which are executed by computers. C and Pascal programs are simple text files containing program statements. As such, they are created using a text editor. This is called the source program
With this tutorial you should start from if you are beginner at Pascal. It will take you from a low to a moderately high level of Pascal programming. Both C and Pascal are considered High Level Languages. They use English type statements that are converted to machine statements which are executed by computers. C and Pascal programs are simple text files containing program statements. As such, they are created using a text editor. This is called the source program
 If we have valuable information or accounting info stored in excel and by chance if you come across a situation where you need to convert the rows to columns. then we can use the transpose functionality in Excel.
If we have valuable information or accounting info stored in excel and by chance if you come across a situation where you need to convert the rows to columns. then we can use the transpose functionality in Excel.
 Different Operating Systems use different characters as their path separator when specifying directory and file paths. Check out how and what is used in PERL on *nix.
Different Operating Systems use different characters as their path separator when specifying directory and file paths. Check out how and what is used in PERL on *nix.
 Unlike the CPU and hard-drive markets, which are dominated by a small number of manufacturers, the memory market is extremely competitive, with dozens of vendors selling modules produced by a wide variety of chipmakers.
Unlike the CPU and hard-drive markets, which are dominated by a small number of manufacturers, the memory market is extremely competitive, with dozens of vendors selling modules produced by a wide variety of chipmakers.

 After a few weeks from the release of the Penguin 3, here are some conclusions from which you can see where the biggest algorithm ranking changes have been made. Those conclusions where taken from Linkresearchtools (LST) in a study of cases on a sample of 100 sites (50 have passed bad, 50 have passed good). This is probably a reply to the growing occurrence of guest posting (guesting on other peoples blogs). The ones who will grow in the ranks of SEO are those who get to their links with the most quality, relevancy, and now speed!
After a few weeks from the release of the Penguin 3, here are some conclusions from which you can see where the biggest algorithm ranking changes have been made. Those conclusions where taken from Linkresearchtools (LST) in a study of cases on a sample of 100 sites (50 have passed bad, 50 have passed good). This is probably a reply to the growing occurrence of guest posting (guesting on other peoples blogs). The ones who will grow in the ranks of SEO are those who get to their links with the most quality, relevancy, and now speed!
 A simple as it gets and no bull $#!t perl tutorial. Explains the low downs of the language involving some realy important basic concepts. Perl is short for Practical Extraction and Report Language. It's a language that is available free over the Web, and it's used for a variety of things, from writing CGI scripts to assisting administrators in maintaining their systems.
A simple as it gets and no bull $#!t perl tutorial. Explains the low downs of the language involving some realy important basic concepts. Perl is short for Practical Extraction and Report Language. It's a language that is available free over the Web, and it's used for a variety of things, from writing CGI scripts to assisting administrators in maintaining their systems. 
 Phishing is the act of sending out emails, supposedly from a certain trusted party, in order to trick out of the recipient sensitive information such as usernames, passwords, banking details etc. To avoid becoming a victim of phishing, stay alert. Whenever you receive an email telling you that you need to enter sensitive information treat it with suspicion.
Phishing is the act of sending out emails, supposedly from a certain trusted party, in order to trick out of the recipient sensitive information such as usernames, passwords, banking details etc. To avoid becoming a victim of phishing, stay alert. Whenever you receive an email telling you that you need to enter sensitive information treat it with suspicion.
 The type of email scam in which an email is sent claiming to be an established enterprise like eBay, Citibank, PayPal, Amazon.com, etc in an attempt to scam the user into surrendering private information. The word phishing comes from the analogy that Internet scammers are using e-mail lures to fish for passwords and financial data from the sea of Internet users. The term was coined in 1996 by hackers who were stealing AOL Internet accounts by scamming passwords from unsuspecting AOL users.
The type of email scam in which an email is sent claiming to be an established enterprise like eBay, Citibank, PayPal, Amazon.com, etc in an attempt to scam the user into surrendering private information. The word phishing comes from the analogy that Internet scammers are using e-mail lures to fish for passwords and financial data from the sea of Internet users. The term was coined in 1996 by hackers who were stealing AOL Internet accounts by scamming passwords from unsuspecting AOL users. 
 This tutorial will step by step take you through creating a simple tiled background with Adobe Photoshop.
This tutorial will step by step take you through creating a simple tiled background with Adobe Photoshop. 
.jpg) A faster pace of life has imposed some new habits. Instead of reading books, it's easier and faster to watch a movie, long letters have been replaced by text messages ... The situation is similar with pictures.
A faster pace of life has imposed some new habits. Instead of reading books, it's easier and faster to watch a movie, long letters have been replaced by text messages ... The situation is similar with pictures. 
 Building web applications with membership management is one of the most frequent tasks that every programmer does. PHP's session-handling features, was first introduced in the 4.0 release. Read this small tutorial to learn more.
Building web applications with membership management is one of the most frequent tasks that every programmer does. PHP's session-handling features, was first introduced in the 4.0 release. Read this small tutorial to learn more.
 It covers all the basic in neat and clean manner. Its recommended for beginner and those that have just passed the beginners mark. Also good for those who want to brush up on the basics. Its intent was to make PHP welcoming for the beginners and not to make the whole intro sound too technical.
It covers all the basic in neat and clean manner. Its recommended for beginner and those that have just passed the beginners mark. Also good for those who want to brush up on the basics. Its intent was to make PHP welcoming for the beginners and not to make the whole intro sound too technical.
.jpg) In collective network topology it may happen that two users that are connected to opposite ends with a closer can not communicate because the digital signal is distorted over time and is not as recognizable. Therefore, a device is inserted that has two-way communication and performs restoration of digital signals.
In collective network topology it may happen that two users that are connected to opposite ends with a closer can not communicate because the digital signal is distorted over time and is not as recognizable. Therefore, a device is inserted that has two-way communication and performs restoration of digital signals.
 There are pros and cons to both types of email, POP3 and web based. Consider them before choosing how you will send and receive your correspondence. These accounts are called POP3 accounts. POP3 refers to the protocol or language your computer and the mail servers located at your ISP use to communicate with each other.
There are pros and cons to both types of email, POP3 and web based. Consider them before choosing how you will send and receive your correspondence. These accounts are called POP3 accounts. POP3 refers to the protocol or language your computer and the mail servers located at your ISP use to communicate with each other.
 There is not a computer that doesn't need a good cooler, especially when it is a portable model. This time we are talking about two Cooler Masters models meant for cooling portables. X-Lite is a smaller and weaker model, designed according to the other models from the X series. The name of the model is inspired by the cooler, while the Lite points to the more humble possibilities of this model.
There is not a computer that doesn't need a good cooler, especially when it is a portable model. This time we are talking about two Cooler Masters models meant for cooling portables. X-Lite is a smaller and weaker model, designed according to the other models from the X series. The name of the model is inspired by the cooler, while the Lite points to the more humble possibilities of this model.
 The first time HomePlug was created is in the year of 2001. That first version had a max speed of between 14 Mbps to 85 Mbps. But, this was just in theory and as we all know that is not very real.
The first time HomePlug was created is in the year of 2001. That first version had a max speed of between 14 Mbps to 85 Mbps. But, this was just in theory and as we all know that is not very real.
.jpg) The first advantage we are going to mention is the ease of cabling powerline networks to computers. Most common homes have a lot of power outlets, and they are usually present in every room so if you want to cable your computer to a powerline network is fast, simple and easy. The reach is also significantly higher and greater than with Wi-Fi networks.
The first advantage we are going to mention is the ease of cabling powerline networks to computers. Most common homes have a lot of power outlets, and they are usually present in every room so if you want to cable your computer to a powerline network is fast, simple and easy. The reach is also significantly higher and greater than with Wi-Fi networks.
 People are now finding it easier and better to keep more than one mobile phone, laptops, and various other gadgets more frequently. These devices are known for better and faster connectivity with the world around themselves. Besides faster connectivity, these devices are capable of meeting all other requirements for the modern life.
People are now finding it easier and better to keep more than one mobile phone, laptops, and various other gadgets more frequently. These devices are known for better and faster connectivity with the world around themselves. Besides faster connectivity, these devices are capable of meeting all other requirements for the modern life.
 Who needs another shell? Unlike the Unix world, Windows hasbeen pretty consistent with the shell environment. First there was MS-DOS (COMMAND.COM) and later Windows NT (CMD.EXE). You can actually still get to COMMAND.COM if you really, really want to. But for all intents and purposes, these have been the only two shells Windows users have ever known.
Who needs another shell? Unlike the Unix world, Windows hasbeen pretty consistent with the shell environment. First there was MS-DOS (COMMAND.COM) and later Windows NT (CMD.EXE). You can actually still get to COMMAND.COM if you really, really want to. But for all intents and purposes, these have been the only two shells Windows users have ever known.
Microsoft wants to change that. When .Net was announced in 2000, Microsoft promised everything would one day be .Net. Unfortunately, Microsoft stuck the .Net name on things that were not .Net at all, such as Passport.Net which had no managed code in it at all.

 This tutorial was a long time coming. It teaches the readers in a very simple and down to earth language how to create a batch file to backup your various files. Also pushes the readers to think outside the tutorial and to figure out more ways to make the given commands even better. I suggest that anyone trying to learn Batch Scripting reads this. It will not be a waste of time, I promise.
This tutorial was a long time coming. It teaches the readers in a very simple and down to earth language how to create a batch file to backup your various files. Also pushes the readers to think outside the tutorial and to figure out more ways to make the given commands even better. I suggest that anyone trying to learn Batch Scripting reads this. It will not be a waste of time, I promise.
 Now we have all heard of various ways to help our PC to avoid viruses. Well this is article is no exception. But it does point out a couple of things that you dont usually hear discussed.
Now we have all heard of various ways to help our PC to avoid viruses. Well this is article is no exception. But it does point out a couple of things that you dont usually hear discussed.
 Spyware can be installed without the conscious consent of the user, allowing unsolicited spam or remote monitoring of a computer's activity. Neither spyware or adware can be removed using a normal Antivirus program.
Spyware can be installed without the conscious consent of the user, allowing unsolicited spam or remote monitoring of a computer's activity. Neither spyware or adware can be removed using a normal Antivirus program.
 Very often, the people who first recognize the potential benefits of professional SEO are not the key decision makers. They are the people on the front lines of the organization, the ones who deal with prospects and customers every day. While different marketing decision makers can have different hot button issues, few things seem to motivate companies as much as the action (or sometimes the inaction) of the competition.
Very often, the people who first recognize the potential benefits of professional SEO are not the key decision makers. They are the people on the front lines of the organization, the ones who deal with prospects and customers every day. While different marketing decision makers can have different hot button issues, few things seem to motivate companies as much as the action (or sometimes the inaction) of the competition.
 You should always avoid buying network gear at the full retail cost. You need to stop yourself from buying a product that has just been released to the market, instead you should wait a month or two months after it has been released because that is usually when vendors offer discounts or rebates.
You should always avoid buying network gear at the full retail cost. You need to stop yourself from buying a product that has just been released to the market, instead you should wait a month or two months after it has been released because that is usually when vendors offer discounts or rebates.
 This is probably the second best Python tutorial on the web. Why second best you ask? Simple because www.python.org has already done such a wonderfull job on their tutorial. But if you want to get your hands dirty from the start, you may want to take a whack out our Python tutorial thats assembled for the beginners.
This is probably the second best Python tutorial on the web. Why second best you ask? Simple because www.python.org has already done such a wonderfull job on their tutorial. But if you want to get your hands dirty from the start, you may want to take a whack out our Python tutorial thats assembled for the beginners.
 QBasic is a very simple language to pick up, and yet it can accomplish a great deal. Granted you will probably never write Doom or Word Perfect with QBasic, but it has its strong points. One of them is to introduce people to programming without having to worry about the internal workings of the computer. It's simple to create games, business applications, simple databases, and graphics. The best aspect of the language is its close resemblance to English.
QBasic is a very simple language to pick up, and yet it can accomplish a great deal. Granted you will probably never write Doom or Word Perfect with QBasic, but it has its strong points. One of them is to introduce people to programming without having to worry about the internal workings of the computer. It's simple to create games, business applications, simple databases, and graphics. The best aspect of the language is its close resemblance to English.
 Today it is just impossible to not have a BitTorrent client installed on the OS, because this way of downloading files is very popular. So, next to choosing audio and video players it is important to choose the right BitTorrent client. When it comes to Windows OS the main torrent is �Torrent. It has been the inspiration to the creator of qBittorrent to create an alternative to open code.
Today it is just impossible to not have a BitTorrent client installed on the OS, because this way of downloading files is very popular. So, next to choosing audio and video players it is important to choose the right BitTorrent client. When it comes to Windows OS the main torrent is �Torrent. It has been the inspiration to the creator of qBittorrent to create an alternative to open code.
 This very fast QtWebKit Internet Browser has the goal of being light and available on all dominant platforms. The project was started for educational purposes, but today it has grown into a quality program. Considering that it is still young, QupZilla can't be found in the GNU/Linux distribution treasury.
This very fast QtWebKit Internet Browser has the goal of being light and available on all dominant platforms. The project was started for educational purposes, but today it has grown into a quality program. Considering that it is still young, QupZilla can't be found in the GNU/Linux distribution treasury.
 This is a perfect tutorial about shading, Variation, and Detail in graphics relating to MAYA mostly.
This is a perfect tutorial about shading, Variation, and Detail in graphics relating to MAYA mostly.
 All of us who are regular users of computers eventually come to the point where we replace what we are using with a new machine. We are then faced with the question of what to do with the old system. Here is some ways to make sure that good use is made of whatever potential is left in the old computer.
All of us who are regular users of computers eventually come to the point where we replace what we are using with a new machine. We are then faced with the question of what to do with the old system. Here is some ways to make sure that good use is made of whatever potential is left in the old computer.
 When you start the program you will see the familiar speed dial that is called Favorites here, and it is with a few predefined pages. Adding new pages in the Favorites section is very easy, as is their changing and deleting. Next to that, on the home screen are shortcuts for entering Bookmarks, the Downloads section, History as well as the display of tabs you recently closed. After you get into rekonq settings you will...
When you start the program you will see the familiar speed dial that is called Favorites here, and it is with a few predefined pages. Adding new pages in the Favorites section is very easy, as is their changing and deleting. Next to that, on the home screen are shortcuts for entering Bookmarks, the Downloads section, History as well as the display of tabs you recently closed. After you get into rekonq settings you will...
 Some people thought that the whole notion of terminal services is a bit to technical for them to understand. Well, MicroSoft and our good friends that work for Bill Boy Gates have come out with terminal services, changed the name and made it a whole lot easier to understand. Find out how!
Some people thought that the whole notion of terminal services is a bit to technical for them to understand. Well, MicroSoft and our good friends that work for Bill Boy Gates have come out with terminal services, changed the name and made it a whole lot easier to understand. Find out how!
 Have you ever had that eye sore (Links Folder) that just wouldn't delete from your favorites list in IE browser? Or maybe, you delete it and it comes back the next time your computer turns on? Then this tutorial is for you!
Have you ever had that eye sore (Links Folder) that just wouldn't delete from your favorites list in IE browser? Or maybe, you delete it and it comes back the next time your computer turns on? Then this tutorial is for you!
 Have you ever gone to a site, and so many pop-ups appear that you feel like your going to explode? Well you need "Remove Spyware Software"
Have you ever gone to a site, and so many pop-ups appear that you feel like your going to explode? Well you need "Remove Spyware Software"
 Yesterday my dad complained that after installing something so and so, ICQ toolbar came into affect in Firefox browser. Not only that but it also took over as his default search engine. Being the household certified tech-geek, it came down upon me to find a solution.
Yesterday my dad complained that after installing something so and so, ICQ toolbar came into affect in Firefox browser. Not only that but it also took over as his default search engine. Being the household certified tech-geek, it came down upon me to find a solution.
 This quick article will explain how to remove folder/file on a Windows machine that have no name and therefore are a pain in the rear end to delete, rename, or drag.
This quick article will explain how to remove folder/file on a Windows machine that have no name and therefore are a pain in the rear end to delete, rename, or drag.
 Ever got annoyed with Windows Messenger Icon in your system tray? Well we'll show you how to take this bad boy out of your PC quickly. Windows Messenger is a Swiss Army Knife sort of program: Instant messenger, video conferencer, file transferer, shared whiteboard, voice chat.
Ever got annoyed with Windows Messenger Icon in your system tray? Well we'll show you how to take this bad boy out of your PC quickly. Windows Messenger is a Swiss Army Knife sort of program: Instant messenger, video conferencer, file transferer, shared whiteboard, voice chat.
 Users have accepted portable computers a long time ago for doing their work outside of their workplace. In most of tests the Asus Transformer Pad Infinity TF700T is one of the most powerful tablets on the market. The Android 4.0 Ice Cream Sandwich operating system allows working with multiple applications at the same time, and it supports Adobe Flash and the increasingly popular Google play. Even though it is got 32/64 GB memory for saving data, extra space for making backup copies is always welcome. By buying this computer you get the ASUS WebStorage service, that enables lifetime using of 8GB online space in a "cloud". You also get the Polaris Office package that can help ...
Users have accepted portable computers a long time ago for doing their work outside of their workplace. In most of tests the Asus Transformer Pad Infinity TF700T is one of the most powerful tablets on the market. The Android 4.0 Ice Cream Sandwich operating system allows working with multiple applications at the same time, and it supports Adobe Flash and the increasingly popular Google play. Even though it is got 32/64 GB memory for saving data, extra space for making backup copies is always welcome. By buying this computer you get the ASUS WebStorage service, that enables lifetime using of 8GB online space in a "cloud". You also get the Polaris Office package that can help ...
 Kaspersky Internet Security 2013 was one of only four antivirus products that have amazed analysts from an independent organization for testing IT safety solutions, MRG Effitas, in that they did, during the test that was recently done, blocked all attempts to steal financial information.
Kaspersky Internet Security 2013 was one of only four antivirus products that have amazed analysts from an independent organization for testing IT safety solutions, MRG Effitas, in that they did, during the test that was recently done, blocked all attempts to steal financial information.
 Rightmove and Zoopla have both released iPhone applications which let you access all their tools while on the move. These free apps aim to give house hunters an advantage when out looking for their dream home. In this new competitive arena we see which app comes out best.
Rightmove and Zoopla have both released iPhone applications which let you access all their tools while on the move. These free apps aim to give house hunters an advantage when out looking for their dream home. In this new competitive arena we see which app comes out best.
 A rootkit is a program that allows attackers to obtain manager entry to a system. On Unix/Linux system, this is known as "root" accessibility. Rootkits contain resources and value that help assailants(attackers) cover up their existence as well as give the enemy full control of the hosting server or customer device consistently without being observed. Sometimes they even cause common viruses type problems. I had a case where a web browser hijack was being brought on by a particular rootkit set up on the program. In this article, I will show you one way to eliminate a Rootkit from a Windows program.
A rootkit is a program that allows attackers to obtain manager entry to a system. On Unix/Linux system, this is known as "root" accessibility. Rootkits contain resources and value that help assailants(attackers) cover up their existence as well as give the enemy full control of the hosting server or customer device consistently without being observed. Sometimes they even cause common viruses type problems. I had a case where a web browser hijack was being brought on by a particular rootkit set up on the program. In this article, I will show you one way to eliminate a Rootkit from a Windows program.
 If you see someone who is wishing to do a reset on their home router there might be a lot of reasons for them to do it. The most common things are forgetting the admin password, forgetting the Wi-Fi security key and also troubleshooting problems with connection.
If you see someone who is wishing to do a reset on their home router there might be a lot of reasons for them to do it. The most common things are forgetting the admin password, forgetting the Wi-Fi security key and also troubleshooting problems with connection.
 Samsung free global service for communication now offers access to multiple screens and other upgrading that make text sharing more fulfilling and interesting. ChatON has simplified texting for millions of users world wide enabling them to enjoy easy interaction with everyone and in any format. The ChatON 2.0 service now goes a step further because it enables users to access it from multiple devices that will supply them with a unique customer experience.
Samsung free global service for communication now offers access to multiple screens and other upgrading that make text sharing more fulfilling and interesting. ChatON has simplified texting for millions of users world wide enabling them to enjoy easy interaction with everyone and in any format. The ChatON 2.0 service now goes a step further because it enables users to access it from multiple devices that will supply them with a unique customer experience.
 Samsung has finally refreshed the series 9, a new ultrabook NP900X3E is not a replacement of the old models, but it will sell with them. The lighting of the screen is larger than 300 cd/m2 so this ultrabook can be used outside in the sunlight, and the resolution is full HD. The only flaw is that the screen is not touch sensitive.
Samsung has finally refreshed the series 9, a new ultrabook NP900X3E is not a replacement of the old models, but it will sell with them. The lighting of the screen is larger than 300 cd/m2 so this ultrabook can be used outside in the sunlight, and the resolution is full HD. The only flaw is that the screen is not touch sensitive.
 As far as technology is concerned updates and upgrades are a daily affair. Web development is not an exception to this trend. With many advanced software carving niches for themselves in the field of web development we can see a radical change in the way websites are created these days. Flash has proven to be one of the most important and effective tools in web development.
As far as technology is concerned updates and upgrades are a daily affair. Web development is not an exception to this trend. With many advanced software carving niches for themselves in the field of web development we can see a radical change in the way websites are created these days. Flash has proven to be one of the most important and effective tools in web development.
 The basic idea is simply to create lots of pages on your site(s) and embed links pointing back to your most important target pages. This works because a link pointing at a page on your site -- your home page, for instance -- enhances that page whether it is coming from outside or inside your site.
The basic idea is simply to create lots of pages on your site(s) and embed links pointing back to your most important target pages. This works because a link pointing at a page on your site -- your home page, for instance -- enhances that page whether it is coming from outside or inside your site.
 This is something that our friend Najmi came up with for the beginners. Have trouble finding things on the net? Well, read this and become a whiz at looking things up online.
This is something that our friend Najmi came up with for the beginners. Have trouble finding things on the net? Well, read this and become a whiz at looking things up online.
 Today you're going to learn how to make a simple "operating system" using batch tutorial. You'll learn about the following commands and features: echo, cls, choice, if, errorlevels, and labels. Once you've finished, you will have a batch file that can show a few different menus, enter into the menus and display the options contain within, and let the user pick the option they want. The example we are going to use is going to let the user choose which game they want to play.
Today you're going to learn how to make a simple "operating system" using batch tutorial. You'll learn about the following commands and features: echo, cls, choice, if, errorlevels, and labels. Once you've finished, you will have a batch file that can show a few different menus, enter into the menus and display the options contain within, and let the user pick the option they want. The example we are going to use is going to let the user choose which game they want to play.
 You can never be careful enough with the people that surround you and that may see something on your computer that they shouldn't. It probably happened to you that your boss suddenly enters your office and you are doing something you shouldn't. If you can, set your screen so it is available only to your eyes.
You can never be careful enough with the people that surround you and that may see something on your computer that they shouldn't. It probably happened to you that your boss suddenly enters your office and you are doing something you shouldn't. If you can, set your screen so it is available only to your eyes.

 The Internet is a useful place, but unfortunately it can also be quite dangerous. Just how do you know what is safe and what you should stay away from? This article gets right down to the point with some practical tips on avoiding a few tricks, so that you don't end up inconvenienced, annoyed, or devastated.
The Internet is a useful place, but unfortunately it can also be quite dangerous. Just how do you know what is safe and what you should stay away from? This article gets right down to the point with some practical tips on avoiding a few tricks, so that you don't end up inconvenienced, annoyed, or devastated.
 If you are looking for career counseling, and are in a dilemma as which branch of computer science you should go for, this small section would hopefully help you in selecting the best option according to your nature and interest. In computer industry, there are several branches from which you can choose any one. The reason behind this is that in this industry, you can get success and/or fame only when you are skilled, and full of knowledge.
If you are looking for career counseling, and are in a dilemma as which branch of computer science you should go for, this small section would hopefully help you in selecting the best option according to your nature and interest. In computer industry, there are several branches from which you can choose any one. The reason behind this is that in this industry, you can get success and/or fame only when you are skilled, and full of knowledge.
 Just as we teach our children the difference between a "good touch" and a "bad touch," we need to teach PC users the difference between a good assist and a bad assist. A good assist is help from a qualified computer expert to solve a real problem. A bad assist is help from a well intentioned friend to solve a problem that frequently doesn't even exist. Some bad assists are harmless, but some precipitate computer disasters.
Just as we teach our children the difference between a "good touch" and a "bad touch," we need to teach PC users the difference between a good assist and a bad assist. A good assist is help from a qualified computer expert to solve a real problem. A bad assist is help from a well intentioned friend to solve a problem that frequently doesn't even exist. Some bad assists are harmless, but some precipitate computer disasters.
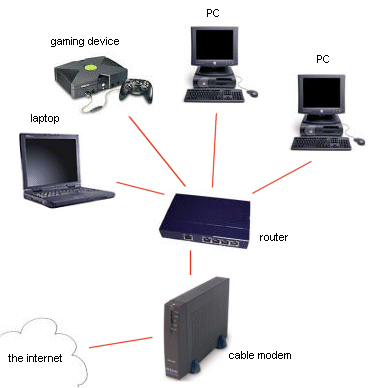 This is an article about setting up home networks. It will help you if you trying to set up a home network. Once you know what type of network you want and you have the necessary hardware, there are four possible steps you can take.
This is an article about setting up home networks. It will help you if you trying to set up a home network. Once you know what type of network you want and you have the necessary hardware, there are four possible steps you can take.
 When you first connect to the network, you will be asked whether you want to include sharing among computers and connect to network devices such as printers. Depending on the answers automatically it sets the appropriate firewall settings and security settings for the type of network you are connecting to. Sharing can be turned on or off at any time.
When you first connect to the network, you will be asked whether you want to include sharing among computers and connect to network devices such as printers. Depending on the answers automatically it sets the appropriate firewall settings and security settings for the type of network you are connecting to. Sharing can be turned on or off at any time.
 If your computer has a wireless (Wi-Fi) network adapter, you will see the wireless network icon when you click on the Settings button. In order to function, the wireless adapter standard must be equal to or older than the wireless router standard. For example, if the AC adapter in the computer is using a wireless 802.11n (also known as Wireless-N), but the router uses 802.11g (also known as Wireless-G), you will not be able to connect because the Wireless-G standard is an older version and does not recognize the Wireless-N.
If your computer has a wireless (Wi-Fi) network adapter, you will see the wireless network icon when you click on the Settings button. In order to function, the wireless adapter standard must be equal to or older than the wireless router standard. For example, if the AC adapter in the computer is using a wireless 802.11n (also known as Wireless-N), but the router uses 802.11g (also known as Wireless-G), you will not be able to connect because the Wireless-G standard is an older version and does not recognize the Wireless-N.
 We at TW were browsing about the web when we stumbled upon Mark's work. Although it's much outdated, it's very fundamental. And please don't let the title fool you. This is not a small short article but a short OS introductory book. An operating system is a layer of software which takes care of technical aspects of a computer's operation. It shields the user of the machine from the low-level details of the machine's operation and provides frequently needed facilities
We at TW were browsing about the web when we stumbled upon Mark's work. Although it's much outdated, it's very fundamental. And please don't let the title fool you. This is not a small short article but a short OS introductory book. An operating system is a layer of software which takes care of technical aspects of a computer's operation. It shields the user of the machine from the low-level details of the machine's operation and provides frequently needed facilities
 Some products persist on the market for a long time, a few years or a few decades (Rolls Royce)... Consumers get to love them so much that the manufacturers have to make new versions every once in a while to make them stay modern. But, some gadgets live the life of a butterfly, after a few months they get pulled from the market, although they could have ended up different.
Some products persist on the market for a long time, a few years or a few decades (Rolls Royce)... Consumers get to love them so much that the manufacturers have to make new versions every once in a while to make them stay modern. But, some gadgets live the life of a butterfly, after a few months they get pulled from the market, although they could have ended up different. 
 It is not uncommon that Internet connections stay on all the time, which makes you online all day long. People usually leave their router or other network devices on for a very long time, even when they don't need them. But, is this a good or bad thing? Should you keep your network on all the time or not?
It is not uncommon that Internet connections stay on all the time, which makes you online all day long. People usually leave their router or other network devices on for a very long time, even when they don't need them. But, is this a good or bad thing? Should you keep your network on all the time or not?
 Colors play an important role in human lives. Unlike animals, we see and interpret colors of different hues, shades, tints and spectrum. Emotions are attached to different colors ; phrases have been coined around them. Sample a few: Seeing Red, Going Green With Envy, Having The Blues, In The Pink Of Health, Green Thumb.
Colors play an important role in human lives. Unlike animals, we see and interpret colors of different hues, shades, tints and spectrum. Emotions are attached to different colors ; phrases have been coined around them. Sample a few: Seeing Red, Going Green With Envy, Having The Blues, In The Pink Of Health, Green Thumb.Since we are surrounded by colors in real life, it is but logical that it make the transition to the virtual world.

 This is a tutorial on how to make a silk material out of just procedural maps with 3D Studio Max.
This is a tutorial on how to make a silk material out of just procedural maps with 3D Studio Max.
 This tutorial gets right down to the grease of loading and saving text in flash.
This tutorial gets right down to the grease of loading and saving text in flash.

It is amazing to look at all that has transpired in technology in relatively a blink of an eye. In a span of 71 years, about as long as many baby boomers have been alive, computers have gone from huge devices that took an entire room to one that can sit on your lap while you update your Facebook page. In more recent years, we have seen the birth and awkward infancy of , also known as the sixth generation of computers.

 In short, SixthSense Technology allows a person access to data at will. It's much different than using your iPhone! Many who aren't much aware of the technology hear the description and try to think of it as a new gadgetry that connects us to the web like iPhone, or your other cell phones or mini laptops. Wrong!!!
In short, SixthSense Technology allows a person access to data at will. It's much different than using your iPhone! Many who aren't much aware of the technology hear the description and try to think of it as a new gadgetry that connects us to the web like iPhone, or your other cell phones or mini laptops. Wrong!!!
 When you mention social media the first thing that comes to mind is Facebook or Twitter, and maybe even Instagram. These services are really massive and have a steady growths in user numbers, but they are not the only ones.
When you mention social media the first thing that comes to mind is Facebook or Twitter, and maybe even Instagram. These services are really massive and have a steady growths in user numbers, but they are not the only ones.
 For many users of Twitter the common practice is to "tweet" on the social network while watching TV, but now for the first time it is confirmed the assumption that "tweeting" may increase the ratings of a show.
For many users of Twitter the common practice is to "tweet" on the social network while watching TV, but now for the first time it is confirmed the assumption that "tweeting" may increase the ratings of a show.
 There are four fundamental phases in most, if not all, software engineering methodologies. These phases are analysis, design, implementation, and testing. These phases address what is to be built, how it will be built, building it, and making it high quality. . These steps together define the cradle-to-grave life cycle of the software project. Obviously, if an action is done many times, it needs to be done correctly and efficiently.
There are four fundamental phases in most, if not all, software engineering methodologies. These phases are analysis, design, implementation, and testing. These phases address what is to be built, how it will be built, building it, and making it high quality. . These steps together define the cradle-to-grave life cycle of the software project. Obviously, if an action is done many times, it needs to be done correctly and efficiently.
.jpg) A brief intoduction into the world of Spamming. Read to find out the only methods known to work in fighting spam emails.
A brief intoduction into the world of Spamming. Read to find out the only methods known to work in fighting spam emails.

 Microcomerc is one of the rare, if not the only one that offers solutions that cover everything about managing and storing documents. Their solution, the Spider, does cover everything there is to cover in managing documents just like a spider with it's web. Things like software, hardware, scanning services, microfilming and storing information. Our point of focus will be the Spider.NET software for managing documents.
Microcomerc is one of the rare, if not the only one that offers solutions that cover everything about managing and storing documents. Their solution, the Spider, does cover everything there is to cover in managing documents just like a spider with it's web. Things like software, hardware, scanning services, microfilming and storing information. Our point of focus will be the Spider.NET software for managing documents.
.jpg) After a great deal of popular demand, TechiWarehouse presents SQL tutorial. As with almost all of our tutorials (with some exception), this tutorial too has been put into one single file for easy printing. This tutorial is concetrated in generality. In other words, it is meant to cover almost all things without getting into some very hardcore details. Yet, its detailed enough to get a newbie up and running in no time with SQL. Again, the focus is for readers to be able to learn SQL and be able to put thier own theories to test by the end of the tutorial and not rely on yet other tutorials as such.
After a great deal of popular demand, TechiWarehouse presents SQL tutorial. As with almost all of our tutorials (with some exception), this tutorial too has been put into one single file for easy printing. This tutorial is concetrated in generality. In other words, it is meant to cover almost all things without getting into some very hardcore details. Yet, its detailed enough to get a newbie up and running in no time with SQL. Again, the focus is for readers to be able to learn SQL and be able to put thier own theories to test by the end of the tutorial and not rely on yet other tutorials as such.
 Here is something that no network or web developing professional should ignore. SSL is has already become the widely accepted. Read the full article to understand the intricacies and the nitty gritty of SSL. SSL comes in two strengths, 40-bit and 128-bit, which refer to the length of the "session key" generated by every encrypted transaction
Here is something that no network or web developing professional should ignore. SSL is has already become the widely accepted. Read the full article to understand the intricacies and the nitty gritty of SSL. SSL comes in two strengths, 40-bit and 128-bit, which refer to the length of the "session key" generated by every encrypted transaction
 Often-told story of Cisco's launch leaves out the drama and intrigue...Founding legends are a specialty of Silicon Valley, and none is more appealing than that of Cisco Systems: i/In the 1980s a young Stanford University couple invent the multiprotocol router and starts Cisco in their living room, using their own credit cards for financing.
Often-told story of Cisco's launch leaves out the drama and intrigue...Founding legends are a specialty of Silicon Valley, and none is more appealing than that of Cisco Systems: i/In the 1980s a young Stanford University couple invent the multiprotocol router and starts Cisco in their living room, using their own credit cards for financing.
 This week, we have again somehow got hold of these pearls of wisdom on running a successful Internet Biz. It is important that you go through this article if there is even a remote chance of you opening up an Internet Business. After all, millions have tried it, only hundreds have succeeded. There has got to something that most people are doing wrong.
This week, we have again somehow got hold of these pearls of wisdom on running a successful Internet Biz. It is important that you go through this article if there is even a remote chance of you opening up an Internet Business. After all, millions have tried it, only hundreds have succeeded. There has got to something that most people are doing wrong.
 There is a possibility that when you are using Wi-Fi, it doesn't matter if it is your home or a public place where you use it, sudden drops of connection occur. Unfortunately, it is not very rare. But there are things you can do that can help with this problem and you can see them below.
There is a possibility that when you are using Wi-Fi, it doesn't matter if it is your home or a public place where you use it, sudden drops of connection occur. Unfortunately, it is not very rare. But there are things you can do that can help with this problem and you can see them below.

 The concern and debate about the ethical issues of a third party tracking and selling PC users online habits is not new in the Internet age. Yet the debate on personal Internet privacy is dramatically heating up in 2010 and gaining worldwide attention from civic and governmental organizations around the globe. The impetus for renewed focus on standardized levels of consumer online privacy is largely fueled by new technologies in cookie tracking tools that is garnering a name for itself in some industry circles as "super cookies."
The concern and debate about the ethical issues of a third party tracking and selling PC users online habits is not new in the Internet age. Yet the debate on personal Internet privacy is dramatically heating up in 2010 and gaining worldwide attention from civic and governmental organizations around the globe. The impetus for renewed focus on standardized levels of consumer online privacy is largely fueled by new technologies in cookie tracking tools that is garnering a name for itself in some industry circles as "super cookies."
 ... we haven't seen a better copy protection anywhere else than with SwarShala 3.0. The system only works when you email the company with a certain number that the program pops up. They in return will email back the key to run the program in a normal full version mode. Now the reason this software will do well in it's copy right protection is because the software is in itself so unheard of that no one has come up with a crack program for it. Trust Me, We Know! We Looked Around! :)
... we haven't seen a better copy protection anywhere else than with SwarShala 3.0. The system only works when you email the company with a certain number that the program pops up. They in return will email back the key to run the program in a normal full version mode. Now the reason this software will do well in it's copy right protection is because the software is in itself so unheard of that no one has come up with a crack program for it. Trust Me, We Know! We Looked Around! :)
 The online world today can be a scary place. The presence of the Internet in everyday life has brought with it the emergence of malicious activities, which are steadily increasing. Online shoppers, users of the portal for electronic payments and transactions and any other services that include the exchange of confidential or personal data are reasonably concerned.
The online world today can be a scary place. The presence of the Internet in everyday life has brought with it the emergence of malicious activities, which are steadily increasing. Online shoppers, users of the portal for electronic payments and transactions and any other services that include the exchange of confidential or personal data are reasonably concerned.
 Have you ever wondered what the difference between a folder and a directory is? Or did you ever try to find the folder "Control Panel" on your hard drive and wondered where it was? The answers lie in understanding a little bit about system folders.
Have you ever wondered what the difference between a folder and a directory is? Or did you ever try to find the folder "Control Panel" on your hard drive and wondered where it was? The answers lie in understanding a little bit about system folders.
 This Article/Tutorial will show you step by step how villian on the web try to hack into everyday PC's. Learn what you can do to protect yourself as well.
This Article/Tutorial will show you step by step how villian on the web try to hack into everyday PC's. Learn what you can do to protect yourself as well.
 The Task Coach is a program from a group of personal to do managers. Next to the standard options of organizing and informing you about upcoming tasks, it offers advanced possibilities of manipulation of tasks and managing the available time.
The Task Coach is a program from a group of personal to do managers. Next to the standard options of organizing and informing you about upcoming tasks, it offers advanced possibilities of manipulation of tasks and managing the available time.
 This Tcl/Tk tutorial is probably one of the few tutorials that cover Tcl and Tk in the most broadest range. A perfect tutorial for newbies. TCL/TK is a programming system developed by John Ousterhout at the University of California, Berkeley, which is easy to use, and which has very useful graphical interface facilities. TCL is the basic programming language, while TK is a ToolKit of widgets, which are graphical objects similar to those of other GUI toolkits, such as Xlib, Xview and Motif.
This Tcl/Tk tutorial is probably one of the few tutorials that cover Tcl and Tk in the most broadest range. A perfect tutorial for newbies. TCL/TK is a programming system developed by John Ousterhout at the University of California, Berkeley, which is easy to use, and which has very useful graphical interface facilities. TCL is the basic programming language, while TK is a ToolKit of widgets, which are graphical objects similar to those of other GUI toolkits, such as Xlib, Xview and Motif. 
 These are set of commandments set forth by the God of C. Same set of rules that were revealed on the Mt. ANSI. Learn them well for they shall set you free.
These are set of commandments set forth by the God of C. Same set of rules that were revealed on the Mt. ANSI. Learn them well for they shall set you free.
 One of the things you might not realize when you're thinking about Perl and hearing about Perl is that there is an awful lot of disinformation out there, and it's really hard for someone who's not very familiar with Perl to separate the wheat from the chaff, and it's very easy to accept some of these things as gospel truth - sometimes without even realising it. What I'm going to do, then, is to pick out the top ten myths that you'll hear bandied around, and give a response to them. I'm not going to try to persuade you to use Perl - the only way for you to know if it's for you is to get on and try it - but hopefully I can let you see that not all of what you hear is true.
One of the things you might not realize when you're thinking about Perl and hearing about Perl is that there is an awful lot of disinformation out there, and it's really hard for someone who's not very familiar with Perl to separate the wheat from the chaff, and it's very easy to accept some of these things as gospel truth - sometimes without even realising it. What I'm going to do, then, is to pick out the top ten myths that you'll hear bandied around, and give a response to them. I'm not going to try to persuade you to use Perl - the only way for you to know if it's for you is to get on and try it - but hopefully I can let you see that not all of what you hear is true.
 A VPN (virtual private network) gives you the possibility to encrypt every bit of traffic that goes through your network (it doesn't matter if it is going in our out).
A VPN (virtual private network) gives you the possibility to encrypt every bit of traffic that goes through your network (it doesn't matter if it is going in our out).
 This is a very short but very thought provoking fictitious story about a script kiddie who become a real hacker. And so the budding hacker asked some computer people he knew how to learn more about computers. They advised him to try building his own computer by putting parts together.
This is a very short but very thought provoking fictitious story about a script kiddie who become a real hacker. And so the budding hacker asked some computer people he knew how to learn more about computers. They advised him to try building his own computer by putting parts together.
 This week you're going to learn the continuation of the second batch tutorial, which demonstrated how to make a simple operating system using batch files. If you are running Windows XP, some of the commands shown in this tutorial will not work. You will need to work through this tutorial on a computer running Windows 98 or plain DOS.
This week you're going to learn the continuation of the second batch tutorial, which demonstrated how to make a simple operating system using batch files. If you are running Windows XP, some of the commands shown in this tutorial will not work. You will need to work through this tutorial on a computer running Windows 98 or plain DOS.
 Software consultants are very high in demand these days and they are extremely required in the development companies as a contractor and the consultants. These software consultants solve the problems of many organizations with the given time period and without spending any extra expenditures on the employees. They are able to work on full time basis or at the part time as well. The software consulting may prove good for you if you wanted to be an entrepreneur and passionate about your software and finally want to gain success in your field.
Software consultants are very high in demand these days and they are extremely required in the development companies as a contractor and the consultants. These software consultants solve the problems of many organizations with the given time period and without spending any extra expenditures on the employees. They are able to work on full time basis or at the part time as well. The software consulting may prove good for you if you wanted to be an entrepreneur and passionate about your software and finally want to gain success in your field.
 The key advantage of DSL over modem is speed. DSL is from several, to dozens, of times faster than a modem connection. Connection speed, reliability, and the 'always-on' nature of DSL, are the main reasons it is so popular. For small businesses, DSL is also a great way to save money compared to pay per minute ISDN service, or expensive T1 lines.
The key advantage of DSL over modem is speed. DSL is from several, to dozens, of times faster than a modem connection. Connection speed, reliability, and the 'always-on' nature of DSL, are the main reasons it is so popular. For small businesses, DSL is also a great way to save money compared to pay per minute ISDN service, or expensive T1 lines.
 Every new software or operating system that comes out in the market houses a lot of technical glitches and annoyances. Some can be fixed easily and others cannot be. And Windows Vista is not an exception. In fact, this new operating system has been facing serious criticism for a long time now for many features of it that a lot of people consider to be highly annoying. Many software and computer geeks have tried their level best to bring about effective solutions for the various annoyances present in Vista. Let us catch hold of a few cyber remedies for these binary dis-eases. ;)
Every new software or operating system that comes out in the market houses a lot of technical glitches and annoyances. Some can be fixed easily and others cannot be. And Windows Vista is not an exception. In fact, this new operating system has been facing serious criticism for a long time now for many features of it that a lot of people consider to be highly annoying. Many software and computer geeks have tried their level best to bring about effective solutions for the various annoyances present in Vista. Let us catch hold of a few cyber remedies for these binary dis-eases. ;)
 Let's take some time to focus on one of the MOST used softwares in the computer world. It's strange how we use something so often and not think twice on fixing some of our pet peeves or kinks that we face which we weren't meant to in the first place. If we compare the amount of work we get done with Microsoft Word, it probably comes in a close third after our Operating System and our Internet Browser.
Let's take some time to focus on one of the MOST used softwares in the computer world. It's strange how we use something so often and not think twice on fixing some of our pet peeves or kinks that we face which we weren't meant to in the first place. If we compare the amount of work we get done with Microsoft Word, it probably comes in a close third after our Operating System and our Internet Browser.
So let's get right down to it.


 A special kind of domain extensions is called TLD or top level domains. It is common to see both names when you surf the web. In order to get a grasp of these domains you should learn something more about normal domains on the Internet.
A special kind of domain extensions is called TLD or top level domains. It is common to see both names when you surf the web. In order to get a grasp of these domains you should learn something more about normal domains on the Internet.
 What eventually became one of the most significant advantages of the Internet is the possibility of simple access to any information placed on any computer attached to this global network. We can access the information that we need in various ways, from searching on the Web, to downloading complete files, even the ones that are pretty large. This text should help the enlightening of the dilemma about downloading files from the Internet and to give you short instructions on how to do it.
What eventually became one of the most significant advantages of the Internet is the possibility of simple access to any information placed on any computer attached to this global network. We can access the information that we need in various ways, from searching on the Web, to downloading complete files, even the ones that are pretty large. This text should help the enlightening of the dilemma about downloading files from the Internet and to give you short instructions on how to do it.
 The model we've tested comes to us from the Japanese manufacturer Toshiba and brings some interesting but also odd solutions for the balance of performance and functionality. The LX830-108 is placed in thickened monitor case with a diagonal of 23 inches using components designed for portable computers.
The model we've tested comes to us from the Japanese manufacturer Toshiba and brings some interesting but also odd solutions for the balance of performance and functionality. The LX830-108 is placed in thickened monitor case with a diagonal of 23 inches using components designed for portable computers.
 If we start the story with a 14.4" diagonal screen, you probably expect another light business Ultrabook. It is light, with only 1.7 kg, but the expanded format of the screen will surprise you. Namely, it's resolution is 1792x768 pixels, so the aspect rose from the usually 16:9 (1.78:1) to 21:9 (2.33:1), and all of that just to make the Toshiba U840W an excellent platform to watch movies. on.
If we start the story with a 14.4" diagonal screen, you probably expect another light business Ultrabook. It is light, with only 1.7 kg, but the expanded format of the screen will surprise you. Namely, it's resolution is 1792x768 pixels, so the aspect rose from the usually 16:9 (1.78:1) to 21:9 (2.33:1), and all of that just to make the Toshiba U840W an excellent platform to watch movies. on.
 A good view on how to convert your LPs and Audio Tapes to CD format. This system of conversion has come in extremely handy for people who want to keep alive old records. Essentially begin with as good quality an audio signal as you can manage ie. new stylus for records, clean your tape heads or whatever as the better the inital recording is the better your result
A good view on how to convert your LPs and Audio Tapes to CD format. This system of conversion has come in extremely handy for people who want to keep alive old records. Essentially begin with as good quality an audio signal as you can manage ie. new stylus for records, clean your tape heads or whatever as the better the inital recording is the better your result
 In our studies we have found that Trojans are primarily responsible for almost all Windows Based machines being compromised. Find out more in this weeks article.
In our studies we have found that Trojans are primarily responsible for almost all Windows Based machines being compromised. Find out more in this weeks article.
.png) Communication via e-mail, even though it is one of the oldest services on the Internet, is not loosing lose it's intensity and popularity. On the contrary, the development of new opportunities for the use of this service does not fade over the years, so the older POP and SMTP accounts and the Internet service providers are slowly being replaced by the IMAP protocol and orders which do not depend on which way you access the Internet device.
Communication via e-mail, even though it is one of the oldest services on the Internet, is not loosing lose it's intensity and popularity. On the contrary, the development of new opportunities for the use of this service does not fade over the years, so the older POP and SMTP accounts and the Internet service providers are slowly being replaced by the IMAP protocol and orders which do not depend on which way you access the Internet device.
 Computers have delicate electronics inside of them. The electronics in laptops may be even more delicate. As the computer ages, the components suffer from repeatedly being turned on and off (technicians say that the parts are fried). Over the course of time, the repeated spiking damages some components. It is thus a good idea to reduce the number of times that you spike these delicate parts.
Computers have delicate electronics inside of them. The electronics in laptops may be even more delicate. As the computer ages, the components suffer from repeatedly being turned on and off (technicians say that the parts are fried). Over the course of time, the repeated spiking damages some components. It is thus a good idea to reduce the number of times that you spike these delicate parts.

 I think we hit the mother-load of server security information in this article people. We urge, every server admin as well as those looking to get into server and network security to not miss out on this article. You may already be experiencing attacks and wouldn't even know. And we like to point out that this article has no views against the "White-Hat Hacking Community."
I think we hit the mother-load of server security information in this article people. We urge, every server admin as well as those looking to get into server and network security to not miss out on this article. You may already be experiencing attacks and wouldn't even know. And we like to point out that this article has no views against the "White-Hat Hacking Community." 
 What types of computer crimes do you and your company have to look out for? How do you avoid these criminals? Because computers are found in just about every home and office now, criminals are becoming smarter.
What types of computer crimes do you and your company have to look out for? How do you avoid these criminals? Because computers are found in just about every home and office now, criminals are becoming smarter. 
 Upgradation is not something new. The computer has come a long way from being just a calculating machine to a device that has become a necessity everywhere. There is no industry or business that can't benefit from the usage of computers. Whether it's a managed server used for dedicated server hosting, personal desktop computers, or just your student friendly notebook computers. First generation computers made use of magnetic core memory whereas second generation saw the advent of transistors. It was in the third generation which began in the 1960s that gave rise to microprocessors.
Upgradation is not something new. The computer has come a long way from being just a calculating machine to a device that has become a necessity everywhere. There is no industry or business that can't benefit from the usage of computers. Whether it's a managed server used for dedicated server hosting, personal desktop computers, or just your student friendly notebook computers. First generation computers made use of magnetic core memory whereas second generation saw the advent of transistors. It was in the third generation which began in the 1960s that gave rise to microprocessors.
.jpg) Computer cases come in a variety of colors, designs, materials and for those who wish to bare all, there are clear acrylic cases available. You'll hear of all types of hardware lingo like: ATX computer cases, full tower computer cases, desktop computer cases, custom computer cases, aluminum computer cases, cheap computer cases, gaming computer cases, mini computer cases, and on and on and on...you get the drift.
Computer cases come in a variety of colors, designs, materials and for those who wish to bare all, there are clear acrylic cases available. You'll hear of all types of hardware lingo like: ATX computer cases, full tower computer cases, desktop computer cases, custom computer cases, aluminum computer cases, cheap computer cases, gaming computer cases, mini computer cases, and on and on and on...you get the drift.
 Ever wonder what types of things servers take part in? Ever wonder the possibilities? Well read all about it here in this weeks article. A good 10 minutes reading for all you future potential system admins. Servers are often dedicated, meaning that they perform no other tasks besides their server tasks.
Ever wonder what types of things servers take part in? Ever wonder the possibilities? Well read all about it here in this weeks article. A good 10 minutes reading for all you future potential system admins. Servers are often dedicated, meaning that they perform no other tasks besides their server tasks.
 One of most important type of server is cluster servers. Software that enables clustering of servers is installed into a computer. Clustering servers also serve as load balancing servers between two computers. This is a common small business server. Clustering servers are used to avoid server failover. Server failover is the capability to shift to another standby server if the main server fails.
One of most important type of server is cluster servers. Software that enables clustering of servers is installed into a computer. Clustering servers also serve as load balancing servers between two computers. This is a common small business server. Clustering servers are used to avoid server failover. Server failover is the capability to shift to another standby server if the main server fails.
 Most people think of Linux as something only for geeks and computer power users. However, we have come to see various flavors of LinuxOS being sold in major retail stores in the last few years and we also see a trend being set online. In this article, we're simply going to single out only one of many Linux flavors known as Ubuntu.
Most people think of Linux as something only for geeks and computer power users. However, we have come to see various flavors of LinuxOS being sold in major retail stores in the last few years and we also see a trend being set online. In this article, we're simply going to single out only one of many Linux flavors known as Ubuntu.
 So you think your PC's sound system is pretty slick? If you're a high-end PC user, you probably have a 5.1-channel speaker system and a discrete sound card capable of 24-bit audio sampling, a 100 dB signal to noise ratio, and 96-KHz audio playback. While those specifications are impressive, they don't hold a candle to the absolute best PC audio configuration you can get.
So you think your PC's sound system is pretty slick? If you're a high-end PC user, you probably have a 5.1-channel speaker system and a discrete sound card capable of 24-bit audio sampling, a 100 dB signal to noise ratio, and 96-KHz audio playback. While those specifications are impressive, they don't hold a candle to the absolute best PC audio configuration you can get.
 Network hubs were the central devices that network administrators used to use to establish a network setup using Star Topologies. Network hubs had multiple RJ-45 ports integrated in them and were used to connect one end of the LAN cables that had RJ-45 connectors crimped to them. The other end of the cables were connected to the RJ-45 ports available on the PCs. Network hubs were available with 4, 8, 16 and 24 ports. Administrators also used to cascade two hubs for larger network setups. Cascading means that one RJ-45 port of one hub connected to ...
Network hubs were the central devices that network administrators used to use to establish a network setup using Star Topologies. Network hubs had multiple RJ-45 ports integrated in them and were used to connect one end of the LAN cables that had RJ-45 connectors crimped to them. The other end of the cables were connected to the RJ-45 ports available on the PCs. Network hubs were available with 4, 8, 16 and 24 ports. Administrators also used to cascade two hubs for larger network setups. Cascading means that one RJ-45 port of one hub connected to ...
 n a nutshell, network topologies are the physical alignments of computers and the way they are connected to each other. For example, if all the computers are connected to each other via a central device (Hub or Switch), the type of topology is Star. Likewise, if all the computers are connected to each other via a main cable, this means it is Bus Topology.
n a nutshell, network topologies are the physical alignments of computers and the way they are connected to each other. For example, if all the computers are connected to each other via a central device (Hub or Switch), the type of topology is Star. Likewise, if all the computers are connected to each other via a main cable, this means it is Bus Topology.
 In computer networks, scope (area) up to where data that is transferred over the cables or the wireless media with certain conditions is categorized in two domain main types. In complex network setups, because multiple segments are connected to each other via different types of central devices, it becomes important for the administrators to separate broadcast domains and reduce the numbers of collision domains. A central device in which collisions may occur is Hub because of it logical Bus Topology.
In computer networks, scope (area) up to where data that is transferred over the cables or the wireless media with certain conditions is categorized in two domain main types. In complex network setups, because multiple segments are connected to each other via different types of central devices, it becomes important for the administrators to separate broadcast domains and reduce the numbers of collision domains. A central device in which collisions may occur is Hub because of it logical Bus Topology.
 In small-scale organizations and home environments, DHCP servers are installed normally and no class oriented configurations are done. The reason behind this is that by default all DHCP client computers belong to default DHCP class and as soon as DHCP scopes are configured and the DHCP servers become ready to assign dynamic addresses to the client computers, the DHCP clients start receiving the IP addresses without any additional administrative overheads. However, in order to allow DHCP servers to assign different ...
In small-scale organizations and home environments, DHCP servers are installed normally and no class oriented configurations are done. The reason behind this is that by default all DHCP client computers belong to default DHCP class and as soon as DHCP scopes are configured and the DHCP servers become ready to assign dynamic addresses to the client computers, the DHCP clients start receiving the IP addresses without any additional administrative overheads. However, in order to allow DHCP servers to assign different ...
 Dynamic Host Configuration Protocol or DHCP servers are the dedicated computers that have network operating systems installed on them and are responsible for providing automatic IP addresses to all the client computers that are configured to obtain the addresses automatically.
Dynamic Host Configuration Protocol or DHCP servers are the dedicated computers that have network operating systems installed on them and are responsible for providing automatic IP addresses to all the client computers that are configured to obtain the addresses automatically.
 Domain Name System or DNS servers are dedicated computers that have network operating systems installed on them and are responsible for resolving hostnames (computer names) to their IP addresses and vice versa. DNS servers are used worldwide and are helpful while accessing the Internet and visiting websites. Every Internet Service Provider or ISP has its own DNS server which receives name resolution requests from the subscribers of that ISP and resolves the requested host names to their corresponding IP addresses.
Domain Name System or DNS servers are dedicated computers that have network operating systems installed on them and are responsible for resolving hostnames (computer names) to their IP addresses and vice versa. DNS servers are used worldwide and are helpful while accessing the Internet and visiting websites. Every Internet Service Provider or ISP has its own DNS server which receives name resolution requests from the subscribers of that ISP and resolves the requested host names to their corresponding IP addresses.
 DNS records are the objects that are created either manually by the DNS administrators or automatically by the DNS servers themselves. A DNS server can have indefinite numbers of records and each DNS record is helpful in resolving the query of its own type. For example a Host (A) record in DNS server helps resolving a hostname to its corresponding IPv4 address whereas Host (AAAA) record resolves hostname to its corresponding IPv6 addresses.
DNS records are the objects that are created either manually by the DNS administrators or automatically by the DNS servers themselves. A DNS server can have indefinite numbers of records and each DNS record is helpful in resolving the query of its own type. For example a Host (A) record in DNS server helps resolving a hostname to its corresponding IPv4 address whereas Host (AAAA) record resolves hostname to its corresponding IPv6 addresses.
 When a DNS server role is installed on a network operating system, by default forward lookup zone is automatically created and the DNS server works as Caching Only server that caches the results of all the queries that it resolves. Forward lookup zone of a DNS server resolves IP addresses to their corresponding host names, is used in most network setups in production environments.
When a DNS server role is installed on a network operating system, by default forward lookup zone is automatically created and the DNS server works as Caching Only server that caches the results of all the queries that it resolves. Forward lookup zone of a DNS server resolves IP addresses to their corresponding host names, is used in most network setups in production environments.

 LAN Bridges were used to separate and isolate multiple collision domains from each other in large broadcast domains. Bridges had two or more LAN ports to which other central devices, such as network Hubs, were connected via LAN cables. Unlike network Hubs that used to forward data packets to every PC that was connected to the ports, Bridges acted more like LAN Switches to identify destination ports and transferred the data packets only if the packets were destined to reach the segments that were connected to their other ends. Bridges used to calculate and identify the destination segments on the basis of physical (MAC) addresses of the central devices that were connected to their LAN ports.
LAN Bridges were used to separate and isolate multiple collision domains from each other in large broadcast domains. Bridges had two or more LAN ports to which other central devices, such as network Hubs, were connected via LAN cables. Unlike network Hubs that used to forward data packets to every PC that was connected to the ports, Bridges acted more like LAN Switches to identify destination ports and transferred the data packets only if the packets were destined to reach the segments that were connected to their other ends. Bridges used to calculate and identify the destination segments on the basis of physical (MAC) addresses of the central devices that were connected to their LAN ports.
 LAN switches, which are also sometimes called intelligent hubs, are the networking devices that have completely dominated and replaced Hubs. The reason behind this is that unlike Hubs, that only used to regenerate the received packets and forward them to all the ports that they had, LAN switches create one-to-one virtual circuits directly to the ports to which the destination computers are connected. This reduces the time consumed while transferring the data packets from the source computers to the destination ones.
LAN switches, which are also sometimes called intelligent hubs, are the networking devices that have completely dominated and replaced Hubs. The reason behind this is that unlike Hubs, that only used to regenerate the received packets and forward them to all the ports that they had, LAN switches create one-to-one virtual circuits directly to the ports to which the destination computers are connected. This reduces the time consumed while transferring the data packets from the source computers to the destination ones.
 Apart from star topology that is widely used in almost every network environment, the other type of topology that is complex while setting up but provides 100% fault tolerance to the network is Mesh Topology. In this topology, every computer that has to be connected to the network is connected to every computer that is available in the network. For example if there are four computers namely A, B, C and D, then A will be connected to B, C and D. Likewise B will be connected to A, C and D and so on. This means that when mesh topology is used while establishing a network setup, it is very unlikely that the network would ever face congestions or would ever fail.
Apart from star topology that is widely used in almost every network environment, the other type of topology that is complex while setting up but provides 100% fault tolerance to the network is Mesh Topology. In this topology, every computer that has to be connected to the network is connected to every computer that is available in the network. For example if there are four computers namely A, B, C and D, then A will be connected to B, C and D. Likewise B will be connected to A, C and D and so on. This means that when mesh topology is used while establishing a network setup, it is very unlikely that the network would ever face congestions or would ever fail.
 This article is mainly to provide beginners of PHP a bit more background into the language then just a bunch of codes. A bit more history, a bit more discussion on the version and syntax of PHP.
This article is mainly to provide beginners of PHP a bit more background into the language then just a bunch of codes. A bit more history, a bit more discussion on the version and syntax of PHP.
 In ring topology, data used to transfer in the form of ring where every computer that was connected to the network had two LAN cards and each LAN card was connected to the LAN card of its neighbor computer. Many times ring topology was preferred over bus topology because there were no collisions and the chances of network getting congested were next to 0%.
In ring topology, data used to transfer in the form of ring where every computer that was connected to the network had two LAN cards and each LAN card was connected to the LAN card of its neighbor computer. Many times ring topology was preferred over bus topology because there were no collisions and the chances of network getting congested were next to 0%.
 Routers are the devices that are used to connect two different networks in order to allow communication between them. Networks with different network IDs are considered to be different. By default, no communication can take place between two different networks, and this configuration prevents computers of one network from getting accessed by the computers on the other network, which may belong to another organization, building premises, home, etc.
Routers are the devices that are used to connect two different networks in order to allow communication between them. Networks with different network IDs are considered to be different. By default, no communication can take place between two different networks, and this configuration prevents computers of one network from getting accessed by the computers on the other network, which may belong to another organization, building premises, home, etc.
 Since over a decade, star topologies have been preferred over bus topologies by the administrators. In star topology, a central device (Hub or Switch) is used to connect multiple PCs in a local area network. Central devices that are used in star topologies have multiple LAN ports integrated in them and the PCs are connected to the central devices via patch cables. In most cases patch cables are twisted pair cables that have four twisted pairs (eight wires in all) which are crimped to the RJ-45 connectors. The reason why star topology is mostly preferred nowadays is that it does not provide a single point of failure and is highly scalable. This means ...
Since over a decade, star topologies have been preferred over bus topologies by the administrators. In star topology, a central device (Hub or Switch) is used to connect multiple PCs in a local area network. Central devices that are used in star topologies have multiple LAN ports integrated in them and the PCs are connected to the central devices via patch cables. In most cases patch cables are twisted pair cables that have four twisted pairs (eight wires in all) which are crimped to the RJ-45 connectors. The reason why star topology is mostly preferred nowadays is that it does not provide a single point of failure and is highly scalable. This means ...
 Learn all about the Windows Registry in this free tutorial from TechiWarehouse.Com. Making changes to the Registry is a lot easier than you think provided you take the sensible precautions outlined in this article.
Learn all about the Windows Registry in this free tutorial from TechiWarehouse.Com. Making changes to the Registry is a lot easier than you think provided you take the sensible precautions outlined in this article.
 Virtualization is a process in which a physical computer a.k.a. host computer contains virtual machines that are stored in them in form of files. These virtual machines act exactly the way the physical computers do and can be mapped with the NICs of the host computers. Once mapped, the operating systems installed inside the virtual machines (Guest Operating Systems) can then communicate with the host computers as well as the network setups to which the host computers might be connected.
Virtualization is a process in which a physical computer a.k.a. host computer contains virtual machines that are stored in them in form of files. These virtual machines act exactly the way the physical computers do and can be mapped with the NICs of the host computers. Once mapped, the operating systems installed inside the virtual machines (Guest Operating Systems) can then communicate with the host computers as well as the network setups to which the host computers might be connected.
 In any network setup, network topology plays an important role without which network cannot be established whatsoever. In other words, whenever two or more machines are connected to each other, a topology is automatically formed. Unlike wired networks that have multiple topologies, wireless networks have only two topologies namely Infrastructure and Ad Hoc. Since wireless networks work on unguided media, it makes sense to have limited number of topologies while configuring the wireless network setups. Moreover, since wireless networks are a bit complicated configure as compared to the wired networks, it is essential for the administrators to have ...
In any network setup, network topology plays an important role without which network cannot be established whatsoever. In other words, whenever two or more machines are connected to each other, a topology is automatically formed. Unlike wired networks that have multiple topologies, wireless networks have only two topologies namely Infrastructure and Ad Hoc. Since wireless networks work on unguided media, it makes sense to have limited number of topologies while configuring the wireless network setups. Moreover, since wireless networks are a bit complicated configure as compared to the wired networks, it is essential for the administrators to have ...
 Caution: This tutorial is HUGE. Please allow ample time to load.
Caution: This tutorial is HUGE. Please allow ample time to load.If you are coming to unix for the first time, from a Windows or MacIntosh environment, be prepared for a rather different culture than the one you are used to. UNIX is not about `products' and off-the-shelf software, it is about open standards, free software and the ability to change just about everything.

 Learn how to insert, modify, and delete entries in a database table with mySQL. Occasionally, it becomes necessary to change the attributes of one of the variables or columns in a table. This is a frequent situation for a variable that might be declared VARCHAR(20) lets say, and then the user wants to add something that might be 25 characters in length.
Learn how to insert, modify, and delete entries in a database table with mySQL. Occasionally, it becomes necessary to change the attributes of one of the variables or columns in a table. This is a frequent situation for a variable that might be declared VARCHAR(20) lets say, and then the user wants to add something that might be 25 characters in length.
 A USB flash memory is mostly used as a transferring device for the most varied types of devices. Somebody stores on them program, somebody music, and there are those that use a flash only to transfer documents, images, videos...
A USB flash memory is mostly used as a transferring device for the most varied types of devices. Somebody stores on them program, somebody music, and there are those that use a flash only to transfer documents, images, videos...
 The Internet has revolutionized the way business is done, but what happens when the Internet fails? In that case you can use several alternatives such as Wireless Internet or you can go to the nearest Internet cafe. But, there is a third alternative when the Internet crashes, your old mobile phone. In the following text you will find instructions that describe the way to turn your old mobile phone into a modem.
The Internet has revolutionized the way business is done, but what happens when the Internet fails? In that case you can use several alternatives such as Wireless Internet or you can go to the nearest Internet cafe. But, there is a third alternative when the Internet crashes, your old mobile phone. In the following text you will find instructions that describe the way to turn your old mobile phone into a modem.
 Like the title, this tutorial teaches you how to create a cookie. What does a cookie do and why do you need it. Now-a-days most of the websites use cookies to store small amounts of information. Websites can read the values from the cookies and use the information as desired.
Like the title, this tutorial teaches you how to create a cookie. What does a cookie do and why do you need it. Now-a-days most of the websites use cookies to store small amounts of information. Websites can read the values from the cookies and use the information as desired.
 Although they are not directly executable as programs, the many DLL files present in Windows contain libraries of functions that are used throughout the operating system and in application software. Generally, these functions areused internally by programs and are not directly visible to the computer user. However, Windows XP contains a file rundll32 that allows command line access to certain functions that are explicitly written to be available to this executable file.In this article we discuss how to use some of these.
Although they are not directly executable as programs, the many DLL files present in Windows contain libraries of functions that are used throughout the operating system and in application software. Generally, these functions areused internally by programs and are not directly visible to the computer user. However, Windows XP contains a file rundll32 that allows command line access to certain functions that are explicitly written to be available to this executable file.In this article we discuss how to use some of these.
 You get to work on a Monday morning, and realise that you've left the document you were presenting today back at home on your computer. How do you get it? Or maybe you have a friend that has problems with their computer, and you know how to fix it, but only if you can see it. There could be many more situations where you need to use a particular computer and you're not there. Enter the range of programs known as VNC.
You get to work on a Monday morning, and realise that you've left the document you were presenting today back at home on your computer. How do you get it? Or maybe you have a friend that has problems with their computer, and you know how to fix it, but only if you can see it. There could be many more situations where you need to use a particular computer and you're not there. Enter the range of programs known as VNC.
 Here is a beginner tutorial that we thought could come handy to those that have just purchased a PC (Today haha). Just kidding! But seriously, if you have programs on your computer and don't have a clue how to take them out, try this tutorial. It's exactly for a person like yourself.
Here is a beginner tutorial that we thought could come handy to those that have just purchased a PC (Today haha). Just kidding! But seriously, if you have programs on your computer and don't have a clue how to take them out, try this tutorial. It's exactly for a person like yourself.
 If you are using the Internet, and you are (unless you have been hiding under a rock for the past 15 years), you have to know something about the various kinds of connections that exist. Down below you can see them listed.
If you are using the Internet, and you are (unless you have been hiding under a rock for the past 15 years), you have to know something about the various kinds of connections that exist. Down below you can see them listed.
 VBA was introduced in Excel 5. Before that version Excel used a completely different macro system, known as XML (Excel Macro language). VBA is an exceptionally strong program language that has hundreds of uses. The following list is just a example of what you can do with the help of VBA macros.
VBA was introduced in Excel 5. Before that version Excel used a completely different macro system, known as XML (Excel Macro language). VBA is an exceptionally strong program language that has hundreds of uses. The following list is just a example of what you can do with the help of VBA macros.
 The magazine "Nature" interviewed six leading world experts from the area of neuropsychology and stated their opinions in an article called "Brains about video games". We should say that these are not the people who give their private opinion, but experts that study this area for a long time, with the goal to prove or to disprove the hypothesis and wide spread stereotypes about video games. They asked to point the positive effects of video games first. They all agreed that video games can help in developing some qualities, but only in healthy people.
The magazine "Nature" interviewed six leading world experts from the area of neuropsychology and stated their opinions in an article called "Brains about video games". We should say that these are not the people who give their private opinion, but experts that study this area for a long time, with the goal to prove or to disprove the hypothesis and wide spread stereotypes about video games. They asked to point the positive effects of video games first. They all agreed that video games can help in developing some qualities, but only in healthy people.
 Early studies have shown that excessive use of Internet (and video games as well) caused some social behavior changes, increased aggression, isolation, lack of attention and depressive behavior. New studies not only confirm the alleged issues, but widen the list with several serious disorders that are linked with heavy addiction. A few psychiatric diagnoses such as depressive neurosis, bipolar psychosis, attention disorder, hyperactivity and anxious neurosis.
Early studies have shown that excessive use of Internet (and video games as well) caused some social behavior changes, increased aggression, isolation, lack of attention and depressive behavior. New studies not only confirm the alleged issues, but widen the list with several serious disorders that are linked with heavy addiction. A few psychiatric diagnoses such as depressive neurosis, bipolar psychosis, attention disorder, hyperactivity and anxious neurosis.
 "My son wants to become a video-game programmer or designer. What advice do you have?" - This is a very common question. Particularly with video games, kids really enjoy playing them, and are often drawn to the potential of creating them as well. There's even a series of TV commercials that play on exactly that scenario. I've hired a lot of programmers in my career. I've also not hired even more. So I definitely have some thoughts and advice.
"My son wants to become a video-game programmer or designer. What advice do you have?" - This is a very common question. Particularly with video games, kids really enjoy playing them, and are often drawn to the potential of creating them as well. There's even a series of TV commercials that play on exactly that scenario. I've hired a lot of programmers in my career. I've also not hired even more. So I definitely have some thoughts and advice.
 All computers have a Central Processing Unit (CPU) in which contains Core Processing Chips that allow the CPU to run your programs. In the beginning, a desktop computer had a chip contained transistors that let the CPU run one process at a time. As time went on, newer Core Processors were developed that split the chip into two, four or up to 16 cores on one Core Processor, allowing the CPU to run more than one process at a time. This greatly increased the processing time of the computer.
All computers have a Central Processing Unit (CPU) in which contains Core Processing Chips that allow the CPU to run your programs. In the beginning, a desktop computer had a chip contained transistors that let the CPU run one process at a time. As time went on, newer Core Processors were developed that split the chip into two, four or up to 16 cores on one Core Processor, allowing the CPU to run more than one process at a time. This greatly increased the processing time of the computer.
 Numerous tech-savvy people have been in the process of boosting the performance of Windows Vista. The number of tweaking software aimed at fine tuning the working of Vista has been on the rise for a long time now. Apart from tweaking software there are many other built-in methods to make your Vista OS faster, cooler and more efficient. Let's have a look at a few such tweaks that would help you know Vista better and handle it more effectively.
Numerous tech-savvy people have been in the process of boosting the performance of Windows Vista. The number of tweaking software aimed at fine tuning the working of Vista has been on the rise for a long time now. Apart from tweaking software there are many other built-in methods to make your Vista OS faster, cooler and more efficient. Let's have a look at a few such tweaks that would help you know Vista better and handle it more effectively.
 What is wrong with the Alt+Tab routine in Windows? Nothing! Especially if you are using Vista or Windows 7. On a blurred background you get a neatly displayed windows of active programs together with fitting thumbnails and names.
What is wrong with the Alt+Tab routine in Windows? Nothing! Especially if you are using Vista or Windows 7. On a blurred background you get a neatly displayed windows of active programs together with fitting thumbnails and names. 
 This Visual Basic tutorial is the very much requested by TechiWarehouse. It'll will be enough to get a beginner up and making VB codes and programs. Although, it will need some time and dedication as with any other tutorial. VISUAL BASIC is one of the easiest programming tool to master. With some basic guidance, anybody could come up with a nice little windows-based program within a short time, age is not the limit.
This Visual Basic tutorial is the very much requested by TechiWarehouse. It'll will be enough to get a beginner up and making VB codes and programs. Although, it will need some time and dedication as with any other tutorial. VISUAL BASIC is one of the easiest programming tool to master. With some basic guidance, anybody could come up with a nice little windows-based program within a short time, age is not the limit. 
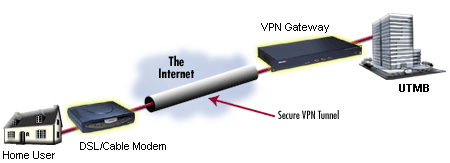 There are two kinds of tunneling that Virtual Private Networks support and they are called compulsory and voluntary. They are equally being used, as in none is more popular than the other.
There are two kinds of tunneling that Virtual Private Networks support and they are called compulsory and voluntary. They are equally being used, as in none is more popular than the other.
 This VRML tutorial will give the newcomers a head start with VRML. Starting with the history and basics, this tutorial will guide you to a point where with a little effort, even new comers will be able to create a decent VRML structure all on their own. Not only is this a recommended tutorial on VRML but (in our best hypothesis) with a good understanding of VRMl, it is easier to learn more advanced concepts of general programming. It is highly recommended that all who are interested in advancing in VRML at-least skim through this particular tutorial.
This VRML tutorial will give the newcomers a head start with VRML. Starting with the history and basics, this tutorial will guide you to a point where with a little effort, even new comers will be able to create a decent VRML structure all on their own. Not only is this a recommended tutorial on VRML but (in our best hypothesis) with a good understanding of VRMl, it is easier to learn more advanced concepts of general programming. It is highly recommended that all who are interested in advancing in VRML at-least skim through this particular tutorial.
 Mobile Internet is all present today through phones and tablets, and all operators have a solid offer of packages for computers too. The connection is established through a USB modem that, judging by the instructions, works only on Windows and rarely on Mac.
Mobile Internet is all present today through phones and tablets, and all operators have a solid offer of packages for computers too. The connection is established through a USB modem that, judging by the instructions, works only on Windows and rarely on Mac.
.jpg) Instead of cabling 2 computers directly, they can be connected in an indirect way through what is called a central network fixture. The central network fixture needs 2 network cables, and each one should connect one computer to the fixture. There are a few types of fixtures that exist and are used for home networking. See article for more info...
Instead of cabling 2 computers directly, they can be connected in an indirect way through what is called a central network fixture. The central network fixture needs 2 network cables, and each one should connect one computer to the fixture. There are a few types of fixtures that exist and are used for home networking. See article for more info...
 Asus VivoBook S200 is standardly delivered with the Windows 8 Pro 64-bit system, and the big touchpad responds perfectly to motion control in the Metro interface. The biggest surprise waits at the display: it is a very good 11,6" screen with LED background lighting that - responds to touch. Just like it was predicted, controlling the Windows 8 system is...
Asus VivoBook S200 is standardly delivered with the Windows 8 Pro 64-bit system, and the big touchpad responds perfectly to motion control in the Metro interface. The biggest surprise waits at the display: it is a very good 11,6" screen with LED background lighting that - responds to touch. Just like it was predicted, controlling the Windows 8 system is...
.jpg) This article describes some of the issues at play in structuring and negotiating Web development and hosting agreements.
This article describes some of the issues at play in structuring and negotiating Web development and hosting agreements.As a threshold issue, we must define our terms. Web development and hosting relationships encompass a broad range of substantive relationships, and it is crucial that the substantive relationships be kept separate to ensure proper analysis.

 Most of the times you'll hear web hosting companies promote their services as some cheap solution for a site that may have scalable needs. This is a fancy way of saying they believe you're website will one day require tremendous amount of hosting resources because they have all the faith in its success. We'll I don’t want to say that we don’t have the faith, but maybe the promoting web hosting service can be done for a "host" of other reasons as well.
Most of the times you'll hear web hosting companies promote their services as some cheap solution for a site that may have scalable needs. This is a fancy way of saying they believe you're website will one day require tremendous amount of hosting resources because they have all the faith in its success. We'll I don’t want to say that we don’t have the faith, but maybe the promoting web hosting service can be done for a "host" of other reasons as well.
 Many times these errors have more to do with the Web servers you're trying to access rather than something being wrong with your computer. Here is a list of error messages you might encounter while surfing the Web and their respective meanings to help you figure out just what the problem is. Here is a list of error messages you might encounter while surfing the Web and their respective meanings to help you figure out just what the problem is.
Many times these errors have more to do with the Web servers you're trying to access rather than something being wrong with your computer. Here is a list of error messages you might encounter while surfing the Web and their respective meanings to help you figure out just what the problem is. Here is a list of error messages you might encounter while surfing the Web and their respective meanings to help you figure out just what the problem is.


 In the world of computers, networking is the practice of linking two or more computing devices together for the exchange of data. Networks are built with a mix of computer hardware and software.
In the world of computers, networking is the practice of linking two or more computing devices together for the exchange of data. Networks are built with a mix of computer hardware and software.
 Internet access usually needs people who use it to subscribe to it to be able to connect to it. Next to the normal use policies, these terms also have a limit set on the use of the Internet connection over some amount of time. The limits are usually known by the name data plans.
Internet access usually needs people who use it to subscribe to it to be able to connect to it. Next to the normal use policies, these terms also have a limit set on the use of the Internet connection over some amount of time. The limits are usually known by the name data plans. 
 A special type of network device is called the hub and can be found in many home and small business networks. Although they have been around for many years, the popularity of the hub has recently exploded, especially among people relatively new to networking. Do you have a hub, or are considering buying one ? This article explains the purpose of the hub and some of the technology behind it.
A special type of network device is called the hub and can be found in many home and small business networks. Although they have been around for many years, the popularity of the hub has recently exploded, especially among people relatively new to networking. Do you have a hub, or are considering buying one ? This article explains the purpose of the hub and some of the technology behind it.
 The way that computers work is that they use something called an Operating System, basically a platform in the form of a low level software which enables programers and other people to make other, more complex programs. A common misconception is that OS (operating system) software runs only on computers, but the truth is that it runs on phones, routers and other network devices.
The way that computers work is that they use something called an Operating System, basically a platform in the form of a low level software which enables programers and other people to make other, more complex programs. A common misconception is that OS (operating system) software runs only on computers, but the truth is that it runs on phones, routers and other network devices.
 There are home networks, corporate intranets, and Internet Service Providers (ISPs) that use proxy servers (also known as proxies). Proxy servers act as a "middleman" between the two ends of a client/server network connection. Proxy servers work with Web browsers and servers, or other applications, by supporting underlying network protocols like HTTP.
There are home networks, corporate intranets, and Internet Service Providers (ISPs) that use proxy servers (also known as proxies). Proxy servers act as a "middleman" between the two ends of a client/server network connection. Proxy servers work with Web browsers and servers, or other applications, by supporting underlying network protocols like HTTP.
 IP and TCP networks use routing tables in order to determine where the messages they forward should go. If you look at the routing table itself, it is a database, very small, and the thing that controls it is the software and hardware that is in the router.
IP and TCP networks use routing tables in order to determine where the messages they forward should go. If you look at the routing table itself, it is a database, very small, and the thing that controls it is the software and hardware that is in the router.
 If you own a business, and you use the services of a certified bookkeeper, maybe it is the right time for you to introduce some new things into your business and in that way save money and time. By using an accountant software you will surely save time you spend on going to the bookkeeper to give him all the necessary documentation. Before you definitively decide for a certain one, it is important to know what your company needs.
If you own a business, and you use the services of a certified bookkeeper, maybe it is the right time for you to introduce some new things into your business and in that way save money and time. By using an accountant software you will surely save time you spend on going to the bookkeeper to give him all the necessary documentation. Before you definitively decide for a certain one, it is important to know what your company needs.
 Speedtest.net works in a way that it uses the transferring on big files and then measures how long it takes to transfer that file, thus telling you your bandwidth. This is pretty good, but the bad thing is that it can't measure your network latency. It also looks pretty cool.
Speedtest.net works in a way that it uses the transferring on big files and then measures how long it takes to transfer that file, thus telling you your bandwidth. This is pretty good, but the bad thing is that it can't measure your network latency. It also looks pretty cool.
 The term Web services describe a standardized way of integrating Web-based applications. Web services technology represents an important way for businesses to communicate with each other and with clients as well. Web services' distributed computing model allows application-to-application communication.
The term Web services describe a standardized way of integrating Web-based applications. Web services technology represents an important way for businesses to communicate with each other and with clients as well. Web services' distributed computing model allows application-to-application communication.
 People sometimes refer to wireless networking as "Wi-Fi", even when the network uses a completely unrelated type of wireless technology. Although it may seem ideal to all the world of wireless devices using a common network protocol, such as Wi-Fi, rather today's networks support a wide range of protocols. Reason: No protocol ensures the existence of an optimal solution for all the different wireless customs that the people want. Some are better optimized to preserve battery life on mobile devices, while others offer higher speeds and more reliable and long-distance connections.
People sometimes refer to wireless networking as "Wi-Fi", even when the network uses a completely unrelated type of wireless technology. Although it may seem ideal to all the world of wireless devices using a common network protocol, such as Wi-Fi, rather today's networks support a wide range of protocols. Reason: No protocol ensures the existence of an optimal solution for all the different wireless customs that the people want. Some are better optimized to preserve battery life on mobile devices, while others offer higher speeds and more reliable and long-distance connections.
 Bluetooth is a specification (IEEE 802.15.1) that uses low-power radio communications to connect phones, computers and other network devices over short distances without wires. The name Bluetooth is borrowed from Harald Bluetooth, King of Denmark that lived more than a 1,000 years ago.
Bluetooth is a specification (IEEE 802.15.1) that uses low-power radio communications to connect phones, computers and other network devices over short distances without wires. The name Bluetooth is borrowed from Harald Bluetooth, King of Denmark that lived more than a 1,000 years ago.
 What does a CPU do,? As the brain of your PC, the CPU allows you to operate software. And, of course, there is a connection between the power of the computer and the work of the CPU.
What does a CPU do,? As the brain of your PC, the CPU allows you to operate software. And, of course, there is a connection between the power of the computer and the work of the CPU.
 Modern metropolises can't function without computers and the Internet. Water supply and electricity, mobile and telecommunications - all function with the help of the Internet. What would happen if it terminated? If the computer network or a system server failed, that would lead to devastating consequences for people and the economy. According to some estimates Internet crime brings more profit than drug related crime. Threats from the virtual space can go much further than home computers or work place computers.
Modern metropolises can't function without computers and the Internet. Water supply and electricity, mobile and telecommunications - all function with the help of the Internet. What would happen if it terminated? If the computer network or a system server failed, that would lead to devastating consequences for people and the economy. According to some estimates Internet crime brings more profit than drug related crime. Threats from the virtual space can go much further than home computers or work place computers.
 VPN supplies network connectivity over possibly long physical distance. In this sense, VPN is a form of a wide area network (WAN). VPN allows file sharing, video conferencing and similar network services. Virtual private networks generally do not provide any new functionality that is not already offered through alternative mechanisms, but VPN applies those services more efficiently/less costing in most cases.
VPN supplies network connectivity over possibly long physical distance. In this sense, VPN is a form of a wide area network (WAN). VPN allows file sharing, video conferencing and similar network services. Virtual private networks generally do not provide any new functionality that is not already offered through alternative mechanisms, but VPN applies those services more efficiently/less costing in most cases.
 There are a lot of factors that determine the range of the connection of a wireless piece of equipment, but the main thing that affects it is the power gain of the antenna. Power gain is a numerical quantity and it is measured in dB, otherwise known as relative decibels. It stands for max effectiveness of one antenna in comparison to a different antenna. You will commonly see 2 standards that are being used by the companies who build them when they speak about measuring gain in antennas. They are dBd and dBi.
There are a lot of factors that determine the range of the connection of a wireless piece of equipment, but the main thing that affects it is the power gain of the antenna. Power gain is a numerical quantity and it is measured in dB, otherwise known as relative decibels. It stands for max effectiveness of one antenna in comparison to a different antenna. You will commonly see 2 standards that are being used by the companies who build them when they speak about measuring gain in antennas. They are dBd and dBi.
 "HART" is an acronym that is used for the name Highway Addressable Remote Transducer. In order to superimpose digital communication signals at a low level on top of the 4-20mA, this Protocol uses the Bell 202 Frequency Shift Keying (FSK) standard.
"HART" is an acronym that is used for the name Highway Addressable Remote Transducer. In order to superimpose digital communication signals at a low level on top of the 4-20mA, this Protocol uses the Bell 202 Frequency Shift Keying (FSK) standard. 
 This term was used for the first time more than 200 years ago. The coax cable was created in the 1880s, and the most common purpose was connecting TV's and antennas. But, today there is a different usage. They provide 10 Mbps Ethernet connections. The time when this kind of connection was most used was in the 80s, but now we are talking about the 20th century.
This term was used for the first time more than 200 years ago. The coax cable was created in the 1880s, and the most common purpose was connecting TV's and antennas. But, today there is a different usage. They provide 10 Mbps Ethernet connections. The time when this kind of connection was most used was in the 80s, but now we are talking about the 20th century. 
 Unlike TW trend of articles, this article is on hardware boyz and girliez. You've seen tons of people good at fixing the PC's how many really know the inner workings of thier Hard Drives (HD)? Well all you brave people who are thinking of getting your A+ Certification, be sure to get an edge over other exam candidates by learning the low down HD parts and how each part contributes to the basic workings of a HD.
Unlike TW trend of articles, this article is on hardware boyz and girliez. You've seen tons of people good at fixing the PC's how many really know the inner workings of thier Hard Drives (HD)? Well all you brave people who are thinking of getting your A+ Certification, be sure to get an edge over other exam candidates by learning the low down HD parts and how each part contributes to the basic workings of a HD.
 One of the most common questions we hear from individuals hoping to enter the IT industry is, "What programming languages do I need to know?" Obviously this is a complex question, and the answer will depend on what field the questioner is going into. Many programming languages are taught during courses used to obtain a computer information science degree. However, those already in IT know that the greatest skill you can have is to be a jack-of-all-trades. A well-prepared worker can switch between computer programming jobs with only minimal training, thanks to a wide knowledge of multiple programming languages.
One of the most common questions we hear from individuals hoping to enter the IT industry is, "What programming languages do I need to know?" Obviously this is a complex question, and the answer will depend on what field the questioner is going into. Many programming languages are taught during courses used to obtain a computer information science degree. However, those already in IT know that the greatest skill you can have is to be a jack-of-all-trades. A well-prepared worker can switch between computer programming jobs with only minimal training, thanks to a wide knowledge of multiple programming languages.
 A great deal of fundamental understanding about computers has been mostly lost from our world today. Computers are so complicated and work so reliably nowadays that many of the finer aspects of computing are now little more than dim memories in the minds of some older hackers, or little-read publications gathering dust in libraries somewhere. People often try to get away with knowing as little as they can, and while they might be able to get away with that, it's distressing how many people who believe themselves to be knowledgeable about computers are actually unaware of some highly fundamental concepts.
A great deal of fundamental understanding about computers has been mostly lost from our world today. Computers are so complicated and work so reliably nowadays that many of the finer aspects of computing are now little more than dim memories in the minds of some older hackers, or little-read publications gathering dust in libraries somewhere. People often try to get away with knowing as little as they can, and while they might be able to get away with that, it's distressing how many people who believe themselves to be knowledgeable about computers are actually unaware of some highly fundamental concepts.
 In order to do their best, candidates should know what to expect at the testing center for the Cisco CCNA certification exam. Read for more information.
In order to do their best, candidates should know what to expect at the testing center for the Cisco CCNA certification exam. Read for more information.
 There are different types of web hosting solutions nowadays. These include shared hosting, dedicated hosting, VPS hosting, among others. All these services serve the same function: hosting your content so that your website can be accessed on the Internet. However, they are different in the way they are structured as well as the benefits they some with.
There are different types of web hosting solutions nowadays. These include shared hosting, dedicated hosting, VPS hosting, among others. All these services serve the same function: hosting your content so that your website can be accessed on the Internet. However, they are different in the way they are structured as well as the benefits they some with.
 Network latency is a term used for stating the time it takes for information to travel for the sender to the recipient. It is always present, even in the smallest amounts, but that amount depends on a lot of factors. Network latency is more commonly known by the name lag.
Network latency is a term used for stating the time it takes for information to travel for the sender to the recipient. It is always present, even in the smallest amounts, but that amount depends on a lot of factors. Network latency is more commonly known by the name lag.
 Usually online gamers will use devices called lag switches. Lag switches are used to intercept the signals from the network and then cause huge delays which then affects other players in a way that is virtually impossible to play. Either way, don't play with lag switch users and everything should be fine.
Usually online gamers will use devices called lag switches. Lag switches are used to intercept the signals from the network and then cause huge delays which then affects other players in a way that is virtually impossible to play. Either way, don't play with lag switch users and everything should be fine.
.jpg) Do you want to get every computer in your home on the Internet? Do you want to share music, photo or video files stored on the computer? What do you think of stream movies? Well, you can do this and much more over the wireless networks.
Do you want to get every computer in your home on the Internet? Do you want to share music, photo or video files stored on the computer? What do you think of stream movies? Well, you can do this and much more over the wireless networks.
 How much do you really know about computers? In the computer world, there are many different levels of user knowledge; Some people believe themselves to be knowledgeable because they can clear their web browser's cache or format a floppy. Others know multiple programming languages and believe they still know very little of all there is to know. The latter group are closer to the truth; As with many other things in life, the more you know, the more you realize how little you know.
How much do you really know about computers? In the computer world, there are many different levels of user knowledge; Some people believe themselves to be knowledgeable because they can clear their web browser's cache or format a floppy. Others know multiple programming languages and believe they still know very little of all there is to know. The latter group are closer to the truth; As with many other things in life, the more you know, the more you realize how little you know.
 We've compiled a table of the most important marketing trends.
We've compiled a table of the most important marketing trends.
 This articles give the brief intro into the world of GSM and the wireless. GSM, short for Global System for Mobile Communication, is the standard behind digital mobile phones.
This articles give the brief intro into the world of GSM and the wireless. GSM, short for Global System for Mobile Communication, is the standard behind digital mobile phones.
 If you have some misconception in mind that the programming languages are easy or hard, I am afraid to say that you are mistaken. To tell you frankly about the programming languages, there is nothing such as easy or tough programming language. The only thing that you need to keep in mind while stepping into the world of programming languages is that which programming language would set your base by giving you in-depth knowledge of programming logics and the basics of programming techniques.
If you have some misconception in mind that the programming languages are easy or hard, I am afraid to say that you are mistaken. To tell you frankly about the programming languages, there is nothing such as easy or tough programming language. The only thing that you need to keep in mind while stepping into the world of programming languages is that which programming language would set your base by giving you in-depth knowledge of programming logics and the basics of programming techniques.
 The Internet is a perfect place to look up all the information you need for a winning presentation. You know you need the perfect search engine in order to get the results you're looking for. Google is that engine. It will provide all of your questions with the perfect answers, and once again you will prove your worth no matter where you settle. Google offers a great deal of information for serious and casual searchers alike. With that kind of dependability, it is easy to do the work you need to do. It doesn't matter if it's a report for school, or a new website for your internet business. Google delivers on a grand scale so you can relax and take care of business.
The Internet is a perfect place to look up all the information you need for a winning presentation. You know you need the perfect search engine in order to get the results you're looking for. Google is that engine. It will provide all of your questions with the perfect answers, and once again you will prove your worth no matter where you settle. Google offers a great deal of information for serious and casual searchers alike. With that kind of dependability, it is easy to do the work you need to do. It doesn't matter if it's a report for school, or a new website for your internet business. Google delivers on a grand scale so you can relax and take care of business.
 One famous saying says that programmers are machines that turn caffeine from coffee and Coca Cola into a programming code. And if you ask a programmer when does he like working the most and when is he most productive - he is probably going to say late at night or early in the morning, that is when he has the greatest energy and concentration to work.
One famous saying says that programmers are machines that turn caffeine from coffee and Coca Cola into a programming code. And if you ask a programmer when does he like working the most and when is he most productive - he is probably going to say late at night or early in the morning, that is when he has the greatest energy and concentration to work.
 On home or public wireless networks, your Wi-Fi connection can unexpectedly fall for no apparent reason. This kind of networking problem is particularly frustrating. It is also more common than you think. Fortunately, there are solutions. Consult this text to determine why this is happening and how to prevent it.
On home or public wireless networks, your Wi-Fi connection can unexpectedly fall for no apparent reason. This kind of networking problem is particularly frustrating. It is also more common than you think. Fortunately, there are solutions. Consult this text to determine why this is happening and how to prevent it.
 Having a connection or performance problem with your wireless network? Do you have bad or occasionally low Wi-Fi signals or poor video or audio streaming? Here we will share some tips to increase Wi-Fi performance. And most do not even require spending money.
Having a connection or performance problem with your wireless network? Do you have bad or occasionally low Wi-Fi signals or poor video or audio streaming? Here we will share some tips to increase Wi-Fi performance. And most do not even require spending money.
 The growth rate of data traffic in recent years has been an unprecedented trend in mobile communications. If consumption data in mobile networks continues to grow at the same pace, significant transformation in many aspects of the business is inevitable: the network, the business model, appliances, even users. The rapid growth of mobile broadband services and digital content (video streaming, online gaming, social networks) and sales growth of smartphones and tablet devices generate increasing traffic demands in mobile networks.
The growth rate of data traffic in recent years has been an unprecedented trend in mobile communications. If consumption data in mobile networks continues to grow at the same pace, significant transformation in many aspects of the business is inevitable: the network, the business model, appliances, even users. The rapid growth of mobile broadband services and digital content (video streaming, online gaming, social networks) and sales growth of smartphones and tablet devices generate increasing traffic demands in mobile networks.
.png) We mentioned that today smartphones and tablets are becoming the dominant devices for Internet access. Research shows that users of smartphone devices for Internet access prefer WiFi, regardless of the quality and availability of 3G/4G networks. Thus, users are increasingly turning to Wi-Fi access as an alternative to 3G access. 36% of Internet traffic today is carried out via WiFi.
We mentioned that today smartphones and tablets are becoming the dominant devices for Internet access. Research shows that users of smartphone devices for Internet access prefer WiFi, regardless of the quality and availability of 3G/4G networks. Thus, users are increasingly turning to Wi-Fi access as an alternative to 3G access. 36% of Internet traffic today is carried out via WiFi. 
 WiFi Security feature protects your network and gets quick access associated with Win2K, XP. It supports WEP or WPA and gives you real-time interloper alerts you from free blockers and you feel glad when there is no spyware and no adware in your network to spoil your files. Any users get access to the Internet by means of laptop, handhold games, smart cell phones and PDA. The most important thing is it tenders a trouble-free and cheap method to safe and sound your network connection at any hotspot all over the world. WiFi Security examines data and perceives entrance point in real time and identifies the user who wants to spoil your files.
WiFi Security feature protects your network and gets quick access associated with Win2K, XP. It supports WEP or WPA and gives you real-time interloper alerts you from free blockers and you feel glad when there is no spyware and no adware in your network to spoil your files. Any users get access to the Internet by means of laptop, handhold games, smart cell phones and PDA. The most important thing is it tenders a trouble-free and cheap method to safe and sound your network connection at any hotspot all over the world. WiFi Security examines data and perceives entrance point in real time and identifies the user who wants to spoil your files.
 Wikileaks has been in the news for quite some time now as it has rocked many nations, embroiling itself in controversy over the fact that it has been releasing classified documents which have been termed as potentially harmful for national security as well as international diplomacy. Amidst all the confusion related to it's ethical and moral standards, people around the world have also speculated how the site functions technically, as a site which has been so controversial, might be technologically sound as well because various steps have already been taken in order to shut the Website down but none of them have availed any results.
Wikileaks has been in the news for quite some time now as it has rocked many nations, embroiling itself in controversy over the fact that it has been releasing classified documents which have been termed as potentially harmful for national security as well as international diplomacy. Amidst all the confusion related to it's ethical and moral standards, people around the world have also speculated how the site functions technically, as a site which has been so controversial, might be technologically sound as well because various steps have already been taken in order to shut the Website down but none of them have availed any results.
 By now most Windows users are probably familiar with the notion of user accounts and how all users on a PC can have their own individual settings, documents, and other features. In Windows Vista, Microsoft simplified the user account types down to just two, and locked them down to make the system more secure. Windows 7 takes this approach a step further and makes it easier to configure how user accounts behave and are protected. And thanks to features such as User Account Control, Parental Controls, and Windows Live Family Safety, Windows 7 is not only more secure than previous Windows versions, but also easier to configure from a user account perspective. This tutorial describes these features and explains how they can be put to the best possible use.
By now most Windows users are probably familiar with the notion of user accounts and how all users on a PC can have their own individual settings, documents, and other features. In Windows Vista, Microsoft simplified the user account types down to just two, and locked them down to make the system more secure. Windows 7 takes this approach a step further and makes it easier to configure how user accounts behave and are protected. And thanks to features such as User Account Control, Parental Controls, and Windows Live Family Safety, Windows 7 is not only more secure than previous Windows versions, but also easier to configure from a user account perspective. This tutorial describes these features and explains how they can be put to the best possible use.
 With Windows 7, Microsoft expands on the pervasive and reliable backup and restore solutions for both data files and the entire computer that it introduced in Windows Vista. You can use Windows Backup to copy your important files and folders to a safe location or create a system image that can be used later to restore a broken PC. There's even a cool new feature that debuted first in Windows Server that helps you recover old versions of data files if you save the wrong version. Windows 7 has everything you need to make sure your data is safe.
With Windows 7, Microsoft expands on the pervasive and reliable backup and restore solutions for both data files and the entire computer that it introduced in Windows Vista. You can use Windows Backup to copy your important files and folders to a safe location or create a system image that can be used later to restore a broken PC. There's even a cool new feature that debuted first in Windows Server that helps you recover old versions of data files if you save the wrong version. Windows 7 has everything you need to make sure your data is safe.

 Windows 8 is with us for a while, and we don't have any doubt that some users have already installed it on their computer as the only operating system. As it usually happens on every new version of Windows coming out there are a lot of differences between the older Windows and the new ones, users don't know all the possibilities that the new Windows offers. That is why we gathered some useful advice on that theme here.
Windows 8 is with us for a while, and we don't have any doubt that some users have already installed it on their computer as the only operating system. As it usually happens on every new version of Windows coming out there are a lot of differences between the older Windows and the new ones, users don't know all the possibilities that the new Windows offers. That is why we gathered some useful advice on that theme here.
 The public is buzzing about the latest release of Windows 8. This release contains over 300 new features that are sure to please. While it is just in preview mode for developers only, the intention is to keep tweaking this version of Windows until it is perfect. Microsoft makes big promises that this version will be bigger and better than before, but just what is so great about this version of Windows? For starters, Windows 8 can be used on both PC's and ARM tablets. Because of new capabilities that include the touch screen ability, Windows 8 can be used on laptops, tablets, even the screens that require high def.
The public is buzzing about the latest release of Windows 8. This release contains over 300 new features that are sure to please. While it is just in preview mode for developers only, the intention is to keep tweaking this version of Windows until it is perfect. Microsoft makes big promises that this version will be bigger and better than before, but just what is so great about this version of Windows? For starters, Windows 8 can be used on both PC's and ARM tablets. Because of new capabilities that include the touch screen ability, Windows 8 can be used on laptops, tablets, even the screens that require high def.
 Keyboard shortcuts for Windows Explorer. Expand the current selection if it is collapsed or Select the first subfolder - RIGHT ARROW. And many more.
Keyboard shortcuts for Windows Explorer. Expand the current selection if it is collapsed or Select the first subfolder - RIGHT ARROW. And many more.
 These tips are provided as-is, with no warranty, either implied or otherwise. These tips do not include a thorough explanation of why you may want to use them, or why it might be a good idea not to. They are strictly meant to be a listing of registry tips and tweaks that I have collected over the years. Feel free to send me corrections or clarifications to us through our contact page.
These tips are provided as-is, with no warranty, either implied or otherwise. These tips do not include a thorough explanation of why you may want to use them, or why it might be a good idea not to. They are strictly meant to be a listing of registry tips and tweaks that I have collected over the years. Feel free to send me corrections or clarifications to us through our contact page.
 No matter what the public thinks, manufacturers rushed to get Windows 8 certificates for their devices. One of the first ones who came in our hands was the Kingston USB 3.0 flash disk called the DataTraveler Workspace. At first glance it looks completely logical that every USB transportable memory works on the Windows 8 operating system, but the Workspace actually is not the common transportable disk.
No matter what the public thinks, manufacturers rushed to get Windows 8 certificates for their devices. One of the first ones who came in our hands was the Kingston USB 3.0 flash disk called the DataTraveler Workspace. At first glance it looks completely logical that every USB transportable memory works on the Windows 8 operating system, but the Workspace actually is not the common transportable disk.
 Windows NT is generally regarded among IT (information technology) professionals as the most stable and secure Windows OS (operating system). Win2000 and WinXP Pro work well in a peer-to-peer network, but these OSes are designed to handle client/server networking, where in multiple clients (computers, or workstations) connect to one or more servers (computers that control the network's software and each client's access to other parts of the network).
Windows NT is generally regarded among IT (information technology) professionals as the most stable and secure Windows OS (operating system). Win2000 and WinXP Pro work well in a peer-to-peer network, but these OSes are designed to handle client/server networking, where in multiple clients (computers, or workstations) connect to one or more servers (computers that control the network's software and each client's access to other parts of the network). 
.gif) Wireless networking is a wireless communication, but as a way to get a computer with a wireless card connected to the SOHO device that allows wireless communication (not to all devices) and become a full member of the local network. SOHO device works as a wireless access point (WAP - Wireless Access Point). In today's rules, all laptops have this feature built-in antenna and they are incorporated in the monitor frame.
Wireless networking is a wireless communication, but as a way to get a computer with a wireless card connected to the SOHO device that allows wireless communication (not to all devices) and become a full member of the local network. SOHO device works as a wireless access point (WAP - Wireless Access Point). In today's rules, all laptops have this feature built-in antenna and they are incorporated in the monitor frame. 
 We are bothered that there is no start button in the Windows 8 - we are looking for a way to return it. The Metro Start screen terrifies us and we don't know what do with it - we are looking for a way to avoid it and go directly to the desktop. To transfer the part of the functionality of the Metro interface in older versions of Windows? That sounds like a good idea for an experiment, and with the help of the newest product of the Iobit company - the WinMetro, we will do it.
We are bothered that there is no start button in the Windows 8 - we are looking for a way to return it. The Metro Start screen terrifies us and we don't know what do with it - we are looking for a way to avoid it and go directly to the desktop. To transfer the part of the functionality of the Metro interface in older versions of Windows? That sounds like a good idea for an experiment, and with the help of the newest product of the Iobit company - the WinMetro, we will do it.
 If it is not the best, Winstep Nexus certainly is placed in the top three places that currently exist on the market. Not only is it a configurable solution that look really beautiful and refreshes the work surface, but it is a program with a lot of function.
If it is not the best, Winstep Nexus certainly is placed in the top three places that currently exist on the market. Not only is it a configurable solution that look really beautiful and refreshes the work surface, but it is a program with a lot of function.
 With the Internet there came a whole new era of information technology, transfer and access. Also, the Internet connected the world in a way that has never been see before, through games. Alongside the Internet came huge amounts of brand new games, genres, software and a lot of other things. And also the Internet seems to be getting faster as we go into the future.
With the Internet there came a whole new era of information technology, transfer and access. Also, the Internet connected the world in a way that has never been see before, through games. Alongside the Internet came huge amounts of brand new games, genres, software and a lot of other things. And also the Internet seems to be getting faster as we go into the future.
 In the last article we have talked about the wired experience and all the pros and cons when it comes to speed, reliability and all the other things you need to enjoy playing video games on the web. In this text we are going to take a different approach and talk about wireless connections and everything that there is to know about them.
In the last article we have talked about the wired experience and all the pros and cons when it comes to speed, reliability and all the other things you need to enjoy playing video games on the web. In this text we are going to take a different approach and talk about wireless connections and everything that there is to know about them.
 WAP stands for Wireless Application Protocol, a secure specification that allows users to access information instantly via handheld wireless devices such as mobile phones, pagers, two-way radios, smartphones and communicators. WAP is supported by all operating systems. Ones specifically engineered for handheld devices include Palm OS, EPOC, Windows CE, FLEXOS, OS/9, and Java OS.
WAP stands for Wireless Application Protocol, a secure specification that allows users to access information instantly via handheld wireless devices such as mobile phones, pagers, two-way radios, smartphones and communicators. WAP is supported by all operating systems. Ones specifically engineered for handheld devices include Palm OS, EPOC, Windows CE, FLEXOS, OS/9, and Java OS.
 A long time ago there were problems with home automation because networks had a huge limitation about how much they could stretch. There were huge problems with wiring and differences in that wiring and that implied the use of phase couplers in order to bridge the signals. If you lived in a big house you would need long cables which then brought slow connections and problems with performance.
A long time ago there were problems with home automation because networks had a huge limitation about how much they could stretch. There were huge problems with wiring and differences in that wiring and that implied the use of phase couplers in order to bridge the signals. If you lived in a big house you would need long cables which then brought slow connections and problems with performance.
 The way networks work is that they use adapters to connect to hotspots. If you have a newer generation computer it will have a built in one but older ones don't have them. You can buy these adapters in stores. There are all sorts of adapter types like USB, PCI card and many more.
The way networks work is that they use adapters to connect to hotspots. If you have a newer generation computer it will have a built in one but older ones don't have them. You can buy these adapters in stores. There are all sorts of adapter types like USB, PCI card and many more.
 Ever wonder if it's a good idea to switch your home LAN to wireless? This is a very easy to understand discussion about the security matters involved.
Ever wonder if it's a good idea to switch your home LAN to wireless? This is a very easy to understand discussion about the security matters involved.
 If you are a home network owner or perhaps a business network owner you are probably seeking to purchase WLAN (wireless local area network) devices and gear. There are a lot of devices and products that fit into the common wireless standard. They are also known as Wi-Fi technologies and the most common are 802.11a, 802.11b and 802.11g. In this text we will compare those standards and tell you the pros and cons of each one of them.
If you are a home network owner or perhaps a business network owner you are probably seeking to purchase WLAN (wireless local area network) devices and gear. There are a lot of devices and products that fit into the common wireless standard. They are also known as Wi-Fi technologies and the most common are 802.11a, 802.11b and 802.11g. In this text we will compare those standards and tell you the pros and cons of each one of them.
 Get the hands on with Wireless Markup Language with WML tutorial. WML is a 'markup' language. This means that WML pages are written and saved as text files, using 'tags' like those found in HTML. Anyone familiar with HTML should find learning WML fairly easy
Get the hands on with Wireless Markup Language with WML tutorial. WML is a 'markup' language. This means that WML pages are written and saved as text files, using 'tags' like those found in HTML. Anyone familiar with HTML should find learning WML fairly easy
 In the following article we are going to talk about Ligatures and OpenType typography in Word. While you can explore the Advanced properties and OpenType font behavior with the Font window opened, watch out for the ligatures that show up in the second appearance of the word Office on the image...
In the following article we are going to talk about Ligatures and OpenType typography in Word. While you can explore the Advanced properties and OpenType font behavior with the Font window opened, watch out for the ligatures that show up in the second appearance of the word Office on the image...
.png) Today we are going to talk about a few things in Word, the Quick Access Toolbar, Letter addressing and Turning on the ruler. Do you use the Quick Access Toolbar? Word 2010 puts it discretely on the title bar, right from the Office key in the top left corner of the window. In it are the default keys...
Today we are going to talk about a few things in Word, the Quick Access Toolbar, Letter addressing and Turning on the ruler. Do you use the Quick Access Toolbar? Word 2010 puts it discretely on the title bar, right from the Office key in the top left corner of the window. In it are the default keys...
 This article reveals the inner workings of the Data Warehousing. This is a must any web hosting people out there and also for database people. Don't forget, data is the heart of all the IT industries.
This article reveals the inner workings of the Data Warehousing. This is a must any web hosting people out there and also for database people. Don't forget, data is the heart of all the IT industries.
 Modern technology has made it greatly easier to do everyday tasks, it enabled us to always be available, but also that we can communicate with everyone at every moment. But, modern technology has brought some habits with it that are not very good for our devices or for our social life.
Modern technology has made it greatly easier to do everyday tasks, it enabled us to always be available, but also that we can communicate with everyone at every moment. But, modern technology has brought some habits with it that are not very good for our devices or for our social life.
 It is true that remembering different password can be difficult, but once when you come up with your system, it will be much easier. Pick a phrase that will be your basis and for every page add something characteristic to that page. For example, if your base is AcM3 and you add 8F8 to that for Facebook, it will be easy to remember and almost impossible to hack.
It is true that remembering different password can be difficult, but once when you come up with your system, it will be much easier. Pick a phrase that will be your basis and for every page add something characteristic to that page. For example, if your base is AcM3 and you add 8F8 to that for Facebook, it will be easy to remember and almost impossible to hack.
 Very informal thoughts on WYSIWYG HTML editors like DreamWeaver and MS Frontpage and the likes.
Very informal thoughts on WYSIWYG HTML editors like DreamWeaver and MS Frontpage and the likes.
 Here is a short and to the point method of learning the naming convention of XML Elements. XML elements must follow these naming rules: mames can contain letters, numbers, and other characters, names must not start with a number or...
Here is a short and to the point method of learning the naming convention of XML Elements. XML elements must follow these naming rules: mames can contain letters, numbers, and other characters, names must not start with a number or...
 This would be a helpful article for those of you looking to get into XML. Its a sure head-starter. XML stands for (Extensible Markup Language)which is a simplified subset of the Standard Generalized Markup Language (SGML). XML is a markup language for documents containing structured information.
This would be a helpful article for those of you looking to get into XML. Its a sure head-starter. XML stands for (Extensible Markup Language)which is a simplified subset of the Standard Generalized Markup Language (SGML). XML is a markup language for documents containing structured information. 

How come I was ranking on page one yesterday and I am not today?
If you've checked your rankings in the search engines today, only to find that your site is not listed on the first page, your first instinct or your gut reaction might be to panic. If you have an SEO company running your campaign for you, then your next action will probably be to call them and ask them what is going on and why they aren't doing their jobs properly. This is a common question that many an SEO company would receive in their day to day operations, and such a rankings drop is a common occurrence within the SEO industry.

 This article will get you going in creating your first webpage solely created by HTML. All you need in a "NOTEPAD" program.
This article will get you going in creating your first webpage solely created by HTML. All you need in a "NOTEPAD" program.
.jpg) If you have a wireless network and you have some problems with your connection, or you are just seeking knowledge about how that signal works, this is just the place where you should be. Read this text and find out something more about wireless and Wi-Fi signal strength.
If you have a wireless network and you have some problems with your connection, or you are just seeking knowledge about how that signal works, this is just the place where you should be. Read this text and find out something more about wireless and Wi-Fi signal strength.
 No matter how good Apples iPad tablet PC is, anyone who has ever owned it knows that it's very difficult to write long lines of text on it's keyboard. Apple has enabled tablet to keyboard Bluetooth connection, but the biggest problem is, except for budget, the amount of hardware is increased and practicality is decreased. Some manufacturers are trying to solve that problem by making smaller keyboards, but those solutions have been just good, not great. Until the appearance of the ZaggMate.
No matter how good Apples iPad tablet PC is, anyone who has ever owned it knows that it's very difficult to write long lines of text on it's keyboard. Apple has enabled tablet to keyboard Bluetooth connection, but the biggest problem is, except for budget, the amount of hardware is increased and practicality is decreased. Some manufacturers are trying to solve that problem by making smaller keyboards, but those solutions have been just good, not great. Until the appearance of the ZaggMate.
|
|
|||



